MedusaLocker, the ransomware-as-a-service (RaaS) group that has been active since 2019 is openly recruiting for penetration testers to help it compromise more businesses.
As Security Affairs reports, MedusaLocker has posted a job advert on its dark web leak site, which pointedly invites pentesters who already have direct access to corporate networks to make contact.
"If you don't have access, please don't waste your time"
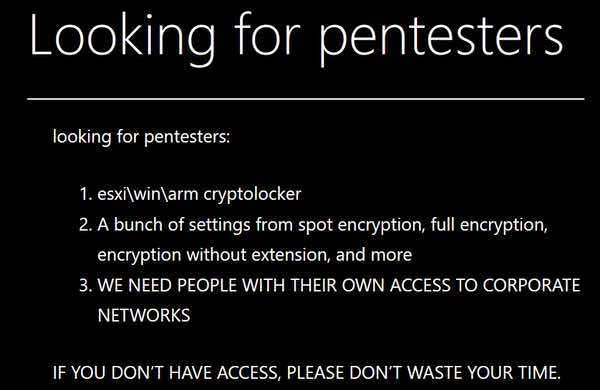
From the sound of things, MedusaLocker (which should not be confused with the similarly-named Medusa ransomware group) is essentially interested in being contacted by company insiders and initial access brokers who can help attackers gain easy access to an enterprise network.
Initial access brokers specialise in gaining unauthorised access to computer networks, and then sell their access to other cybercriminals.
They will often exploit human weakness by taking advantage of misconfigured or unpatched systems, or deploy phishing and social engineering attacks to infiltrate a corporate network.
The ultimate goal of the initial access broker is to sell their remote network access to other cybercriminals who will most likely monetise the situation by stealing data and deploying ransomware.
Often an initial access broker will spend time and effort seeking unauthorised access to a virtual private network, email server, or remote desktop protocol (RDP), allowing ransomware groups to free up their own time to deploy ransomware insider networks rather than attempting to break into companies themselves.
As CISA warned back in 2022, MedusaLocker attacks have heavily relied upon vulnerabilities in RDP to access victims' networks in the past.
So, what has this to do with penetration testing?
Penetration testers (or "pentesters") are cybersecurity professionals who use the techniques often used by cybercriminals to identify weakness in a company's defences before a malicious hacker does.
They responsibly report their findings back to the company, and work with them to resolve any issues.
A legitimate pentester would undoubtedly have the skillset required to search for weaknesses in a corporate network, and perhaps gain access. But one hopes that they would be too ethical to do so without authorisation from the company involved.
But here we see the MedusaLocker gang practically headhunting talent from the same pool of people who are normally employed to help companies protect themselves from cyber attack.
The lines between legitimate cybersecurity work and cybercrime are once again blurring.
"Every company gets penetration tested, whether or not they pay someone for the pleasure," goes an old adage in the industry.
All organisations need to be on their guard, and have put layered protections in place, to prevent themselves from becoming the next ransomware statistic.
It is clear from even the most casual read of the headlines that more and more companies are falling foul of ransomware attacks, and that the cybercriminals are finding it far too easy to gain an initial intrusion into businesses from which they can launch their attack.
One hopes that businesses are putting as much effort into hiring the talent to defend their networks, as ransomware gangs appear to be putting into recruiting pentesters who will open the door for attacks.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Cybercrime Intelligence Shouldn't Be Siloed
Fortra® experts are dedicated to protecting organizations and the public by delivering the latest insights, data, and defenses to strengthen security against emerging cyber threats.