Each year, the State of IBM i Security Study analyzes the latest data around cybersecurity controls around this powerful operating system. The data comes from Security Scans performed by Fortra throughout the previous year, and shows what organizations are actually doing to secure their IBM i data—and it reveals areas where the failure to follow best practices can leave organizations vulnerable to data leaks or breaches.
IBM i security best practices start with the configuration of numerous system values, which regulate how easy or difficult it is for an outsider to use or abuse your system. Poorly configured or unmonitored system values are an unacceptable security risk.
The system security level (QSECURTY) sets the overall tone, although it is often undermined by other settings. IBM recommends and ships security level 40 as the minimum, due to documented vulnerability found in level 30 and below. It should be noted that, despite the change to the default setting, a server migration will typically reload this to the same value as found on the previous generation of the server.
Power Systems servers can be configured at one of five different security levels:
- Level 10 — Physical Security. No password required. User profiles are created for any user who attempts to sign on. IBM no longer supports level 10.
- Level 20 — Password Security. Every user must have a valid profile and password. Every user with a valid profile and password assumes root-level authority (*ALLOBJ) by default.
- Level 30 — Resource Security. Object-level authority is enforced as users do not assume root-level authority by default. A moderately knowledgeable programmer or operator can bypass resource-level security and assume root-level authority.
- Level 40 — Operating System Integrity. Level 30 protection plus additional operating system integrity. It is possible for an extremely knowledgeable programmer with access to your system to elevate his or her level of authority, possibly as high as root-level authority.
- Level 50 — Enhanced Operating System Security. Level 40 protection plus enhanced operating system integrity. A properly secured system at security level 50 is the best defense. However, even at level 50, other system configuration issues must be addressed.
Figure 1 shows the distribution of security settings on the systems included in the 2021 dataset. Out of the 247 systems studied, 18 percent were running system security level 30 and eight percent were running at security level 20. Overall, 26 percent fell short of IBM’s recommended minimum level (Figure 1A). Many running on a sub-par security level are doing so without deliberate intent after having migrated their system values from an older server and are now recognizing the need to take corrective action.
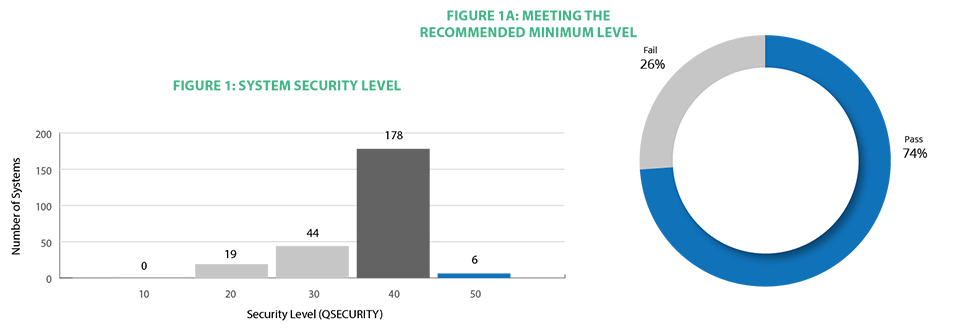
Bringing your system up to QSECURITY level 40 or higher is a critical step toward protecting your system. Organizations that are unsure of the potential impact of system value changes may want to consult with IBM i security professionals first, but a solution should be applied quickly. Outsourcing this task to security professionals like the team at Fortra is a way to eliminate quickly all the guesswork from the process.
Download the Full State of IBM i Security Study
Find out where IBM i systems tend to be secure and where they're often vulnerable. Download the complete State of IBM i Security Study today.