The data below is taken from the 2021 State of IBM i Security Study, which provides compelling insight into the security posture of 247 IBM i servers and partitions—systems that are often used for business-critical data, payment card data, and personally identifiable information (PII). The full study can be accessed here.
The traditional IBM i library and object infrastructure is considered highly virus-resistant, but other file structures within the Integrated File System (IFS) are susceptible to hosting infected files, which can then be propagated throughout the network. Recognizing this reality, IBM created system values and registry exit points to support native virus scanning a number of years ago.
One business scanned IBM i for viruses for the first time and was shocked to find nearly 250,000 infected files. If anyone doubted the need for virus protection, this example proves the risk is real. Scanning IBM i for viruses and malware is becoming increasingly popular as administrators start to recognize that IBM i contains file systems that are not immune to infection and, under certain circumstances, native applications and even IBM i itself can be impacted.
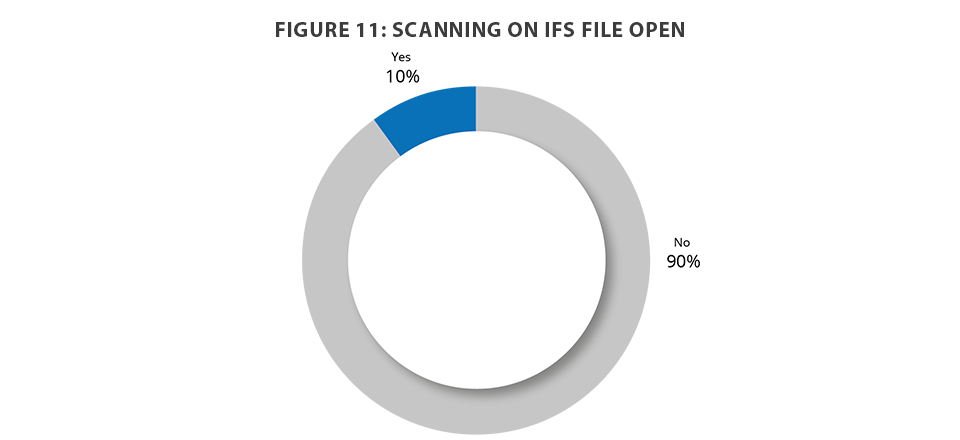
When the servers were reviewed for antivirus controls, 10 percent were scanning on file open, which is a noticeable increase over prior years. This means the other 90 percent are at risk of having internal objects impacted or of spreading an infection to another server in their network (Figure 11).
Pro Tip: Register QIBM_QP0L_SCAN_OPEN and QIBM_QPWFS_FILE_SERV
Register an exit program to exit point QIBM_QP0L_SCAN_OPEN to intercept file open attempts from the network and scan files before they are opened. This prevents viruses from spreading outside the IBM i environment.
Install an antivirus solution that runs natively on IBM i, such as Powertech Antivirus for IBM i, to detect and remove infections, as well as prevent malware from spreading beyond the current environment.
In addition, utilizing an exit program registered to the QIBM_QPWFS_FILE_SERV exit point can help limit actions of remote viruses operating on other servers on the network.
Read the Full Report
Get the latest data around IBM i security and find out how you can close security gaps on your systems. Download the latest State of IBM i Security Study.