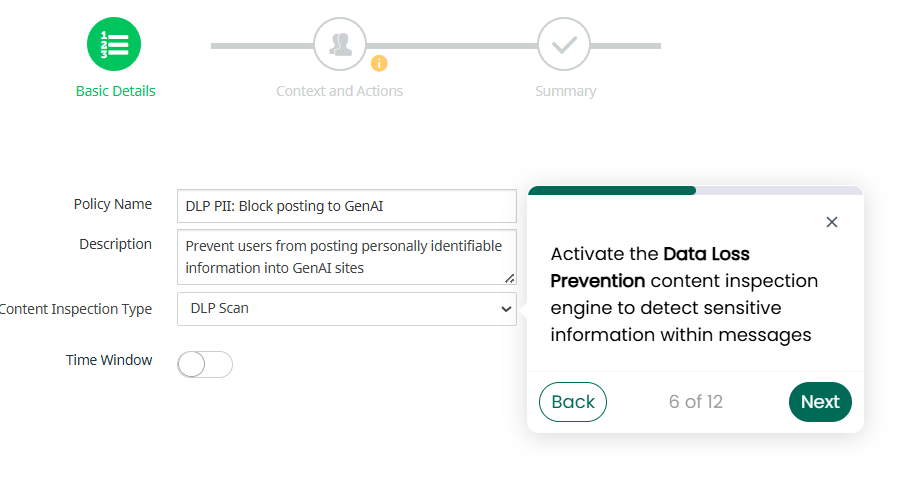
As GenAI accelerates data creation and shadow IT expands beyond security’s visibility, protecting sensitive information is becoming more complex.
Organizations must know where their data lives — across cloud environments, SaaS applications, and on-premises systems — along with the ability to discover, classify, and protect it with policy-driven controls that enable secure AI adoption and reduce risk from unsanctioned tools.
Where Trusted Brands Turn for Data Security
Data Protection Solutions from Fortra
Organizations rely on sensitive data to serve customers, drive innovation, and grow. Security leaders need visibility into that data, protection against loss or theft, and safe ways to share it beyond the enterprise.
Fortra’s data protection solutions deliver layered, adaptable security for every cybersecurity maturity level. Our modular solutions meet immediate needs, safeguard critical data, and guide the next steps as your security program evolves.

Discover how Fortra’s interlocking data security solutions protect sensitive data while keeping users productive.
Ready to Get Started?
Take another tour and see how to assess data risk, identify data repositories, and safeguard sensitive information.