
The eagerly awaited release of IBM i 7.4 (V7R4) became available in June 2019, but what’s in it for system administrators? I’ve dissected the announcement and summarized it in this blog.
1. Db2 for i Services
Db2 for i Services views are incredibly powerful and flexible. Since their introduction, system administrators have been using them via both Access Client Solutions (ACS) and the 5250 green screen. Here are a handful of my favorite new views in IBM i 7.4:
SYSTOOLS.FIRMWARE_CURRENCY allows you to view installed firmware and optionally compare it against IBM’s Fix Level Recommendation Tool.
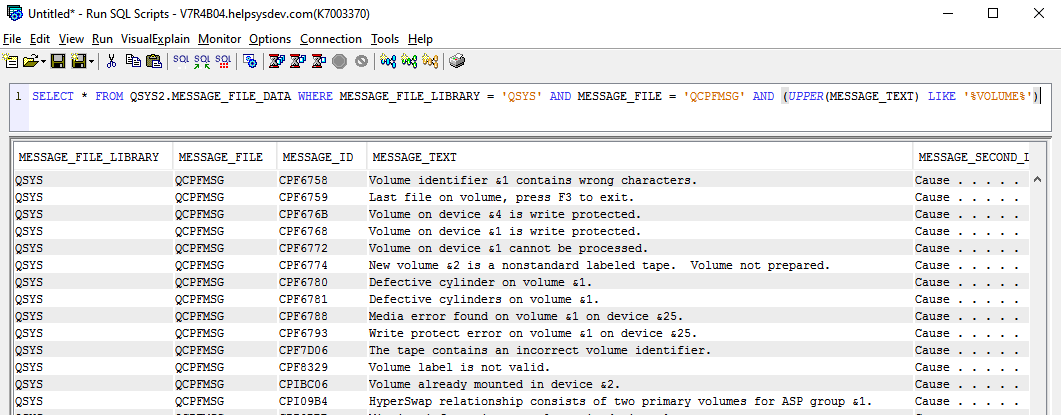
QSYS2.MESSAGE_FILE_DATA is the modern equivalent of the DSPMSGD (Display Message Description) command.
QSYS2.TIME_PROTOCOL_INFO allows you to view details about the NTP (Network Time Protocol) servers that are defined on the server.
QSYS2.ASP_JOB_INFO is the modern equivalent of the WRKASPJOB (Work with ASP Jobs) command, which is especially useful when looking for active jobs running in a defined independent auxiliary storage pool (IASP).
QSYS2.DATA_AREA_INFO is the modern version of the RTVDTAARA (Retrieve Data Area) command.
The Security Authority Collection feature was introduced in 2016 with IBM i 7.3 (V7R3), providing customers with the ability to capture data associated with the runtime authority checking that is built into the operating system. Several new views have been introduced with IBM i 7.4 (V7R4) that allow you to interrogate this captured data:
QSYS2.AUTHORITY_COLLECTION_DLO allows you to view document library objects (DLO).
QSYS2.AUTHORITY_COLLECTION_FSOBJ shows file systems in root, user-defined file systems, and QOpenSys.
QSYS2.AUTHORITY_COLLECTION_LIBRARIES displays information collected for all libraries and objects.
QSYS2.AUTHORITY_COLLECTION_OBJECT shows libraries and objects, specifically useful when the captured data is large.
Note: Db2 for i Services can be used within both Robot Monitor and IBM i Server Suites.
2. QHST Made Simple
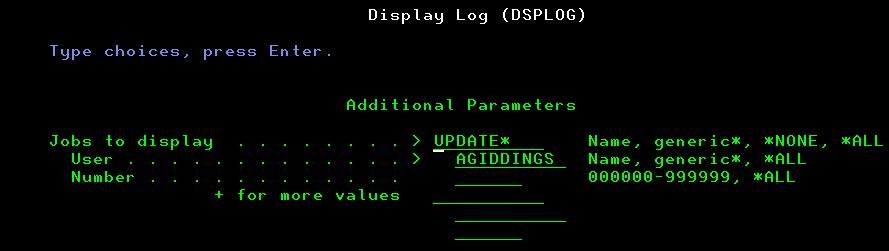
Often the go-to command for system administrators looking to analyze historical events, DSPLOG (Display Log) has been a mainstay of the operating system since day one. In IBM i 7.4 (V7R4), you can now use *ALL or a generic value for the “jobs to display” field and simply complete the user whose jobs you’re interested in.
3. Workload Capping by Job Description
Workload Groups were introduced with IBM i 7.1. (V7R1), providing system administrators with the power to subset and isolate specific workloads at the subsystem level. In turn, you can restrict the number of cores that are allocated to defined Workload Groups—particularly useful when looking to separate workloads, avoiding cross-core contamination—and key for some applications such as IBM MQ running on IBM i.
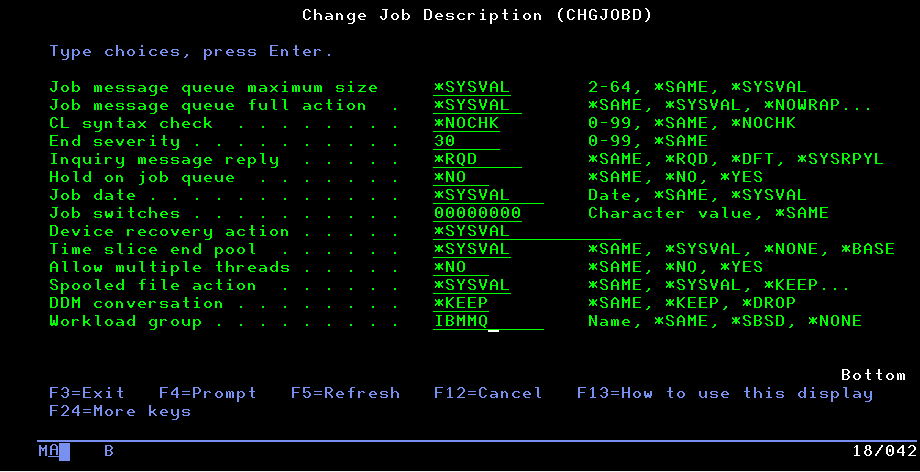
With IBM i 7.4 (V7R4), workloads can now be split by job description with the addition of a “Workload Group” parameter on the CRTJOBD (Create Job Description) and CHGJOBD (Change Job Description) commands.
4. Server Message Block (SMB) Version 3
SMB (Server Message Block) is a network file-sharing protocol typically used for access resources on remote networks. For example, a Windows client with a mapped drive to an IBM i location. SMB v3 for NetServer is faster and more secure.
5. SST User Profiles Management
SST (System Service Tool) user profiles can now be managed outside of the tool itself and through the standard IBM i command line. The below commands are now available:
CRTSSTUSR (Create Service Tools User)
CHGSSTUSR (Change Service Tools User)
DLTSSTUSR (Delete Service Tools User)
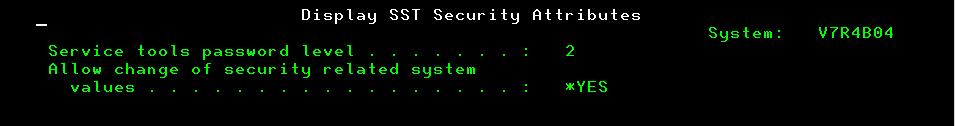
In addition, the password level and rules (of which there are 24 elements) associated with IBM i user profile passwords can now be applied to SST passwords using two new commands:
CHGSSTSECA (Change SST Security Attributes)
DSPSSTSECA (Display SST Security Attributes)
6. Access Client Solutions (ACS)
IBM i Access Client Solutions (ACS), in tandem with IBM Navigator for i, is the standard application for system administration. To coincide with the IBM i 7.4 (V7R4) announcement, a new version (1.1.8.2) of ACS has been made available. Enhancements designed to help the SQL novice include example scripts to base your next script on and a much-improved syntax aid. In addition, Db2 for i fields can be updated directly from the ACS Run SQL Scripts interface—useful but dangerous!
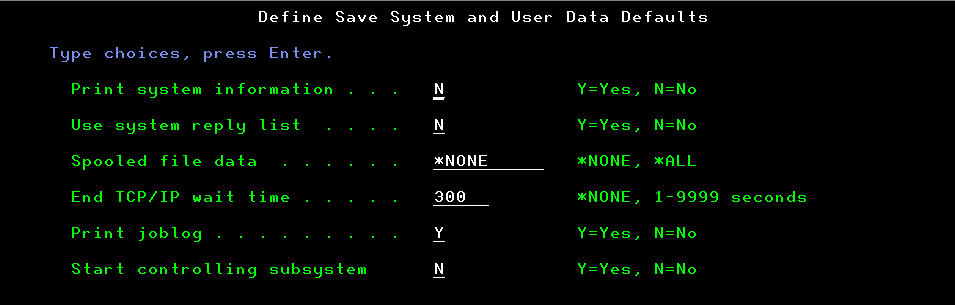
7. System Save and User Data Defaults
Option 22 “Define save system and user data defaults” from the SAVE menu now allows you to define whether you’d like the controlling subsystem to start upon completion. Being able to specify “N” is especially useful when you want to prevent users from accessing the system post save.
8. Operating System Limits
Several operating system limits have been increased including the number of disk arms allowed in basic auxiliary storage pools (ASPs) per partition—up from 2,047 to 3,999—and disk arms in independent auxiliary storage pools (IASPs) in all cluster nodes—increased from 2,047 to 5,999.
Stay tuned to the Fortra blog for more information on the latest IBM i operating system enhancements. If you’re security-minded, be sure to check out our on-demand webinar and related blog post which discusses security features with IBM i 7.4 (V7R4).
Planning an upgrade to IBM i 7.4?
It’s more work to plan an upgrade than to make the upgrade itself. Darren Anderson and IBM Champion Tom Huntington help you discover what you need to upgrade to IBM i 7.4 in this recorded webinar.