Many IBM i applications use log files as a way to track events that occur within the application, whether they be good events or bad. However, the application architecture often spans multiple platforms, both on-premises and in the cloud, making it hard to identify and troubleshoot issues.
That’s why tracking the content of log files has become increasingly important in recent years.
Since early warning signs of future outages can be detected in log files, they are a key component in preventing interruptions to service. But before you fix these issues, you have to find them.
So, how can you get visibility into log file content without increasing your monitoring footprint or overhead?
Big Boost in App Visibility
Log File Monitor, included in IBM i Server Suite levels 3 and 4, can monitor the contents of files in the integrated file system (IFS), QSYS.LIB, other file systems, and external data sources accessible from an IBM i server (e.g., URLs), and raise alerts based on this content.
To provide users with ultimate flexibility, Log File Monitor supports a variety of different file types, including CSV, fixed, XML, and hybrid.
Log File Monitor includes a special CERT file type to support IBM i digital certificates that are held in any certificate store as well as their parameters (e.g., remaining validity period). Log files that can’t be specifically named and therefore fall into a more generic category are also supported.
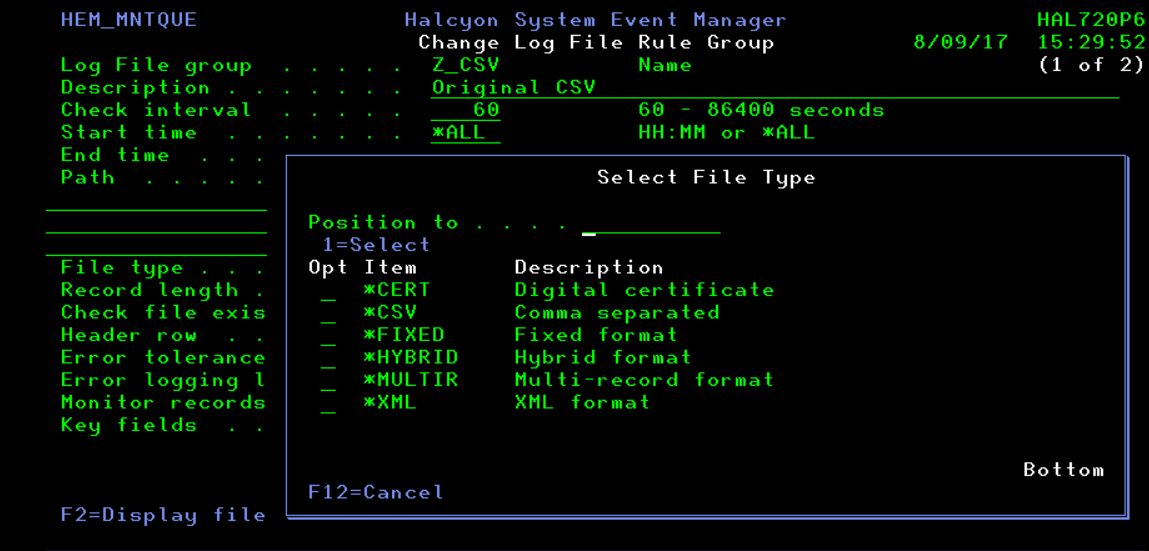
Figure 1: Log File Monitoring in IBM i Server Suite
Small Monitoring Footprint
With custom interval settings between 60 seconds and once per day, Log File Monitor gives you the ability to run a lean monitoring operation, so you won’t waste valuable CPU cycles.
Of course, depending on the application and the type of content being written, there will be times when you need to analyze all the file content at each interval instead of the new entries only. And some files, especially those containing XML data, can be very large and cumbersome to monitor. For these scenarios, Log File Monitor can extract precise subsets of data for comparison purposes.
It’s not uncommon to find incomplete or corrupt log file content, especially when you’re heading straight for a major application outage. Log File Monitor includes an error tolerance level to handle situations like this. You can adjust the settings on a file-by-file basis.
Custom Comparisons and Clear Notifications
Rule-based monitoring gives you ultimate control. You can define comprehensive rule criteria in Log File Monitor that will check file content for specific words, phrases, error conditions, codes, or even against a pre-defined list of values.
Using AND, OR, and ANDIF relationship triggers, you can link multiple checks on the same file and combine them with comparators such as EQ, GE, GT, LE, LIKE, LT, NE and NLIKE.
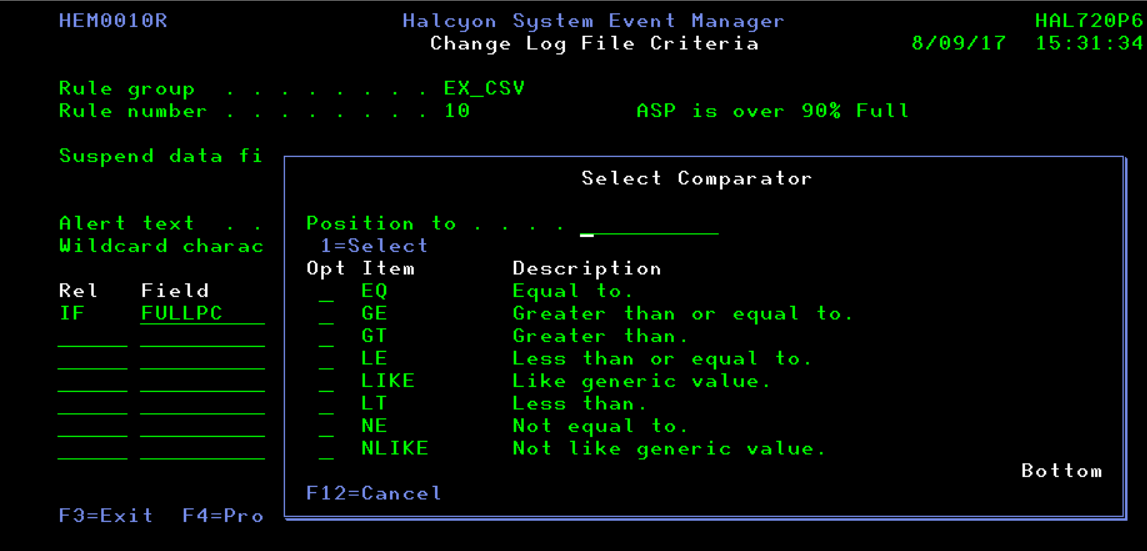
Figure 2: Link criteria in Log File Monitor with Comparators
There are two ways to perform rule checking: the traditional way, where you check criteria against the content, or by exception. When you check by exception, an alert is raised only when the content does not contain criteria defined in the rule.
Log File Monitor has over 20 built-in functions that allow users to manipulate data in order to perform advanced comparisons. These functions range from calculating the difference between two dates to scanning for a specific character string within an extracted section of the content.
The actions that can be performed are limitless. Among the most helpful actions are the ability to send an email or SMS notification and generate an Enterprise Console alert. More advanced actions include the COMMAND action, which allows users to run an IBM i command or call a program. This adds a degree of automation, where appropriate, and provides an easy way to pass variables that were extracted from the content of the file being monitored.
When combined with Alert Intelligence, which also ships as standard in IBM i Server Suite levels 3 and 4, you can link up to 12 rules across the suite for complete flexibility in monitoring. Let’s say a job has exceeded its normal run time by 10 minutes and there is an unacceptable error within a monitored log file. This combination may indicate a problem, so an alert should be raised.
Be sure to read our monthly release notes for the full list of enhancements to Halcyon Software.
Get Started
Discover how modular IBM i server monitoring tools help you easily monitor and automate critical components of your business. Request a demo to learn more about which IBM i Server Suite suits your business best.
