What's happened?
The Scattered LAPSUS$ Hunters hacking group claims to have accessed data from around 40 customers of Salesforce, the cloud-based customer relationship management service, stealing almost one billion records.
Ouch! What organisations have been affected?
On its dark web leak site, the hackers list numerous organisations whose Salesforce instances it claims to have breached via social engineering:
1-800Accountant, Adidas, AeroMexico, AirFrance-KLM, Albertsons, Alexander McQueen, ASICS, Balenciaga, Brioni, CarMax, Cartier, Chanel, Cisco, Disney/Hulu, Engie Resources, FedEx, Fujifilm, GAP, Google Adsense, HBO Max, Home Depot, IKEA, Instacart, Instructure.com – Canvas, Kering (Gucci, KFC, Marriott, McDonald’s, MHM, Pandora, Petco, Puma, Qantas Airways, Republic Services, Saks Fifth (Avenue), Stellantis, Toyota, TransUnion, TripleA, UPS, Vietnam Airlines, and Walgreens.
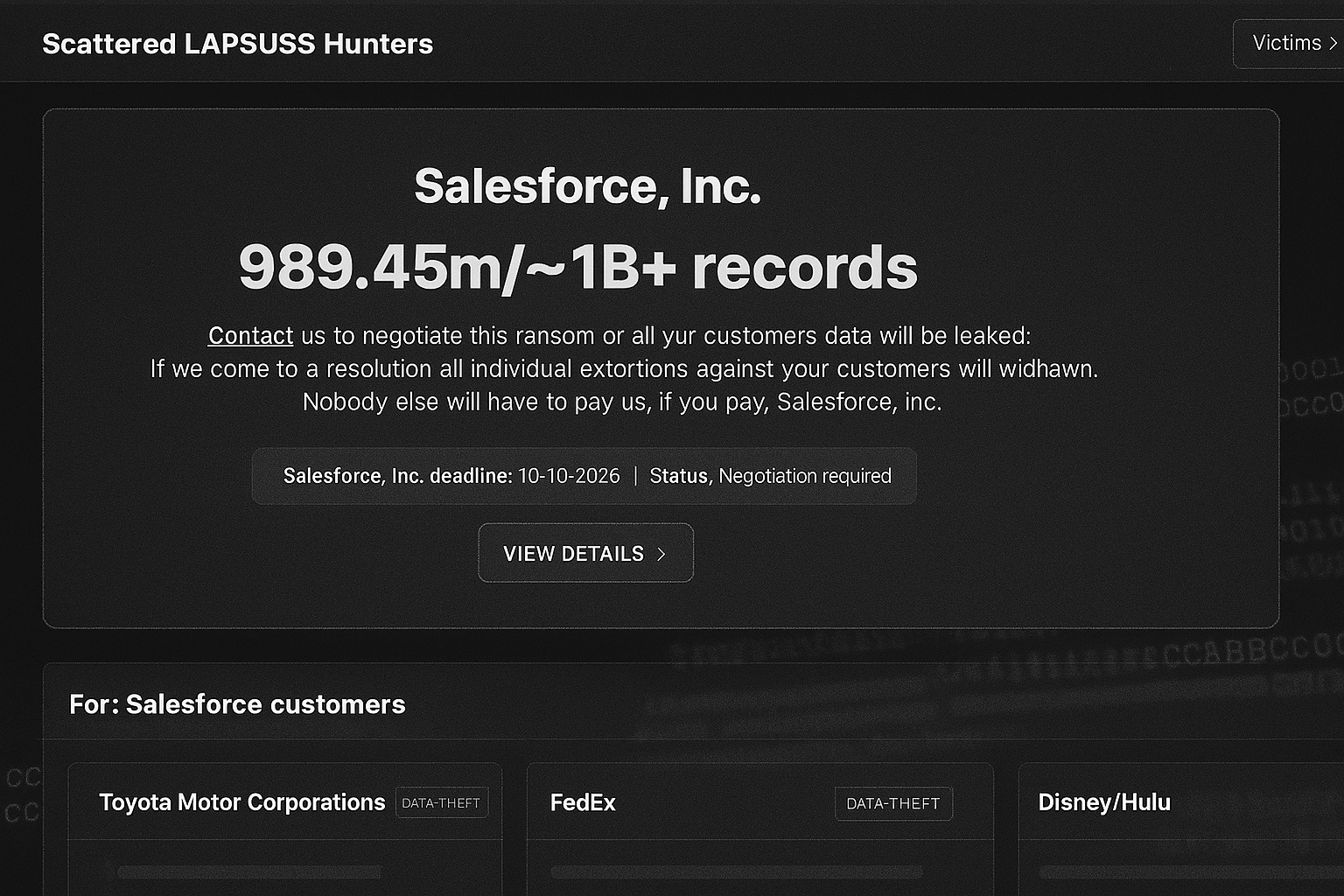
Each entry contains details of when the breach occurred, how much data has been exfiltrated, and a deadline for when a ransom has to be paid before the data is leaked.
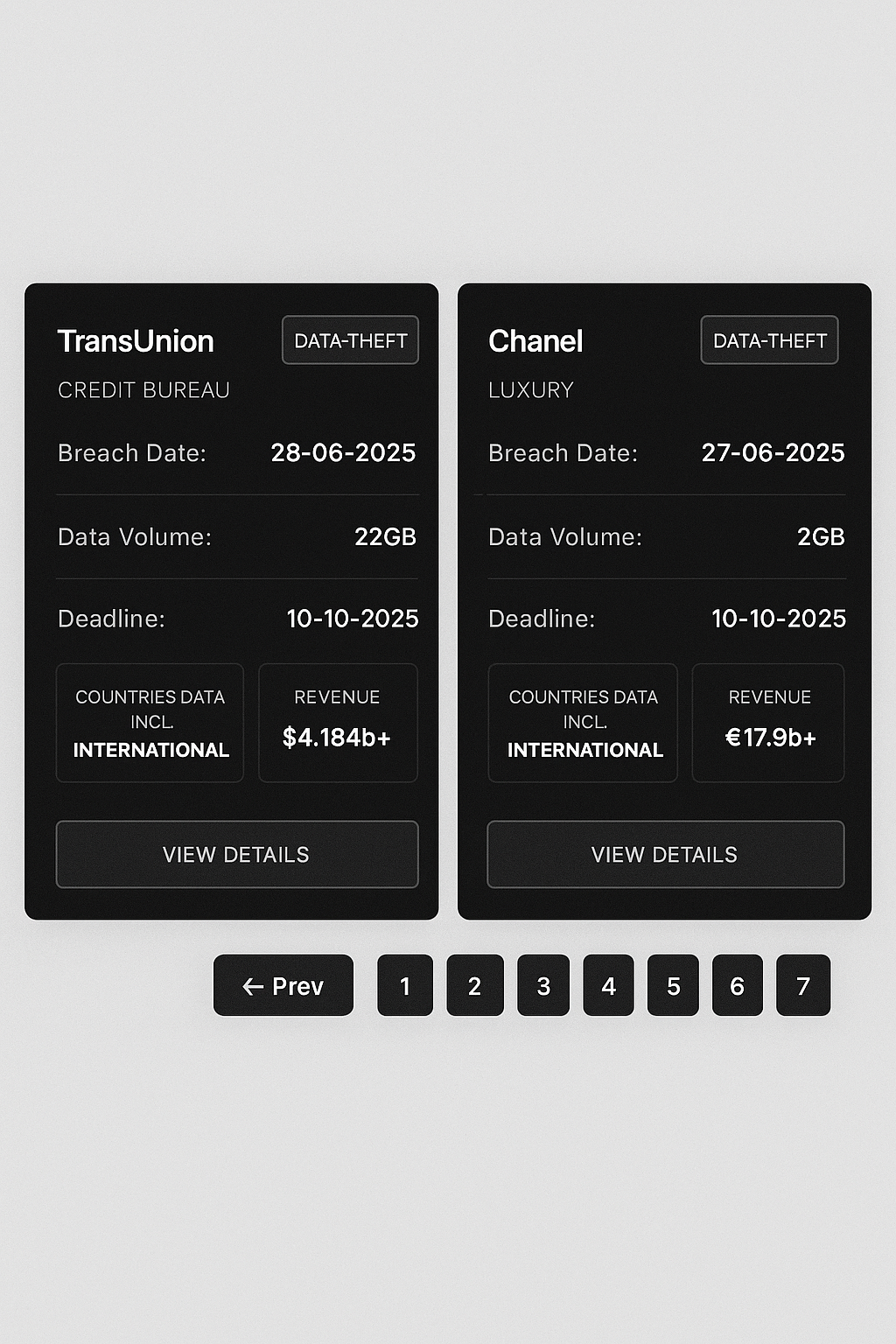
For instance, in the case of FedEx the hackers claim to have compromised its data on 31 August 2025, stealing 1.1TB of information - of which over 166 million records are claimed to contain personally identifiable information, including full names, email addresses, phone numbers, residence address, employee information, support chat transcripts and more.
So, I daren't even ask... but when is the deadline to pay the ransom?
The hacker are demanding payment by this Friday, 10 October 2025.
Crikey. That's just a couple of days away. How long has this been going on for?
In May, Adidas said that it was aware that some of its consumer data had been accessed "through a third-party customer service provider." In June, Google security researchers warned of the hacking campaign, only to find - in a cruel irony - that it had fallen foul of an attack that targeted one of its corporate databases run on Salesforce.
As more companies reported data breaches, Salesforce published a security advisory encouraging customers to enforce multi-factor authentication and other security measures, as well as warnings of social engineering and phishing attacks.
So is that how the hackers got in? Through phishing?
It appears that the hackers used the old-fashioned (but often highly effective) social engineering technique of making a phone call. By posing as IT support personnel, the hackers trick unwary employees into granting them access to sensitive systems or sharing sensitive credentials during the call.
So it's just human manipulation?
Pretty much. During the phone call, the attackers trick the targeted user into downloading a modified version of Salesforce's own Data Loader app. If the app is authorised to connect to the organisation's Salesforce portal, vast amounts of data can be stolen by hackers.
In August, Google researchers warned that some attacks were exfiltrating data via Salesforce's integration with the third-party app, Salesloft Drift. In response, SalesLoft advised customers to refresh the access tokens used to connect Drift and Salesforce apps, and Salesforce has since disabled Drift's connection to its systems.
What else has Salesforce had to say about this?
Salesforce has emphasised that its platform has not itself been compromised and that "this issue is not due to any known vulnerability in our technology." It has advised concerned customers to review their security settings and contact Salesforce's support team if they need assistance.
Okay, but the ransom deadline is looming...
Bloomberg reports that a security notification has been sent to customers explaining that Salesforce will not pay the ransom demand:
"Allen Tsai, a Salesforce spokesperson, said the company won’t engage, negotiate with or pay any extortion demand. The company is aware of recent extortion attempts, and it remains in contact with affected customers to provide support, the spokesperson said."
What should affected companies do?
Recommended steps to take immediately include:
- Audit all connected apps in Salesforce and revoke any suspicious authentication tokens.
- Checking API logs for any unexplained or large exports of data.
- Resetting integration tokens and refreshing secrets for connected services such as Salesloft.
- Educate staff about the risks posed not just by email phishing, but also voice-phishing techniques.
- Establish a multi-person approval process before granting a new app permission to connect to systems that hold sensitive data.
- Ready your customer communication and regulatory disclosure plans.
Is that it?
I don't think so. Although all the headlines mention Salesforce, this clearly isn't a threat to their platform. Security needs to be hardened wherever you store your data to ensure that a similar technique cannot be used across other Software-as-a-Service ecosystems.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Break the Attack Chain with Fortra®
Advanced offensive and defensive security solutions. Complete attack chain coverage. Shared threat intel and analytics. Add Fortra® to your arsenal.

