Have you performed pen testing lately?
Here's why we ask: penetration tests help determine if a security breach will be prevented and they ensure that interested parties receive security notifications.
By attempting to exploit security vulnerabilities on your IBM i (AS/400, iSeries), you'll find out if your security measures are functioning as expected or if an attacker could gain access to sensitive data.
Pen testing is a proactive approach to cybersecurity, allowing you to indentify and fix security gaps before any harm occurs.
Think of it like checking your door after you leave the house. You know you've installed a deadbolt. You know it should prevent someone without a key from simply opening the door and walking into your living room. And you know locked the door. Or at least you're pretty sure you locked it.
The thing is, you can't be certain the door is locked and the deadbolt is working properly unless you check. You try to turn the knob and push the door open to verifty that your security technology is working as it should. If the door is locked? Great, you can walk away with peace of mind.
If the door opens right up? Not the result you expected, but at least you're aware of it and can take steps to correct the problem before you leave the property.
Pen testing is much like this for your server security. You find out if your system settings and configurations and cybersecurity software deliver the result you want when someone attempts to gain unauthorized access to sensitive data, like PII (personally identifiable information).
If the test shows an unauthorized individual cannot access your data, you can feel confident about the state of your IBM i security.
And if the penetration test reveals sensitive data could be changed, downloaded, or deleted without any security alerts, you know you have more work to do to protect the system. This is the reason even a failed pen isn't necessarily bad news. It's only bad news if no one determines the cause of the failure, attempts to correct it, and verifies that the corrective steps worked.
Now a PCI DSS Requirement
Another issue to keep in mind is that pen testing is now a PCI requirement. If your organization is required to comply with the Payment Card Industry Data Security Standard, make annual tests are part of your security and compliance plan.
Questions about pen testing? Our security team can help >
What if I've already secured the IBM i perimeter?
Even if you're using Powertech Exit Point Manager for IBM i to protect your perimeter, pen testing should be a part of your plan. Failed tests might be indicative of a problem with product activation, or an incorrect or outdated Exit Point Manager for IBM i rule set.
For best results, test a number of services including: FTP, Remote Command, and Client Access. Here are some simple tips for Exit Point Manager for IBM i users:
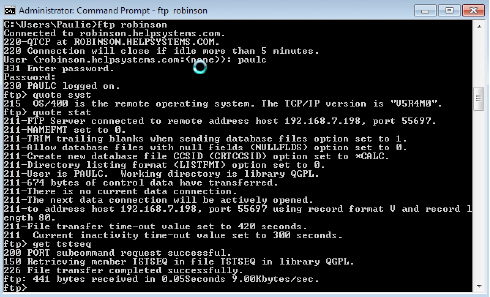
FTP Vulnerability
From a PC command prompt enter c:/ftp your system name or IP address then sign on. The command ftp>quote stat will provide the user with information regarding how FTP is configured on your system. The user can now “get” data from your system, change it, and “put” it back.
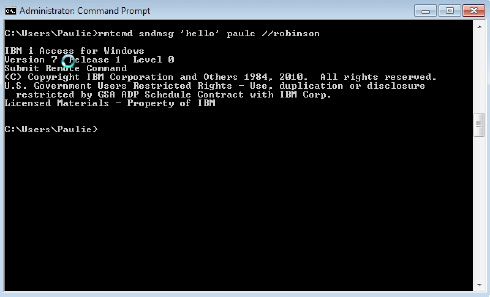
Remote Command Vulnerability
Client Access users can execute commands from a PC command prompt. Here is an example of a simple send message command for you to try:
C:/rmtcmd sndmsg ‘hello’ YourUserID //YourSystemName or IP
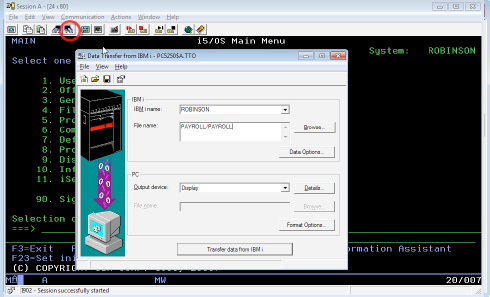
Client Access File Transfer Vulnerability
The Client Access toolbar contains mechanisms for file retrieval. This is an easy way for users to exploit their object authority by downloading files or displaying them on screen.
Final Thoughts
Whether you're a Exit Point Manager for IBM i user or not, penetration testing can be a valuable strategy for ensuring your business's sensitive data is safe from attackers. While it's a requirement for organizations affected by PCI DSS, pen testing is beneficial for anyone who wants to know where the system vulnerabilities are before cyberattackers find them. To learn more about the testing process, contact our team of security professionals today >
Let's Get Started
Independent, third-party pen testing can help you determine whether your AS/400 security defenses are up to par. Contact our cybersecurity team to get started.