
The biggest roadblock to IBM i security success is the misconception that it’s already a secure platform. Many assume that, because their users don’t know how to navigate the system outside of their limited interface and because the IBM i is not a well-known platform, there’s little threat of any internal or external threat actors.
Just like any other platform, there are threat actors with knowledge of the IBM i waiting to take advantage of organizations that leave their systems vulnerable. Thankfully, being proactive, developing a malware defense strategy, and implementing a native antivirus solution backed by excellent support, such as Fortra’s Powertech Antivirus for IBM i, can protect your organization and its customers from even the most advanced threats.
I’ve witnessed Powertech Antivirus save organizations from devastating attacks on countless occasions. In this blog, I will be discussing different scenarios in which organizations commonly find their IBM i vulnerable to attacks and how Powertech Antivirus has helped real organizations neutralize the danger.
Ransomware on IBM i
The days of ransomware being a non-factor for IBM i environments are long gone. The increased interconnectedness of the IBM i along with common security mistakes like sharing IFS directories and maintaining overprivileged users have made the IBM i vulnerable to ransomware attacks. With its native IBM i scanning capabilities and behavior-based detection technology, Powertech Antivirus for IBM i’s anti-ransomware is your best bet for securing your IBM i against today’s greatest digital threat.
For example, around this time last year, a colleague of mine was working with a customer that may have saved their company by being proactive and installing Powertech Antivirus on their IBM i. They had enabled the product’s AR functionality and used it to block a user suspected of performing suspicious activity. That user was in fact executing a ransomware attack and was stopped after encrypting only a handful of files.
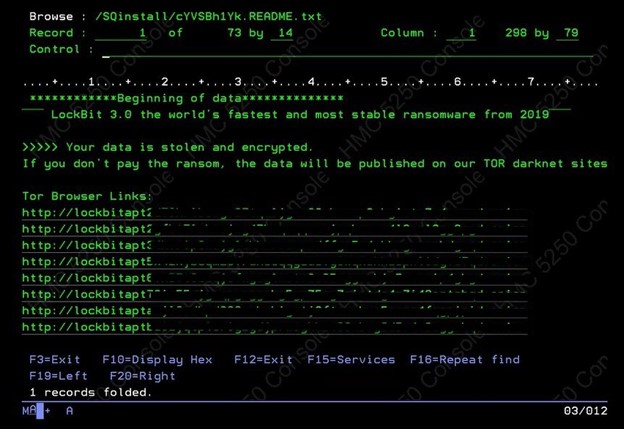
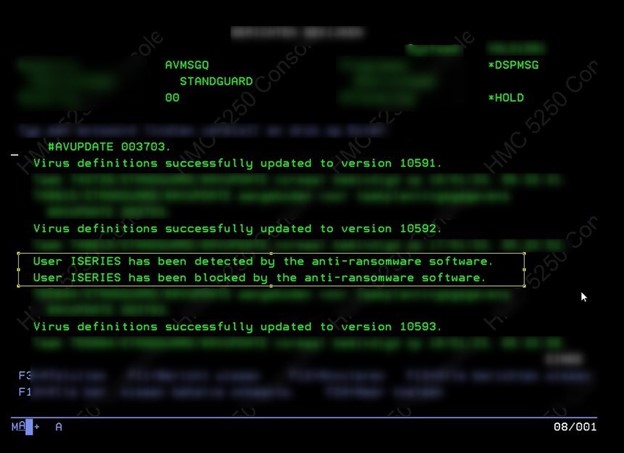
In the first screenshot above, you can see the heart-stopping message that was received by the organization’s IT admin. Fortunately for this customer, that window of shock was limited to just seconds, as Powertech Antivirus for IBM i identified the malicious behavior in near real-time and blocked the user, prompting the message that was sent in the second screenshot above.
Ransomware Can Lie Dormant for Years
Although Powertech Antivirus is most useful when deployed preemptively, the product is extremely effective in sniffing out lingering infected files that could be used to repeat devastating attacks.
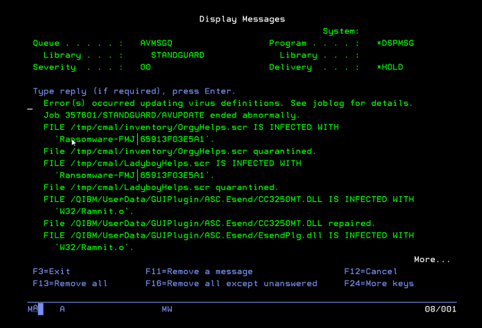
In 2021, I worked with a customer that experienced a ransomware attack in 2017. They were certain they had cleaned everything up and had rid their systems of the malicious virus. However, upon performing a scan with Powertech Antivirus, a file containing the malware was discovered. We also discovered that someone had attempted to open that file less than six months prior to scanning. They had narrowly avoided relaunching the same attack that crippled their systems years ago.
In the screenshot below, you can see the names of the infected files followed by statements describing the corrective actions that Powertech Antivirus automatically took to contain and repair the files:
Below, you can see the time stamps in which the infection took place and when the infected file was last accessed:

In instances like these, we make sure to go the extra mile in assisting customers with optimizing their scanning for remnants of malware. We make sure that any user who had access to that file server or share, the IFS, or any application used to pull the file is not infected.
Infected Directories
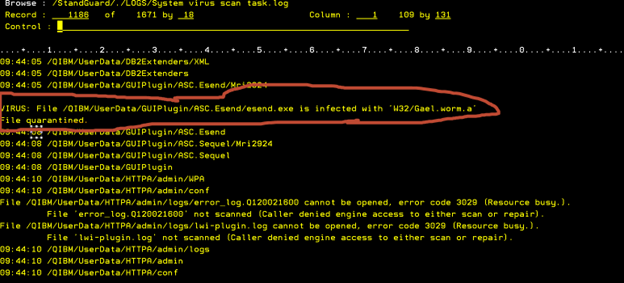
The need for antivirus scanning is continuous. We have seen malware that has been allowed to remain on organization’s sites for close to a decade. This type of oversight can spell disaster. I’ve personally seen such things lead to IBM directories and even vendor directories becoming infected, as evidenced by the screenshot below:
Compromised Credentials of Over-Privileged Users
Ransomware attacks are not one dimensional. They can come from a variety of fronts and can even be caused by negligence on behalf of some of your most trusted employees. I once had a customer reach out to us after a ransomware attack left over 500,000 objects in their IFS encrypted. As it turned out, one of their users had *ALLOBJ authority and a mapped drive to the root directory of their IFS. On a Friday afternoon, that user received an email with an attachment that was infected with CryptoWall and unknowingly opened it.
The CryptoWall ransomware started running, and in the meantime, the oblivious user went home for the weekend, leaving their PC on and the malware free to do damage. By Sunday morning, another employee realized that their backups hadn’t been completed, so they tried signing on to the system to check but were unable to. They ended up signing onto the console and discovering that more than half a million objects in the IFS were encrypted, including many of their TCP/IP configuration files, WebSphere directories and files used for batch jobs. They called us that week and I helped them install Powertech Antivirus and set up a scan. The screen shot is the result of that first scan. They spent the better part of a month cleaning up and restoring their files.
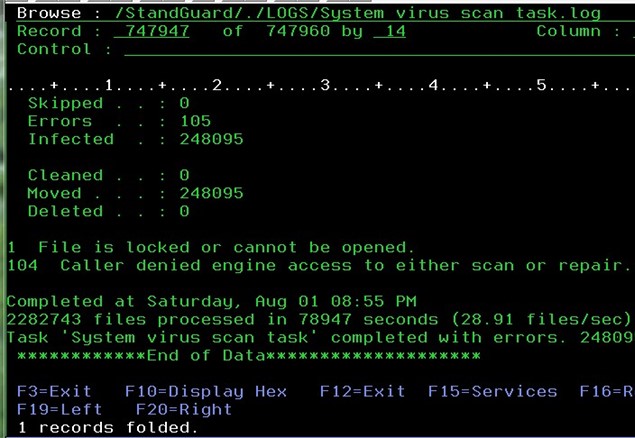
With Powertech Antivirus for IBM i’s anti ransomware technology, the actions of the attacker would have been identified as malicious and the user would have been blocked almost instantaneously – minimizing the amount of files encrypted and limiting the damage. The video below offers an explanation of how Powertech Antivirus for IBM i leverages behavior-based detection in thwarting ransomware attacks.
Outside of detecting and blocking the ransomware attack, this organization could have also secured its data with authority brokering technology. Powertech Authority Broker for IBM i uses monitored authority swaps so that users can only temporarily use elevated authority in instances where it is absolutely necessary. This security measure would have prevented the attacker from having a direct line of access to the root directory.
There's No Way Around the Need for Anti-Malware
Take it from the team with decades of first-hand experience serving customers of all sizes and industries: Whether you have Linux, AIX, or IBM i, the threat of malware is very real and the only way to truly combat it is with antimalware technology.
If securing your mission-critical servers against today’s threats is a priority for your organization, you can get started today with a free 30-day trial of Fortra’s Powertech Antivirus.
