Passwords are a critical IBM i (AS/400) security issue because they represent the most obvious—and most easily exploited—method to compromise your system.
Without proper password security measures in place, efforts to secure other areas of an IBM i network are largely ineffective. How can you be sure that the user signed on is the same user that the ID and password were assigned to?
Keep reading to learn how many IBM i users rely on default passwords despite the risks and how you can close this security gap on your system.
Why are IBM i default passwords so risky?
On IBM i, profiles that have a default password have a password that’s the same as the user name. Because this is the default when new user profiles are created, it is a particularly high-risk factor for IBM i servers.
Many companies have policies to name their user accounts or profiles based on a standard format, such as first name initial followed by surname (for example, jsmith or tjones). A hacker can guess profile names like jsmith and try default passwords. It’s even easier for an employee who understands the internal convention for user profile names to guess account names and try default passwords, especially if they are aware of accounts that have been created but not yet used.
Regulatory and legislative standards typically mandate that users must utilize unique credentials known only to the user, ensuring that any actions can be tied to that specific individual. Organizations might struggle to prosecute illegal or unauthorized activity if it became evident that the credentials couldn’t unequivocally identify the culprit. This prevalence of default passwords means guessing a password becomes an incredibly simple task and this ultimately translates into a compliance failing.
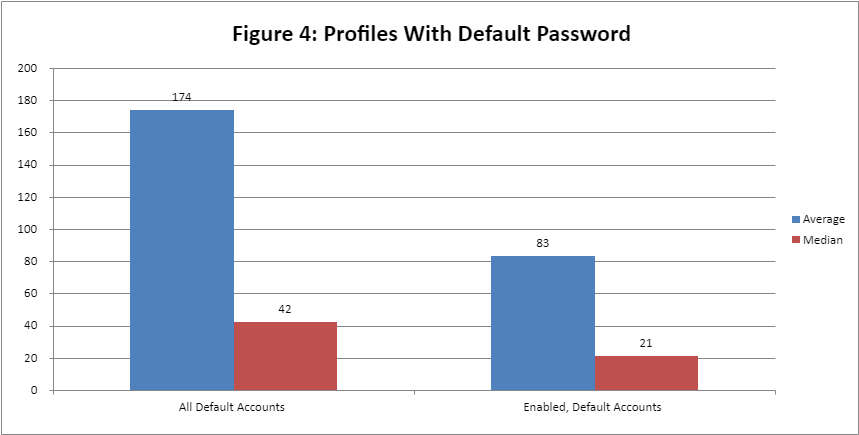
The data on default passwords
The annual State of IBM i Security Study analyzes how many system users continue to leverage default passwords. The latest data shows nearly 15 percent of user profiles have default passwords (Figure 4). 44 percent of the systems studied have more than 30 user profiles—25 percent have more than 100 user profiles—with default passwords. One system has a total of 5,604 user profiles with default passwords and over two thousand were in an enabled state.
Use QPWDRULES System Value to Ban Default Passwords
Establish and enforce password policies that make it difficult to compromise a user’s account. As of V7.2, IBM i supports the banning of default passwords via the QPWDRULES system value, although consideration must be given to applications or vendor software that creates profiles during installation.
Reporting tools like Powertech Compliance Monitor make it easy to generate audit reports on a regular basis that compare IBM i user and password information against policy.
Download the State of IBM i Security Study
Get the data on other IBM i security vulnerabilities, along with expert tips on how to protect your systems. Download the complete State of IBM i Security Study today.