Field Encryption
Automatically encrypt database fields and columns using strong AES encryption in Powertech Encryption
Database field encryption has traditionally been very difficult and time-consuming to implement on IBM i. In the past, major application changes would have to be made to expand database field sizes and implement complicated API calls to encrypt/decrypt data. In contrast, the design of Powertech Encryption for IBM i allows organizations to encrypt fields quickly and effectively using its intuitive screens and proven technology.
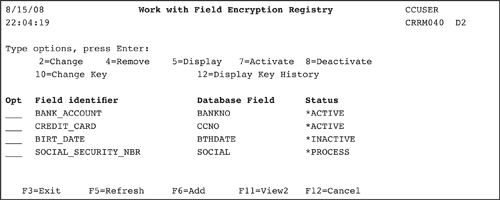
With Powertech Encryption for IBM i's innovative "Field Encryption Registry", you can simply indicate the database fields to encrypt within your database files. When a field is "activated" in the Registry, Powertech Encryption for IBM i will perform a mass encryption of the current values for that field. Powertech Encryption for IBM i can then automatically encrypt the field values on an ongoing basis as new database records are added and when existing field values are changed. The automated encryption function in Powertech Encryption for IBM i's Field Encryption Registry will eliminate the need to make changes to your application programs for data encryption.
If DB2 Field Procedures (available in IBM i V7R1) are utilized in Powertech Encryption for IBM i, the values can also be automatically decrypted without program changes. Otherwise, simple program changes can be made to decrypt values using Powertech Encryption for IBM i's APIs.
You can optionally modify your applications to encrypt data through program (API) calls to Powertech Encryption for IBM i's encryption procedures and programs. Powertech Encryption for IBM i also includes stored procedures and SQL functions, which can be called from within native applications or other external clients (i.e. graphical or web-based front ends) for encryption/decryption.
IBM i database fields can be protected in Powertech Encryption for IBM i using either AES and TDES encryption algorithms. Both of these algorithms follow standard (non-proprietary) specifications as published by the United States National Institute of Standards and Technology (NIST). AES and TDES are widely used for protecting highly sensitive data and complying with PCI DSS, HIPAA and State Privacy laws.
For AES encryption, you can choose between the key lengths of AES128, AES192 and AES256.
You can encrypt almost any IBM i DB2 database field with Powertech Encryption for IBM i. Field encryption examples:
- Credit card numbers (PAN)
- Social security numbers
- Bank account numbers
- Health-related information
- Wages
- Financial data
Encrypted database fields are secured with Data Encryption Keys (DEK) which are managed through Powertech Encryption for IBM i's integrated Key Management system. Only authorized users will have the ability to decrypt data and gain access to the full or masked values. Decryption of any data can be fully audited in Powertech Encryption for IBM i, which will log the user id, date, time, job information and key utilized.
IFS Encryption
Encrypt and decrypt files and folders on the Integrated File System
IFS Encryption is provided in Powertech Encryption for IBM i to allow IBM i (iSeries) customers to encrypt and decrypt files and folders on the Integrated File System. All types of IFS stream files can be encrypted including text, PDF, JPG, TIF, CSV and XLS files. The encryption of IFS files can be completely automatic for designated folders or can be user-driven using Powertech Encryption for IBM i commands.
Strong AES encryption is utilized for protecting files on the IFS. AES follows standard (non-proprietary) specifications as published by the United States National Institute of Standards and Technology (NIST). You can choose between key lengths of AES128, AES192 and AES256.
The IBM i IFS encryption provided in Powertech Encryption for IBM i allows organizations to comply with PCI DSS requirements, state privacy laws and federal regulations such as HIPAA and Sarbanes-Oxley. Powertech Encryption for IBM i is a pure software solution requiring no additional hardware.
Automatic IFS Encryption
Powertech Encryption can automate the encryption and decryption of files on the IFS. Through its innovative IFS encryption registry, authorized administrators can indicate which folders on the IFS should be encrypted. For each folder, you can indicate a unique encryption key for protecting the contents.
Once a folder is activated in the registry, Powertech Encryption will automatically encrypt files as they are written to that IFS folder. For authorized users, files will be automatically decrypted as they are accessed from the folder. You can control user access to each encrypted folder through the use of IBM authorization lists. A folder can be granted access to individual users or groups of users.
Command-Driven IFS Encryption
Native IFS encryption/decryption commands are available in Powertech Encryption, which can be easily integrated into existing IBM i applications and processes. Keys or passphrases can be used to protect the encrypted IFS files. Features include:
- Supports single file names and wildcards (e.g. *.pdf) to encrypt one or more IFS files at a time.
- Encrypted IFS files can be targeted to the IFS, a tape device and other physical and virtual backup devices.
- IFS encryption commands can be integrated quickly into existing processes.
- No intermediate save files are generated, saving disk space and time.
- Key labels can be stored in encrypted IFS files, so you don't have to remember which key to use on decryption.
- Only authorized users can be granted permissions to decrypt IFS files.
Powertech Encryption's IFS encryption/decryption commands can be entered on the IBM i command line, placed in CL programs, incorporated in BRMS and used in job schedulers on the IBM i.
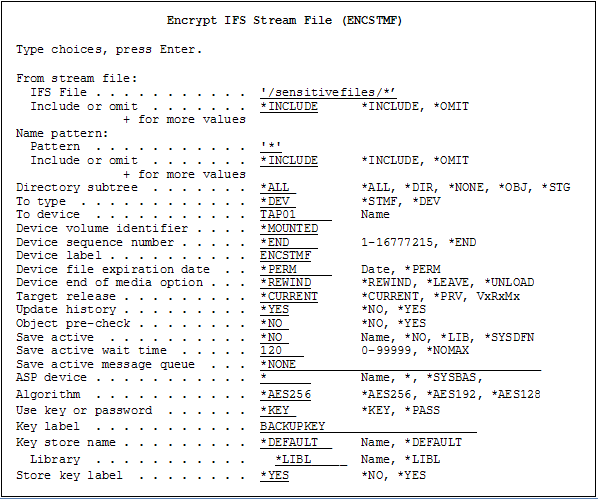
Example of command to encrypt IFS stream files:
Backup Encryption
Protect sensitive backup media
Powertech Encryption for IBM i offers native backup (tape) encryption for IBM i (iSeries) customers that wish to protect their sensitive backup media. This encryption is provided by commands in Powertech Encryption for IBM i which can encrypt and save entire libraries or individual objects. Symmetric keys or passphrases can be used to protect the encrypted backups.
AES encryption is implemented to provide strong protection for your backups. AES follows standard (non-proprietary) specifications as published by the United States National Institute of Standards and Technology (NIST). Powertech Encryption supports key lengths of AES128, AES192 and AES256.
The IBM i backup (tape) encryption provided in Powertech Encryption for IBM i allows organizations to comply with PCI DSS requirements, state privacy laws and federal regulations such as HIPAA and Sarbanes-Oxley.

Additional benefits of Powertech Encryption for IBM i's backup encryption:
- Powertech Encryption for IBM i is a pure software solution requiring no additional hardware.
- Customers can utilize their existing tape devices.
- Encrypted backups can be targeted to a tape device, virtual backup devices and the IFS.
- Backup/restore commands can be integrated quickly into existing backup processes.
- Encrypt entire libraries or selected objects.
- No intermediate save files are generated, saving disk space and time.
- Includes an integrated key management system that resides on the IBM i.
- Key labels can be stored with encrypted backups, so you don't have to remember which key to use to decrypt/restore a backup.
- Disaster recovery is simplified since no special devices are required to restore.
Powertech Encryption for IBM i's backup and restore commands can be entered on the IBM i command line, placed in CL programs, incorporated in BRMS and used in job schedulers on the IBM i.
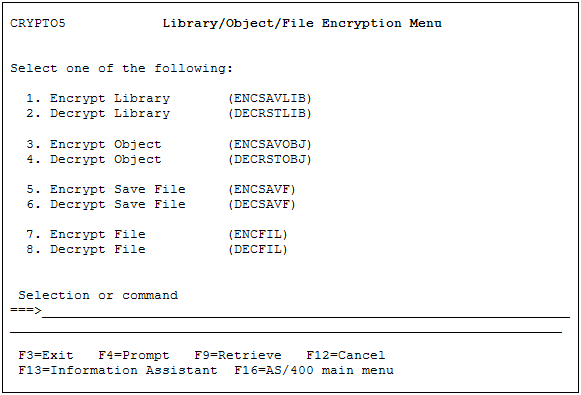
Backup encryption menu:
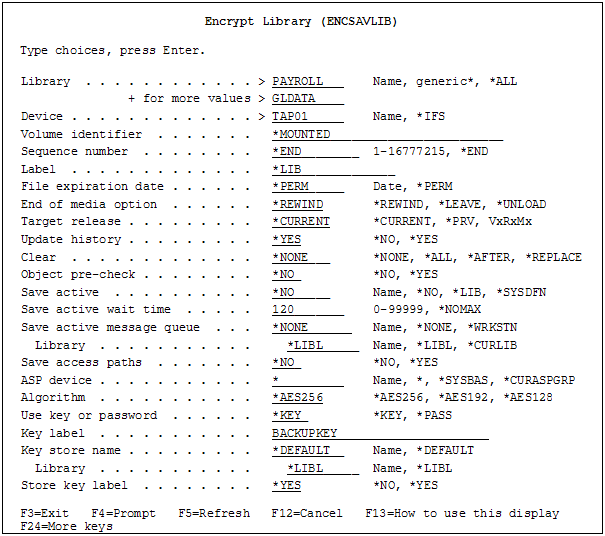
Example of command to encrypt and save libraries:
Native commands are also provided to restore/decrypt libraries, objects and IFS files which were saved using Powertech Encryption for IBM i's backup commands.
Get Started
IBM i database encryption doesn't need to be difficult or time consuming. implement encryption quickly and successfully with Powertech Encryption for IBM i. Request a free trial today.