Powertech Encryption for IBM i includes an advanced Key Management system which resides natively on IBM i. This Key Management system is seamlessly integrated with Powertech Encryption’s policy controls, encryption functions and auditing facilities to provide a comprehensive data protection solution.
Together with the integrated security on IBM i, organizations can strictly control access to key maintenance and usage activities to meet stringent compliance requirements such as PCI DSS. The encryption keys can either reside on the same IBM i system or partition as the data or can be managed and stored on a different system or partition.
Secure IBM i Encryption Keys
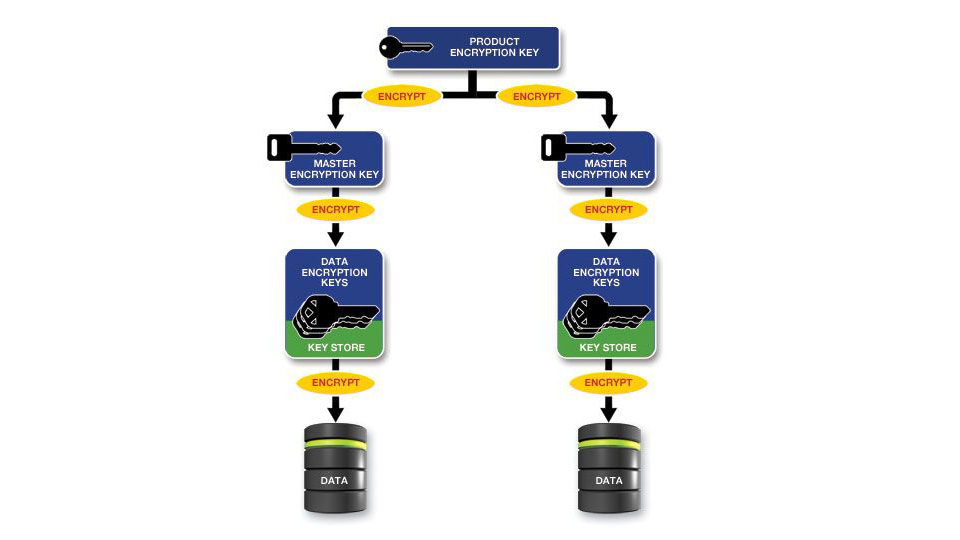
Powertech Encryption provides a secure multi-level architecture to protect data encryption keys on IBM i.
Key Features
Policy Settings
Strong Key Values
User-Based Authorization
Integration Options
Secure Interfaces
Key Protection
Dual Control
Key Stores
Auditing
Get Started with IBM i Encryption
Find out how strong encryption, tokenization, integrated key management and auditing can help protect your sensitive IBM i data and meet compliance regulations. Request a free demo today.