Tokenization should be considered when sensitive data is stored on multiple systems throughout an organization. Tokenization is the process of replacing sensitive data with unique identification numbers (e.g. tokens) and storing the original data on a central server, typically in encrypted form.
By centralizing sensitive data onto a single system, tokenization can help thwart hackers and minimize the scope of compliance audits such as PCI. Tokenization can be used to protect any sensitive data including credit card numbers (PAN), bank account numbers, Social Security numbers, drivers license numbers and other personal identity information.
Powertech Encryption for IBM i Within a Tokenized Environment
Image
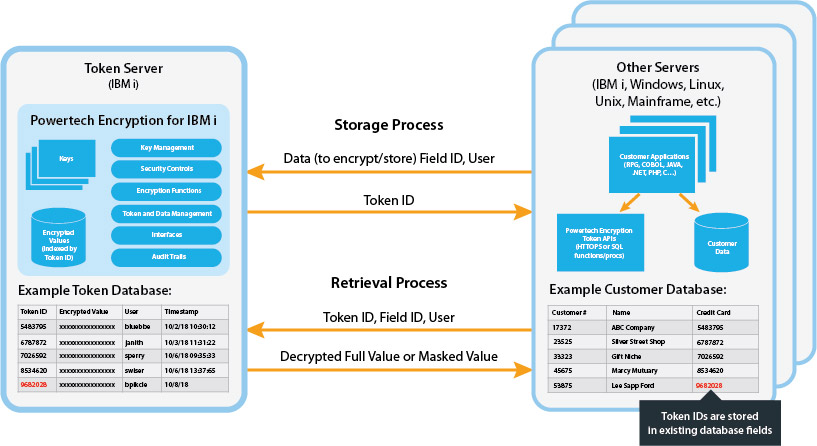

Storage Process
When data needs to be stored (typically on an insert or update), the remote system will pass this data, along with the Field Id and User to the Token Server. Powertech Encryption for IBM i will then assign a unique Token Id, and will encrypt and store that data into a DB2 physical file on the IBM i Token Server. The Token Id will be returned to the remote system, which would usually be stored in the same field (or column) as where the original data used to be located.
Retrieval Process
When data needs to be retrieved from the IBM i Token Server, the remote system will pass in the Token Id, Field Id and User. The data will then be retrieved from the DB2 physical file using the Token Id and Field Id. Based on the User’s authority and requested function, Powertech Encryption for IBM i can return the fully decrypted value, masked value or no value (if not authorized) to the remote system.
Key Features
Centralizes key management and policies on a single server
Supports tokenization of data from diverse systems including IBM i, Windows, Linux, AIX, etc.
Provides remote connections to token functions through secure HTTPS protocol
Auto-assigns token identifiers from the central token server
Encrypts and stores tokenized data into scalable DB2 physical files
Allows securing data elements by User Id, User Group and/or Authorization Lists
Provides centralized audit logs and message alerts
Get Started
Learn how centralizing sensitive data onto a single system can help thwart hackers and minimize the scope of compliance audits with tokenization by Powertech Encryption for IBM i. Request your personalized demo today.