A wave of phishing attacks is targeting executives and privileged users with well-crafted PDFs containing malformed QR codes – designed to bypass both traditional email defenses and exploit mobile vulnerabilities. These campaigns are believed to be tied to Tycoon2fa, a highly active and popular Phishing-as-a-Service (PhaaS) group. What sets this campaign apart is its high degree of targeting and customization, with attachments disguised as internal handbooks, complete with corporate branding, table of contents, and personalized names. This professional packaging, coupled with the sophistication of the QR phish allows low-skilled actors to launch advanced attacks on high-value individuals like C-level executives, managers, and directors.
Key Points and Modus Operandi
1. Targeted Delivery
The email appears to originate from an internal system and includes a PDF attachment mimicking a new employee handbook.
2. Personalized Context
The PDF is tailored to the target, incorporating the official logo, corporate color scheme, recipient’s name, and company branding. It also includes a table of contents, step-by-step directions, and a QR code.
3. The Malformed QR Code
The embedded QR code is intentionally malformed, functioning when scanned by a phone but appearing as an image and evading detection by Microsoft’s security filters. This allows it to bypass tenant-level scanning and link extraction.
The QR code can be dynamic, depending on factors such as the scanning angle, the decoding engine, or the device used, which can result in a different URL redirect. This variability can be exploited by threat actors to evade detection. For instance, cybersecurity tools or analysis platforms might resolve the QR code to a legitimate URL, while a mobile device scan may redirect the user to a malicious phishing site, creating a deceptive split in destination visibility.
4. Credential Harvesting
Mobile Users are instructed to scan the QR code that, when scanned, directs to a spoofed Microsoft login page with the username pre-populated. Behind the scenes, the page acts as a reverse proxy: it forwards authentication requests to Microsoft to verify credentials. The traffic is then routed through a [.]ru domain where stolen credentials are harvested. If the correct password is entered, the user is redirected to the real Microsoft portal, unaware of the breach.
5. Phone Vulnerability
The intent of the campaign is for the user to utilize a personal device or a poorly hardened corporate phone, for which the scanning from a personal device bypasses corporate web-filtering controls and secure web gateways. An added benefit to the phone usage is that the URLs are shortened on the phone browser by default, making them less noticeable and further reducing user suspicion.
Indicators and Attribution
Threat Actor Group and Phishing-as-a-Service
Phishing-as-a-Service (PhaaS) is a cybercrime model in which experienced hackers offer phishing tools, templates, and services to less-technical individuals for a fee, typically via subscription. This approach lowers the barrier to entry, enabling attackers with minimal technical expertise to deploy advanced phishing campaigns. Like legitimate software-as-a-service (SaaS) offerings, PhaaS providers supply:
- Pre-built phishing kits
- Hosting and support
- Credential storage
- Malicious email and landing-page templates
- Step-by-step attack tutorials
- Credential-theft management tools
- Our infrastructure analysis suggests this campaign leverages a PhaaS provider “Tycoon2fa” active since 2013. Subscription access for services range from $120 to $320 and include:
- Prebuilt phishing kits and templates
- Credential storage and management tools
- Step-by-step attack automation guides
Safe-Attachment Vulnerability
During our investigation, a safe-attachment policy misfire was detected. A crafted string in the attachment triggered the policy, allowing the malicious PDF to pass through. Although this issue has been patched, we recommend auditing safe-attachment rules, scoping whitelists appropriately, and verifying that each policy remains necessary.
Dynamic Domain Generation
Within the attacker’s infrastructure, we discovered a PHP-based subdirectory that generates custom domain and subdomain iterations. Users can specify prefixes, suffixes, and root domain segments, enabling the rapid creation of hundreds of unique URLs. This makes detections, tracking, and blocking far more challenging for security teams.
Mitigation
Early threat detection is key to preventing data breaches, financial loss, and operational disruption:
- Proactive defense: Deploy real-time alerts for suspicious URLs, leveraging multiple threat-intelligence vendors and static IOCs on email gateways and web traffic monitoring systems.
- Pattern detection: Identify recurring artifacts such as random IDs in subjects, uniform attachment byte sequences, or sender-domain patterns by using regex or lexical rules on your secure email gateway.
- Fortra Secure Email Gateway (SEG) provides lexical expression capability which can be set to look for the IOCs found in text format or regex for a dynamic pattern-based detection.
- QR code analysis: Use OCR-enabled email security solutions to extract and validate links embedded in QR codes before delivery.
- Blocking strategies:
- Low level: Manually block known malicious domains/subdomains.
- Medium level: Temporarily block sending IPs until more robust pattern detection is in place.
- Behavioral detection: Integrate heuristic analysis and dynamic vendor feeds to block evolving phishing patterns rather than relying on static indicators alone.
Summary
QR code–based phishing is on the rise, delivered via email body, attachments, or seemingly benign URLs. Attackers exploit email-whitelisting gaps, malformed QR codes that evade tenant scanning, and mobile-only click prompts to bypass network defenses. A layered mitigation approach-including QR code extraction, multi-vendor URL scanning, advanced pattern detection, and stringent mobile-device management provides the best defense.
Screenshots
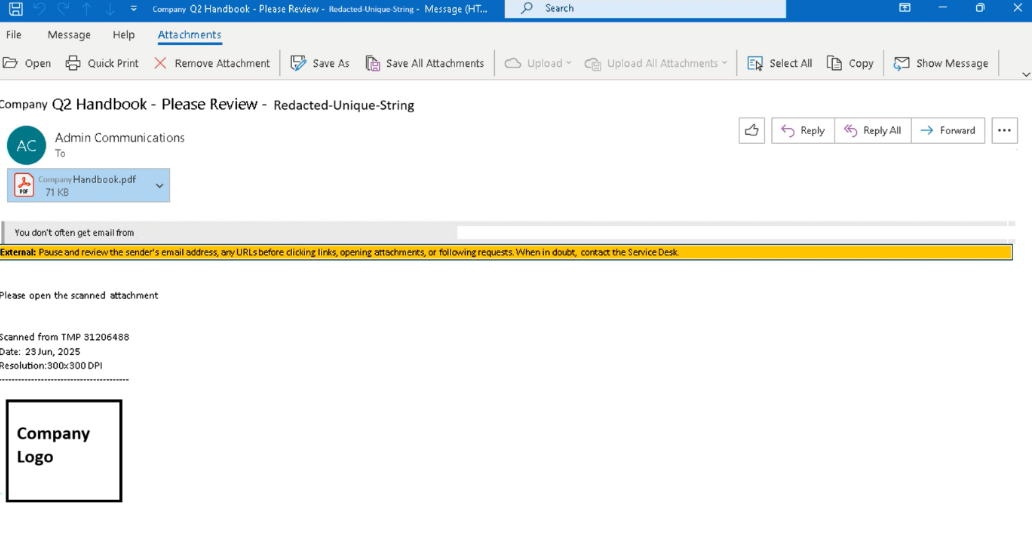
Email Lure
Email Attachment

Attachment Image 1

Attachment Image 2

Attachment Image 3
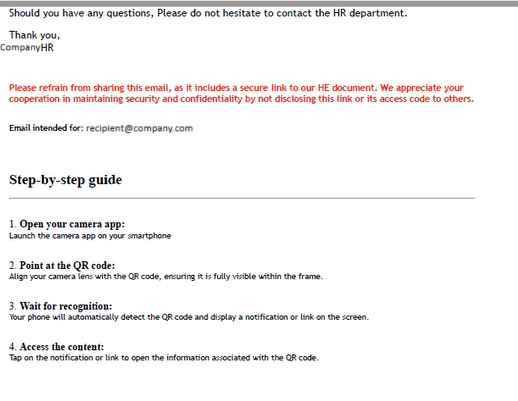
Attachment Image 4
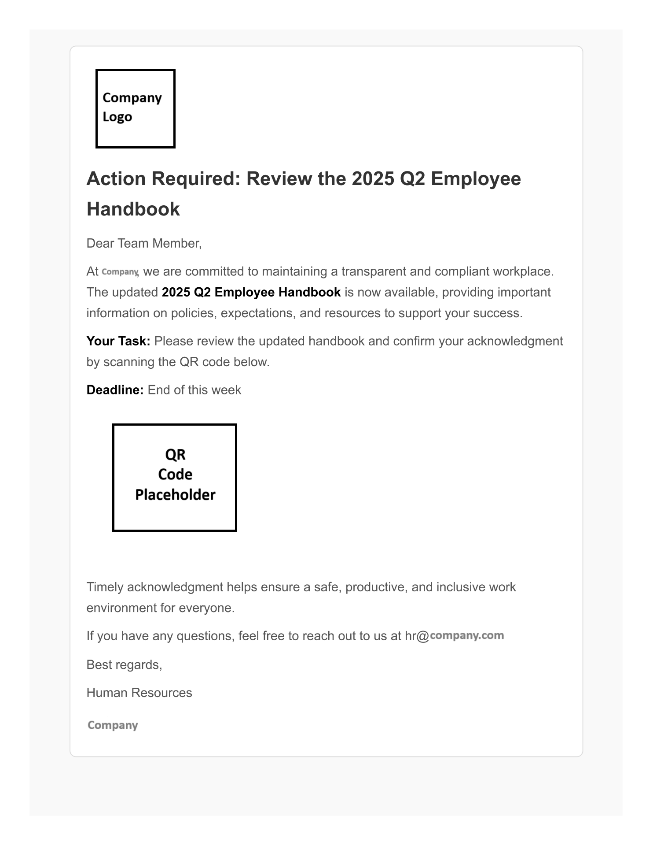
Attachment Image 5
Domain Generator
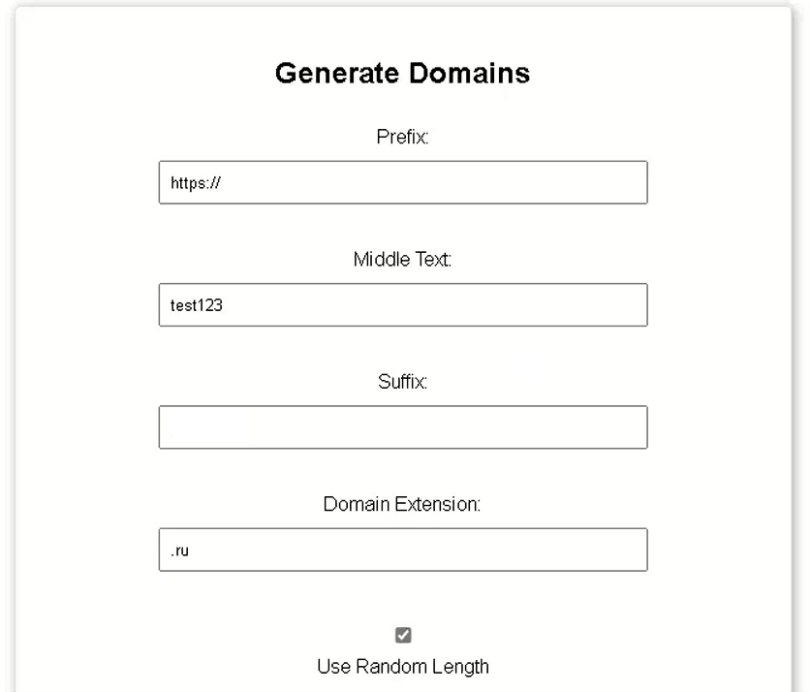
Domain Generator Image 1
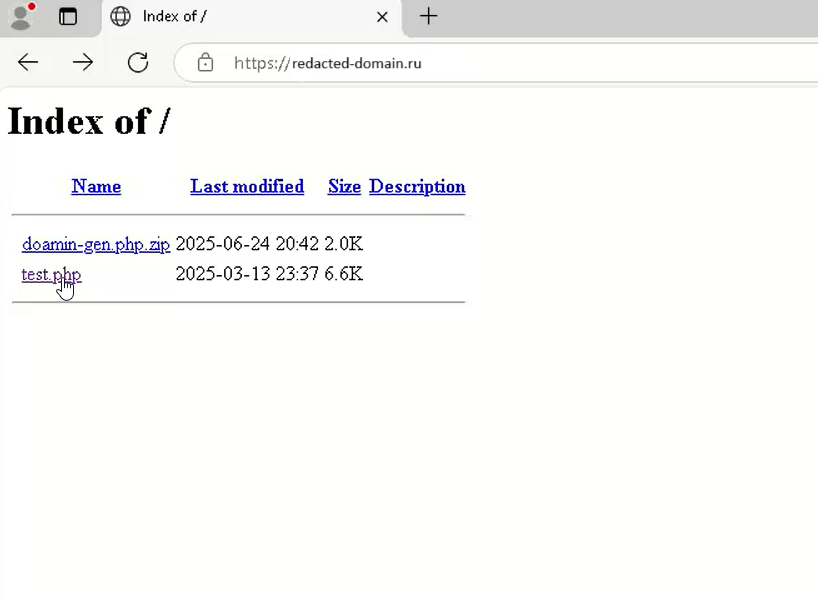
Domain Generator Image 2
Cybercrime Intelligence Shouldn't Be Siloed
Fortra® experts are dedicated to protecting organizations and the public by delivering the latest insights, data, and defenses to strengthen security against emerging cyber threats
