The profile swap is a powerful authority inheritance technique. Introduced by IBM to support TCP/IP services, a profile swap allows a job to change midstream and run under a different profile than the one that started it. For example, when the FTP server starts, its “listener” jobs start and run under the QTCP profile. However, when a user logs in to FTP and issues a request, you want to run the authority check against the user rather than QTCP. To handle this, the operating system switches from the QTCP profile to the logged-in user before executing the request.
To see this support in the operating system, run the Display Job (DSPJOB) command and select option 1. You’ll see the traditional job name, user, and number at the top of the screen, and the “current user profile.” This normally contains the job user, but also indicates when there’s an active profile swap. Programmers should note that the RTVJOBA command was enhanced with the Current User (CURUSER) parameter to retrieve the current active user separately from the original job user. (Unless the job user is to be retrieved regardless of an active swap, I recommend using CURUSER, since this parameter still returns the job user information if there’s no active swap.)
People often ask if a profile swap is the same as adopting authority—a programmatic technique that allows a user to add the authority of an application program object’s owner. Authority adoption provides a temporary elevation of authority, but there are some distinct differences between adoption and a profile swap:
- Authority adoption only works for native object access, not IFS objects. A profile swap works for both native objects and IFS environments.
- Adoption is cumulative for each program called —the default setting allows authorities to accumulate. You can adopt the authority of multiple profiles as additional programs are called.
- Profile swapping releases the authority of the original profile before assigning the authority of the swap profile. This allows you to lower the authority of a user (for example, swap a user with *ALLOBJ special authority to a profile that has read-only rights before they access a function.)
- Adoption never changes who the underlying profile is during the adoption process. In contrast, a profile swap literally changes the user to the target user—almost as if they had signed on. The user assumes run-time attributes beyond authorities, such as a default output queue and command line access.
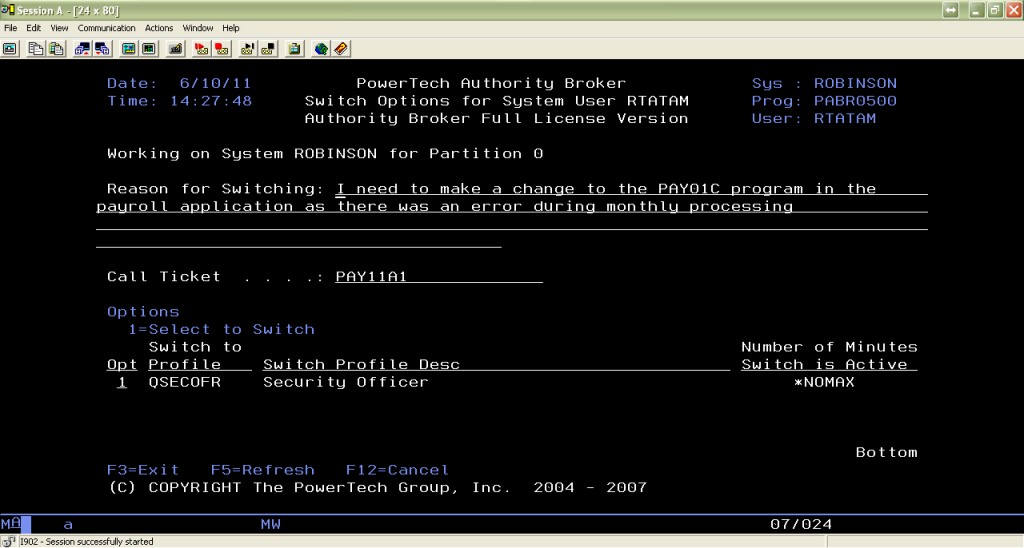
Powertech Authority Broker for IBM i removes the “heavy lifting” associated with profile swaps, and enhances the functionality beyond the API support in the operating system.
Authority Broker for IBM i users can use pre-authorized swap profiles for a temporary authority change. You can run the swap from a command line, or embed it in a program. This makes the swap transparent to end users (think contractors and software vendors). Real-time notifications can advise managers and auditors when users temporarily alter their authority (see Figure 1). And, you can run detailed reports of command line activities after they’re done. Plus, Authority Broker for IBM i supports segregation of duties, time-restricted switching, tamper-proof logging, and activity exporting.
Get Started
Find out how Authority Broker can help you meet your security and compliance goals.