Security issues around IBM i user profiles are serious business: they represent one of the most obvious ways to compromise your system.
And without proper user security measures in place, efforts to secure other areas of an IBM i network are largely ineffective.
Inactive user profiles are a surprisingly common vulnerability. Keep reading to see the latest data and learn IBM i (AS/400) security best practices related to inactive user profiles.
Inactive profiles are a prime target
Inactive profiles are user profiles that have not been used in the last 30 days or more. They create a security exposure because these accounts are not actively maintained by their users, which make them prime targets for hijacking.
Many of these inactive profiles belong to former employees or contractors—people who might carry a grudge or who might find their former employer’s data useful in their new roles at competitors.
The threat persists even if ex-employees never attempt to utilize these profiles. Other users within the organization might know, for example, that the former IT director’s profile is still on the system. And whether an inactive profile is exploited by a former employee, a malicious insider, or a hacker, unusual use of the profile won’t be detected and reported by the profile owner.
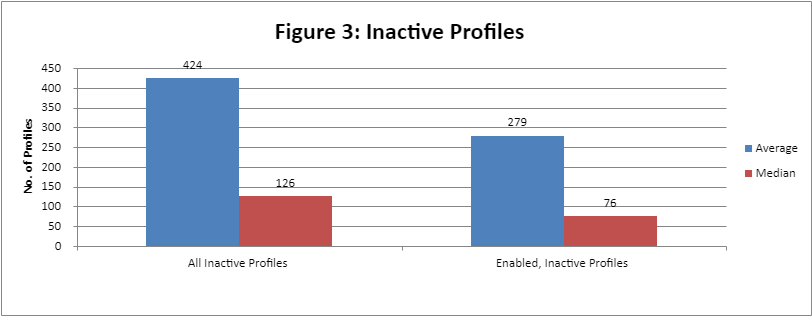
The annual State of IBM i Security Study analyzes how many inactive profiles remain on IBM i systems around the world, and how many of those inactive profiles are still enabled.
Figure 3 shows an average of 427 profiles (40 percent of the total) have not signed on in the past 30 days or more. Of these, 259 of them remain enabled and ready to be used.
AS/400 security best practices for inactive user profiles
Develop a process for inactive profiles. Start by defining how long a profile must be inactive before you take action (perhaps 60 days), disable the inactive profiles, and remove all special authorities and group profile assignments. Wait another 30 days to make sure the profile really is inactive before removing it from the system, or until the name of the user is no longer required for reconciling with the audit trail.
This process can be performed manually or automated using IBM’s built-in security tools.
Get the Latest IBM i Security Data
Find out how organizations around the world are securing their systems and learn IBM i (AS/400) security best practices. Download the latest State of IBM i Security Study today.