Fortra threat researchers identify, analyze, and highlight emerging cyber threats by turning data from proprietary, open source, and third-party sources into actionable threat intelligence—improving analytics and empowering security decisions.
FIRE Team Members Include
Vulnerability researchers
Malware analysts
Data scientists
Security architects
Automation engineers
Security developers
Reverse engineers
Red and blue team experts
Fortra is proud to partner with law enforcement, global CISOs, and like-minded organizations for intelligence
sharing in the collective fight against cybercrime.
Fight Adversaries with FIRE
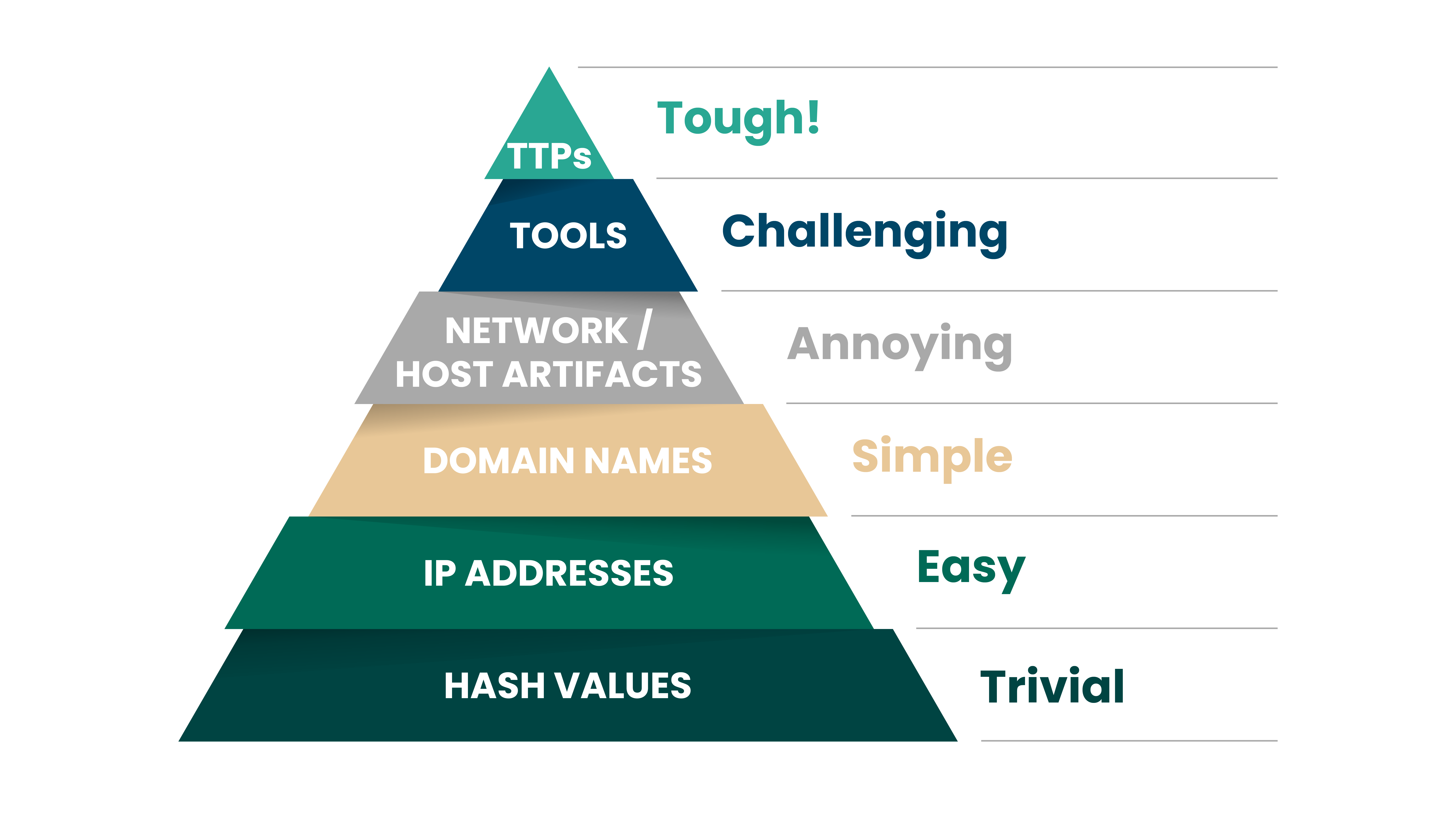
Fortra and the Pyramid of Pain
The Pyramid of Pain is an essential framework for breaking the attack chain. Continuous profiling of active adversaries and campaigns creates coverage from bottom to top, facilitating cyber vigilance by disrupting adversarial TTPs (tactics, techniques, and procedures) and empowering proactive security decisions before adversaries can advance along the attack chain toward their objectives.
The pyramid illustrates the varying difficulty of obstacles attackers face when cyber defenders uncover their indicators of compromise. Targeting indicators at the bottom of the pyramid—e.g., hash values—only slightly inconveniences an attacker, since they can easily generate new hash values by simply changing the coding syntax of a malicious program.
Moving further up the pyramid, targeting indicators like adversarial TTPs is more painful for an attacker to alter because it requires threat actors to reevaluate their attack strategy, abandoning time-tested attack methods, and forces them to find new TTPs that achieve the same goal or face redesigning entire chunks of their attack sequence—even retraining other threat actors when operating as a part of organized cybercrime groups.
Fortra Threat Brain automatically addresses the Trivial, Easy, Simple, and Annoying IOCs across the pyramid, allowing our Fortra Intelligence and Research Experts (FIRE) to tackle the Challenging and Tough IOCs and disseminate timely and actionable intelligence, insights, and threat trends to our products, managed services, partners and customers.
FIRE burns through threat actors’ most complex indicators, forcing adversaries back to the drawing board.

Fortra Security Operations Center (SOC)
The Fortra SOC is comprised of specialist detection and mitigation groups that are on the front lines of FIRE, facing continuous cybersecurity incidents, events, attacks, and threats.
The SOC’s defensive capabilities can extend both within and beyond the firewall, allowing Fortra to defend organizations with an extensive portfolio of solutions all the way from lookalike.
domain takedowns to finetuning data egress detection rules. This dedicated team is built upon multiple service lines in various industries and disciplines, which further expands Fortra’s exposure and contributions to the extensive threat landscape.
Fortra's dedicated SOC team is made up of the following cybersecurity disciplines:
Brand Protection
Data Loss Prevention
Extended Detection and Response
Web Application Firewall
Integrity and Compliance Monitoring
Regardless of which team is responding to a cyber threat, Fortra’s service lines are unified through shared threat intelligence and research — continuously exchanging insights with FIRE in a virtuous cycle. For example, Fortra DLP analysts regularly identify malicious patterns, such as geolocations or system commands, that target data confidentiality, integrity, and availability.
In addition, Fortra Brand Protection analysts share indicators of compromise (IOCs) that accelerate the dissemination of actionable intelligence through tools like Fortra Threat Brain. Together, these advanced SOC capabilities, solutions, and teams enable FIRE to deliver unmatched threat intelligence and research.
Fortra Research and Development (R&D)
Fortra’s broader intelligence and research team includes R&D technologists who focus on threat intelligence and protecting customers from cyberattacks. While the Fortra SOC concentrates on threat disruption and attack takedown efforts, the R&D team takes a broader, long-term view — leveraging research, innovation, and intelligence to anticipate emerging threats and strengthen defensive capabilities.
insights from the SOC to identify patterns that inform overall threat intelligence, research, and build the bigger picture of the threat landscape.
Our research and development team is constructed on the following three pillars:
Research
Artificial Intelligence and Machine Learning
Content
FIRE and Fortra Threat Brain
The analysts of the FIRE team consistently update Fortra Threat Brain with newly discovered threat research and intelligence, verifying and adding threat data obtained from other partner sources. In turn, FIRE draws AI-driven information from Fortra Threat Brain to enrich and apply this intelligence through advanced analytics, creating and finetuning content to help Fortra customers stay ahead of evolving threats.

By the Numbers
exfiltration attempts
blocked monthly

credential theft incidents
detected monthly

phishing, social media, domain, and open web threats mitigated monthly

vulnerabilities
tracked monthly

global threats
blocked monthly

queries to Fortra
Threat Brain monthly