Remember the MasterCard commercials from a few years ago? In my mind, I see one of them going like this:
- State-of-the-art, 64-bit, multi-core Power7 hardware: $225,000
- Highly securable IBM i operating system: $100,000
- Discovering you can generate and distribute audit reports automatically: PRICELESS
This joke probably isn’t too funny to anyone who’s responsible for generating audit reports from IBM i. Despite the server’s incredible security infrastructure, auditing remains primarily a thankless, manual chore. And, let’s face it, any task that’s thankless and manual probably won’t get done. Even with a commercial audit tool, a user must decide what reports to run, and then compile and interpret the results.
A Basic Audit Scenario
A common report request from auditors is for a list of the powerful users on the system. Your first question is likely to be “what is a powerful user?” Unfortunately, there’s no official auditor’s dictionary (wouldn’t that be nice!)—each auditor has different criteria.
Maybe you can omit IBM-supplied profiles, disabled profiles that haven’t signed on for at least 45 days, and any profiles without a password. They’ll ask for each of those reports separately. Then, don’t forget to include the users from all 15 production IBM i partitions, preferably on a single report so it’s easier to process.
Here’s one way to accomplish this task:
Step 1: Run IBM’s user profile report (PRTUSRPRF) to dump the configuration data for ALL defined users. Print a hard copy of the report, or figure out how to use Navigator for i to download it to your PC.
Step 2: Manually review each user profile to see if it meets the auditor’s criteria—and hope you don’t have too many profiles to deal with! Don’t forget special authorities of the sixteen possible group profiles the user might belong to in case any authority is inherited. Oh, and the report doesn’t include the number of days since prior sign-on, so you’ll have to determine what the date was 45 days ago, and check that manually. And, you’ll also have to manually exclude the “known” users from the report each time.
Step 3: Document the name of the users that remain.
Step 4: Return to Step 1 and repeat for the next server.
Step 5: Aggregate the results into a single report (somehow) and distribute it to the auditor (somehow) in a secure manner.
Step 6: Prepare to prove to the auditor that the information hasn’t been tampered with (since you’re likely to be one of those powerful users). Also, expect to be asked for a lot more than one simple report.
This is a fictitious scenario, but it’s not unrealistic. It doesn’t take very long to realize that the process is tedious, time-consuming, and expensive; not to mention error-prone and arguably considered self-policing.
A Basic Audit Scenario (Revised)
Powertech Compliance Monitor for IBM i has the reports you need. Powerful (and modifiable) filters you can apply to the data make child’s play out of creating custom audit reports. And, its assessment scheduling and distribution function allows you to run reports at regular intervals across multiple systems and distribute them on completion.
Let’s take another look at that scenario using Compliance Monitor for IBM i:
Step 1: Point and click to select the systems to assess.
Step 2: Point and click to select from the hundreds of available reports.
Step 3: Specify the run schedule (optional) and distribution requirements.
Step 4: Sit back and relax.
You can send the reports automatically via email as individual files, or bundled into a password-protected (and encrypted) zip file. Report files can be editable, or PDFs that are digitally signed to reassure auditors that the information hasn’t been tampered with. If you prefer, you can place the reports in the IFS for the user to access.
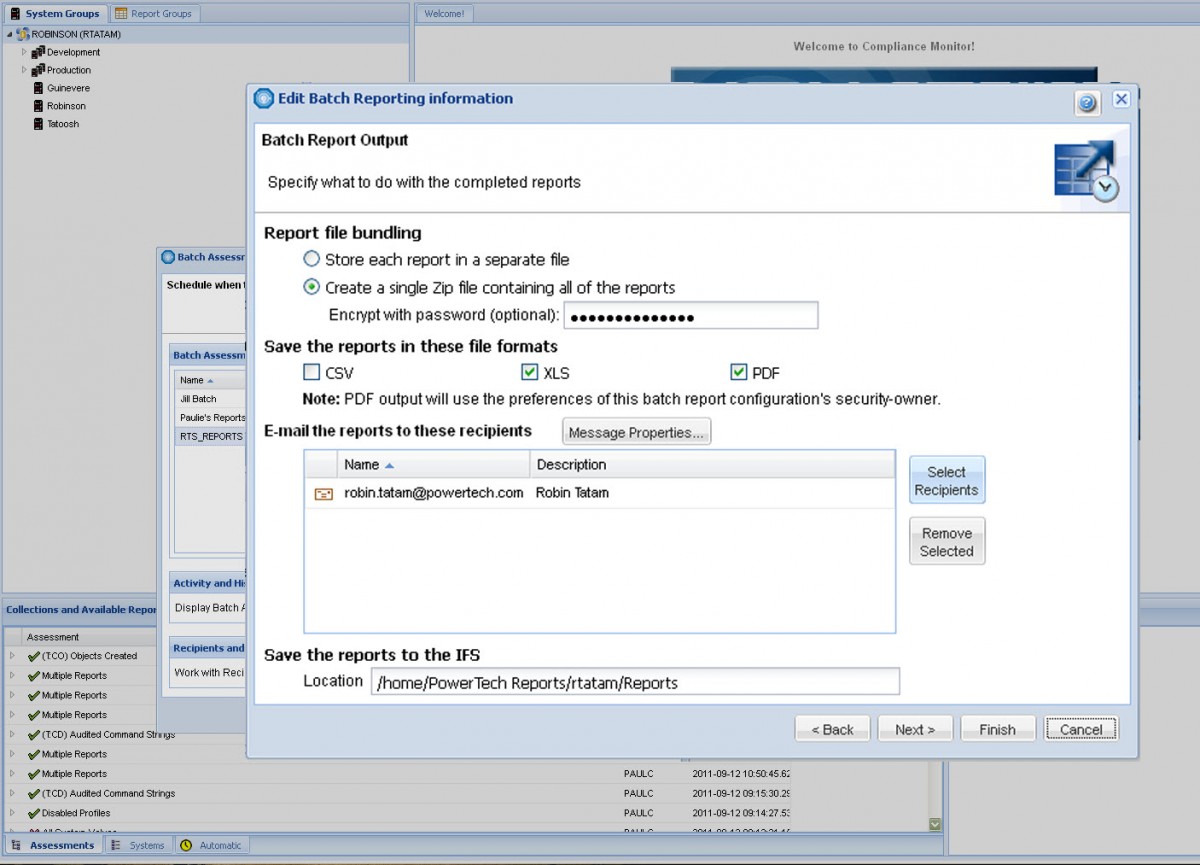
Compliance Monitor for IBM I offers batch scheduling and email distribution of audit reports.
Compliance Monitor for IBM i eliminates the burden of audit reporting. Its hundreds of report options give visibility to static information, such as user profiles and system values, as well as dynamic events recorded into the security audit journal, QAUDJRN. Priceless—YES!