“If you fail to plan, you are planning to fail.”
This adage is still around because it’s true—especially when it comes to cybersecurity. And this is why it’s so surprising to see that many IBM i aren't planning to implement key security controls.
Keep reading to find out where security plans are running off course and how you can make a completely attainable plan to succeed.
For the ninth year in a row, cybersecurity is the top concern for IT professionals who took the IBM i Marketplace Survey. This makes perfect sense, considering how many data breaches have made headlines and how cybersecurity has become part of the public discourse. But the next survey question was quite surprising.
The next question asked, “Which security solutions do you have in place or plan to put in place across your IBM i servers?” Eight options were listed, and survey takers could indicate whether they had the solutions in place already, planned to implement them, or had no plans to implement them.
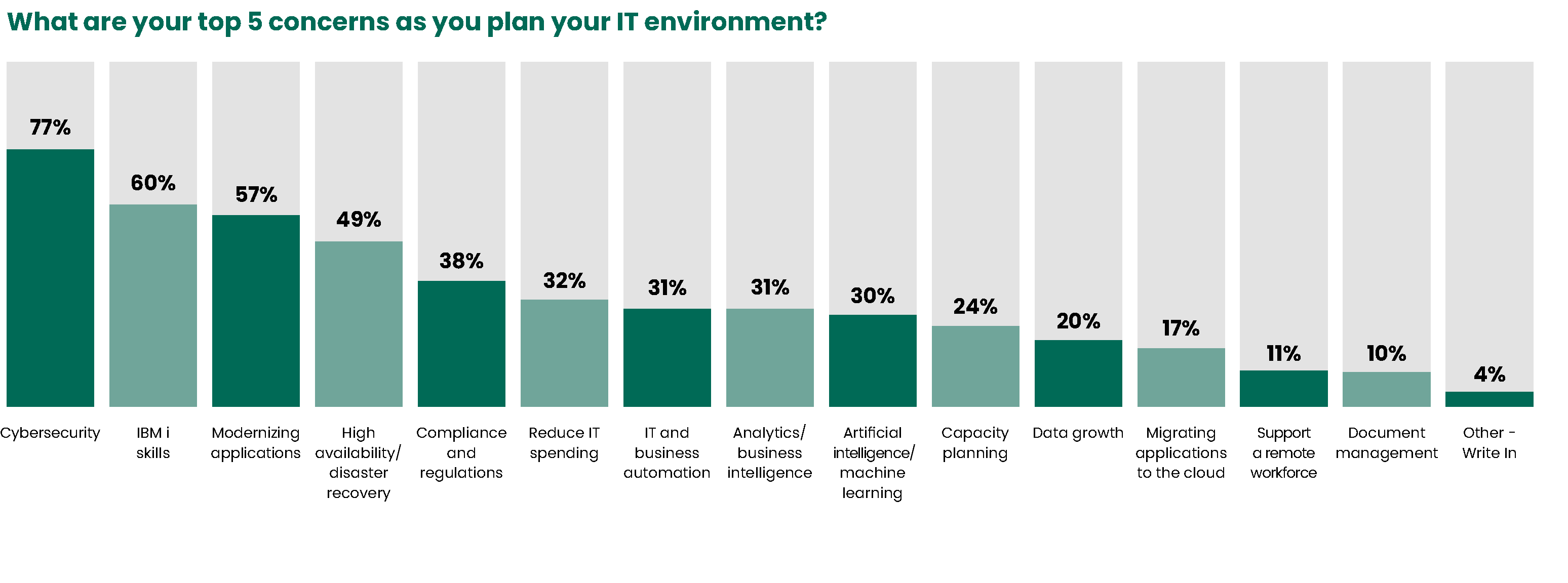
Despite the increased focus cybersecurity and data protection around the world, many IBM i pros say their organizations have no plans to implement key security solutions:
- Sixty percent have no plans to implement antivirus protection
- Forty-six percent have no plans to implement exit point security
- Seventy-four percent have no plans to implement database encryption
We know that at most organizations, it’s not feasible to implement multiple solutions at once. But this lack of planning is concerning, considering how critical the IBM i operating system is to the organizations that run it.
Ransomware Is Avoidable
Malicious programs like malware, ransomware, and viruses have consistently made headlines in recent years. On top of that, cryptocurrency miners have targeted servers and PCs with malware. A malware attack can derail critical IT projects and cause downtime that costs your organization hundreds of thousands of dollars—or more.
Many IBM i professionals are just beginning to understand how malware can attack their systems through the IFS. The risk is real and the damage could be extensive (and expensive!). The good news is that malware infections are avoidable. Powertech Antivirus is server-level protection built specifically for the IBM i OS, and you can get a free trial to find out if you already have infected files in your systems.
Prevent Unauthorized Access
On IBM i, exit points are another area of cybersecurity that’s not well understood. IBM added exit points to IBM i to allow data to be access from other platforms like users’ PCs. Exit programs can be installed on exit points to monitor and control access to IBM i data. Without exit programs, many users could have untraceable access to sensitive data.
IBM i has 27 exit points. The latest State of IBM i Security Study shows that just 58% of systems have one or more exit programs in place. That leaves a lot of unsecured exit points out there, and the IBM i Marketplace Survey shows that more than half of all survey takers have no plans to implement exit point security.
Unsecured exit points could result in exposed or corrupted data and fines for compliance violations. For most organizations, exit programs are the low-hanging fruit of IBM i security. To know for sure how to prioritize exit point controls in your IBM i security plan, get a risk assessment. Fortra offers a free IBM i Security Scan that will show you whether your exit points are vulnerable.
Data Encryption: Your Last Line of Defense
Thanks to many high-profile data breaches, encryption has become a larger part of the security conversation than it was even a few years ago. On IBM i, l 26% of organizations have implemented a database encryption solution. Seventy-four percent have no plans to do so.
In the event your organization does suffer a data breach, encryption is your last line of defense. The data is worthless to attackers if they don’t have the encryption key. In many cases, this means your organization won’t have to notify customers of the breach because no data was actually exposed.
Database encryption on IBM i is simpler than you might think, thanks to the field procedures introduced by IBM. We have resources that explain what the process involves:
- Using Field Procedures for IBM i Encryption
- Encryption on IBM i Simplified
- IBM i Encryption: How to Protect Your Database
Make an IBM i Security Plan
To succeed at securing your IBM i, a plan is critical. A free Security Scan is a great place to start because you’ll find out where your systems are most vulnerable and get expert tips for prioritizing your security controls. You’ll also get a report summarizing the state of your IBM i security, which can help you formulate your plan and track your progress. It's free, it's simple, and it'll help you understand what changes could make the biggest impact on your security posture.
To get started, request your free Security Scan today.
