As threat actors become more proficient, sophisticated, and effective, organizations often turn to point-products as a solution. The result is dozens of tools that lack cohesive visibility across an environment, an inability to correlate the disparate data sources to develop actionable insights and, ultimately, not achieving the security outcomes needed to address ever-present threats.
With tightening budgets, security skills shortages, and a focus on improved security posture, it’s no surprise security leaders seek more scalable, sustainable, comprehensive, 24/7 detection and response solutions.
Integrate Your IBM i Logging and XDR
For customers running critical business applications on IBM i, Fortra Extended Detection and Response (XDR) seamlessly ingests and processes log data from the IBM i, including QAUDJRN and QSYSOPR entries — all enabled by the Powertech SIEM Agent for IBM i. This allows security teams to monitor events from IBM i and other operating systems within one centralized dashboard, reducing the likelihood that a critical IBM i security event goes unnoticed while minimizing IT’s workload.
Key Benefits
Comprehensive Coverage and Visibility
Fortra XDR offers complete visibility into all security events spanning an organization’s entire IT estate. This includes endpoints, networks, cloud, and third-party vendors and sources. Combined with industry-leading managed detection and response (MDR) and a lightweight Fortra agent uniquely designed to target endpoint telemetry, Fortra XDR makes gathering and acting on security insights as easy and effective as possible.
Centralized Management
Fortra XDR and Powertech SIEM Agent allow cybersecurity and operations teams to host all critical security messages in a centralized location. This eliminates any duplication of detection and response efforts and reduces the likelihood of a threat going unnoticed.
Tool Integrations
Fortra XDR and Powertech SIEM Agent integrate with existing tools like endpoint detection and response, identity management, and IBM i job scheduling solutions to multiply the value of your existing investments while fortifying your security strategy, technology, and expertise.
Protection from Known and Unknown Threats
Fortra XDR identifies known threats by leveraging threat intelligence from the Fortra Threat Brain in its analysis of thousands of data points and a broad range of telemetry sources. Deep analytics, machine learning, and powerful search functions enable analysts to identify unknown and emerging threats.
Improve Efficiency and Time to Response
Organizations can gain efficiency with our automated response by streamlining repetitive response tasks such as host isolation. Our technology is augmented by our SOC team, whereby verified malicious actions detected on the endpoint will result in SOC-deployed response actions on behalf of the customer.
Overcome Staff Shortages with a 24/7 Managed Service
Delivered as a managed solution, Fortra XDR safeguards your business-critical assets with 24/7 threat detection and incident management, delivered by a global SOC with more than 120 experts in security and information technology disciplines.
Our security operations teams leverage threat intelligence to perform tasks such as incident triage, threat hunting, security investigations, and tuning. Backed by a 15-minute escalation SLA, our managed XDR solution provides continuous monitoring and security expertise, providing you with peace of mind.
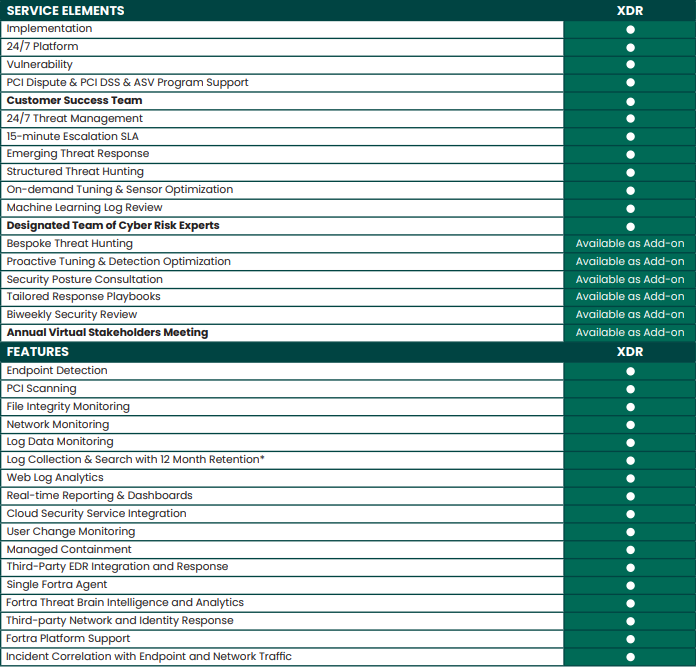
Features and Capabilities
Detection
- Agent-based scanning
- File integrity monitoring
- Network traffic inspection
- Log collection
- Application attacks
- Credential attacks
- Lateral movement
- Command and control communication
- OS events, including file, system, host, process, and network activity
- File-based attacks (e.g., malware)
- Fileless attacks (e.g., PowerShell or registry)
- File download and origination
- Multi-stage attacks
- User behavior analysis
- Anomaly detection
- Threat scoring and prioritization
- System scanner and events (user, data, system, command line)
- Third-party integrations
- Cloud service integrations
- Collection of forensic evidence such as web history, event logs, and suspicious files on demand
- Utilize MITRE-aligned rules to identify suspicious activity
Response
Supports third-party and native response actions for:
- Identity management providers
- Firewalls
- Web application firewalls (WAF)
- Endpoint detection and response (EDR)
Response actions:
- Isolate endpoint from network
- Disable user credentials
- Reset user session
- Force password reset
- Remove MFA devices
- Shun malicious connections
Use Cases:
- Block reconnaissance attempts
- Block application attacks
- Quarantine compromised accounts
- Reset compromised accounts
- Prevent infection spread
- Limit malware and ransomware
- Block command and control traffic
Ready to Get Started with Fortra's XDR for IBM i?
Contact us to have a Fortra representative reach out to you with more information.