Cloud Data Protection
Unified Policy Engine
With a unified policy engine, it is easy to create, edit, and extend an authentication policy, data at rest policy, and data in motion policy across SaaS, private enterprise, and web apps.
Take the tour >
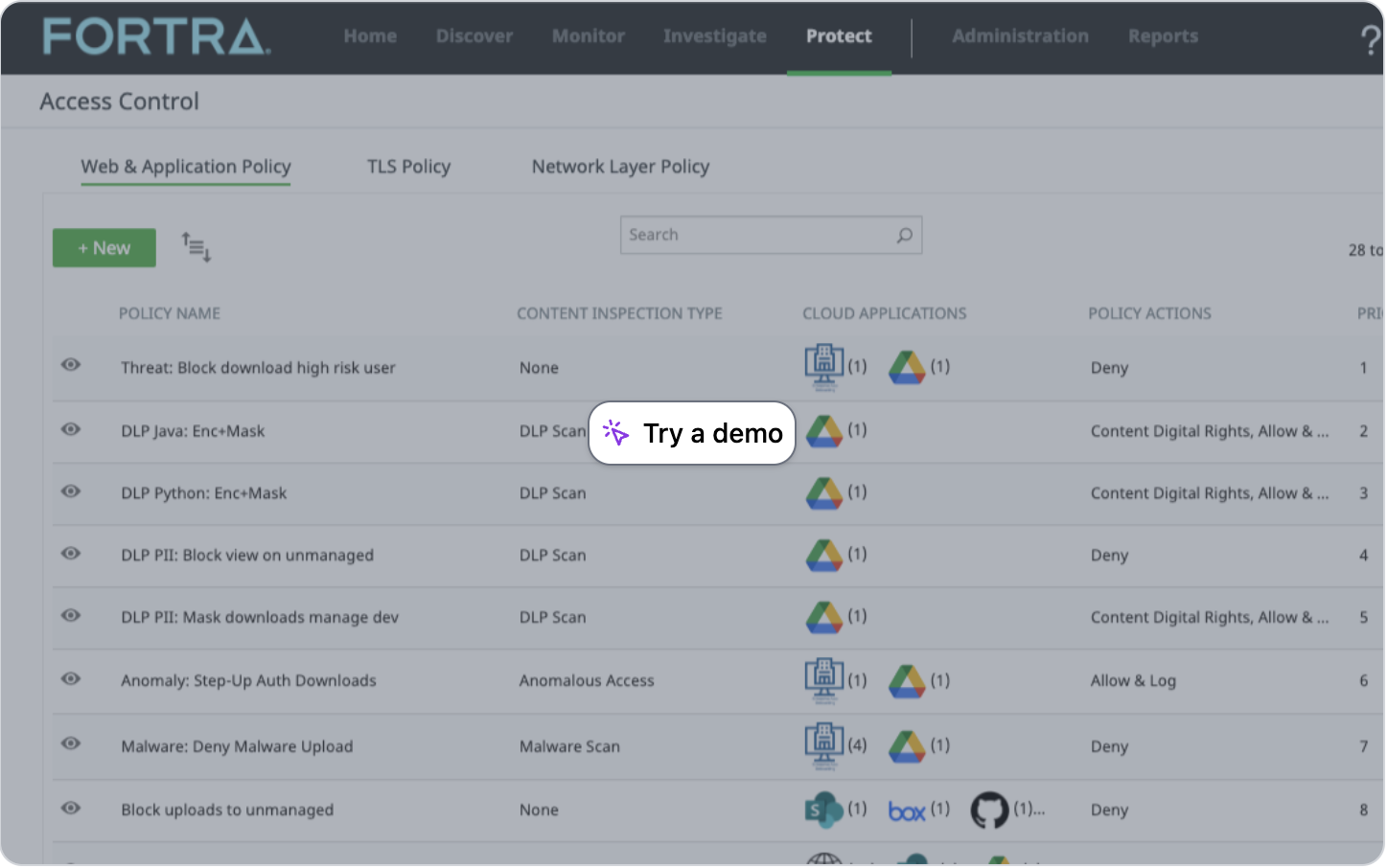
Define Policy Frameworks
Access control policies allows you to apply continuous and adaptive security controls to user activity. See how easy it is to create authentication policies, data-at-rest (API) policies, data-in-motion (Access) policies, and decryption (Dynamic DRM) policies.
Take the tour >
Monitor and Audit Activity
With a unified policy engine, you can quickly see how effective your security policies are across your SaaS, private enterprise apps, and websites.
Take the tour >
Extended Context Rules
Contextual awareness plays an important role in defining and enforcing security measures tailored to your unique environment.
Fortra SSE understands the language of modern web apps, allowing for deeper knowledge about where and how your data is being used.
Take the tour >
DRM
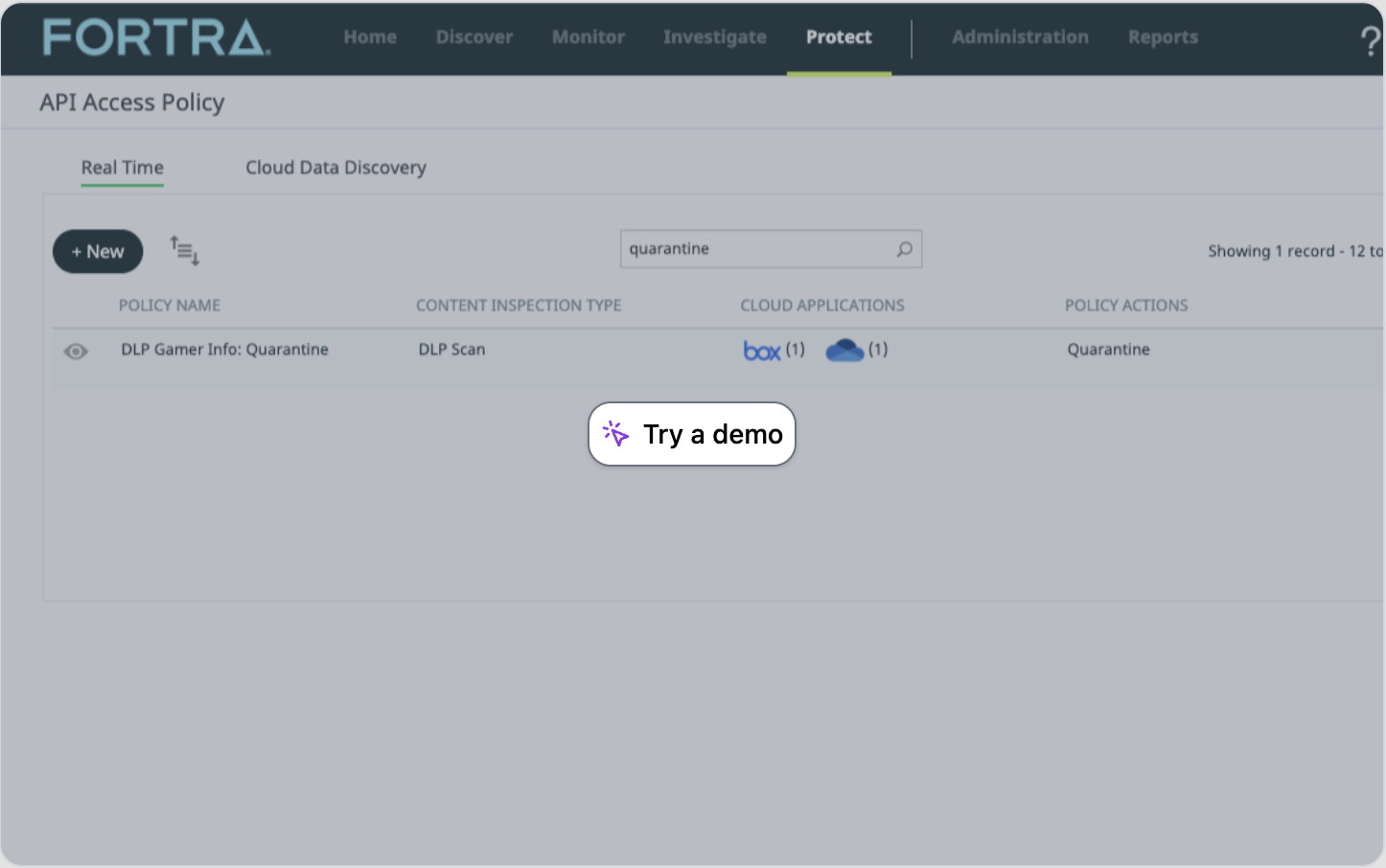
Quarantine Potential Violations
Determining a data protection strategy can often be complex. By quarantining a file, your security administrator can thoroughly review it for potential security violations before implementing any data protection measures.
Take the tour >
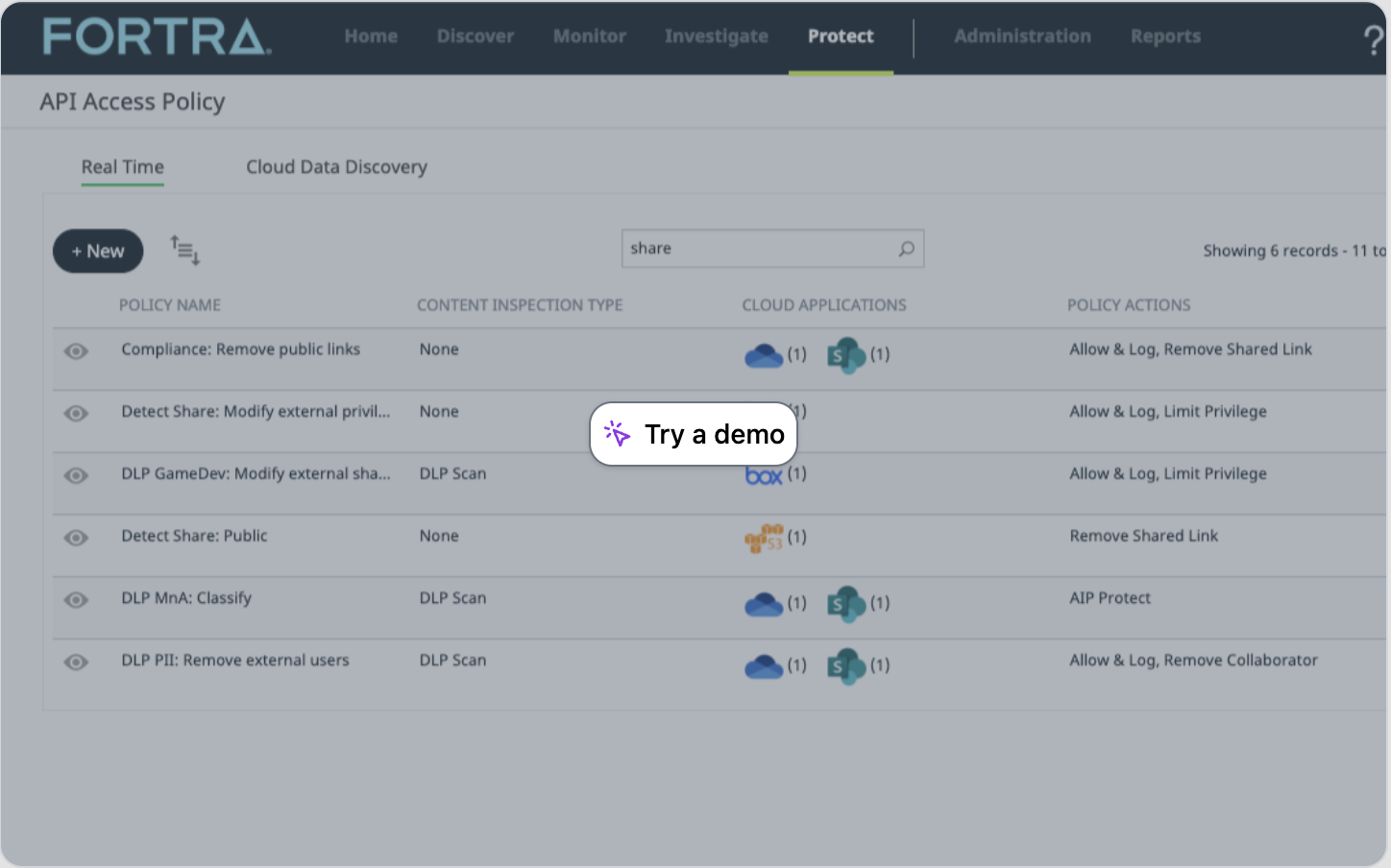
Adjust Sharing Permissions
With Fortra SSE, Digital Rights Management (DRM) extends beyond content-specific protections to include sharing permissions, and you can very easily create a policy that detects a publicly accessible share and rescind the public share.
Take the tour >
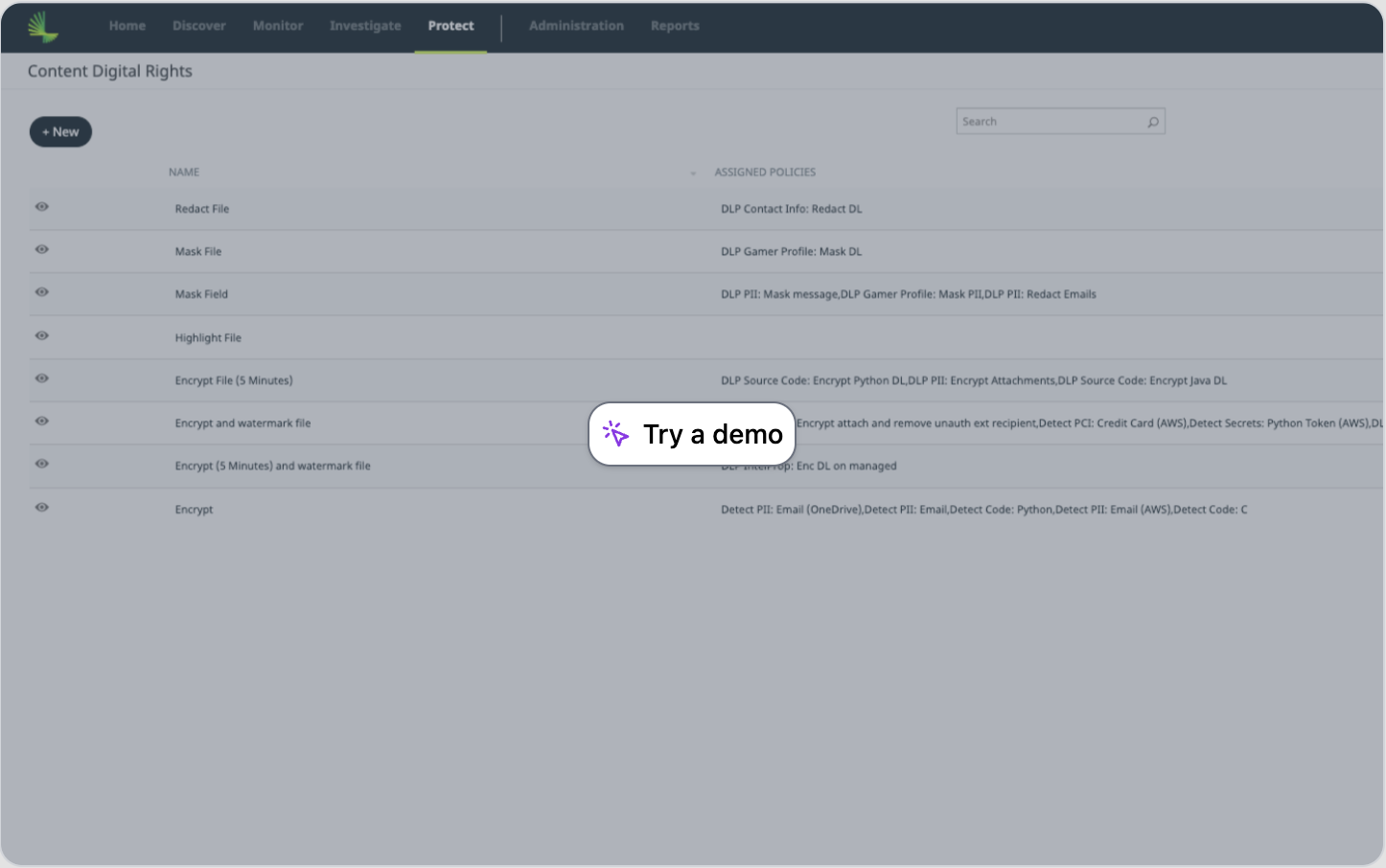
Apply Content Protections
When DLP detects sensitive information, you can automatically apply numerous Digital Rights Management (DRM) protections to prevent accidental data leakage. With content digital rights, you determine how to protect sensitive information.
Take the tour >
UEBA
Defining Adaptive Thresholds
With adaptive thresholds, you have the ability to influence the user's overall risk level. The unified policy engine can leverage a user's risk level as a contextual attribute to determine if an action should be allowed, denied, or restricted.
Take the tour >
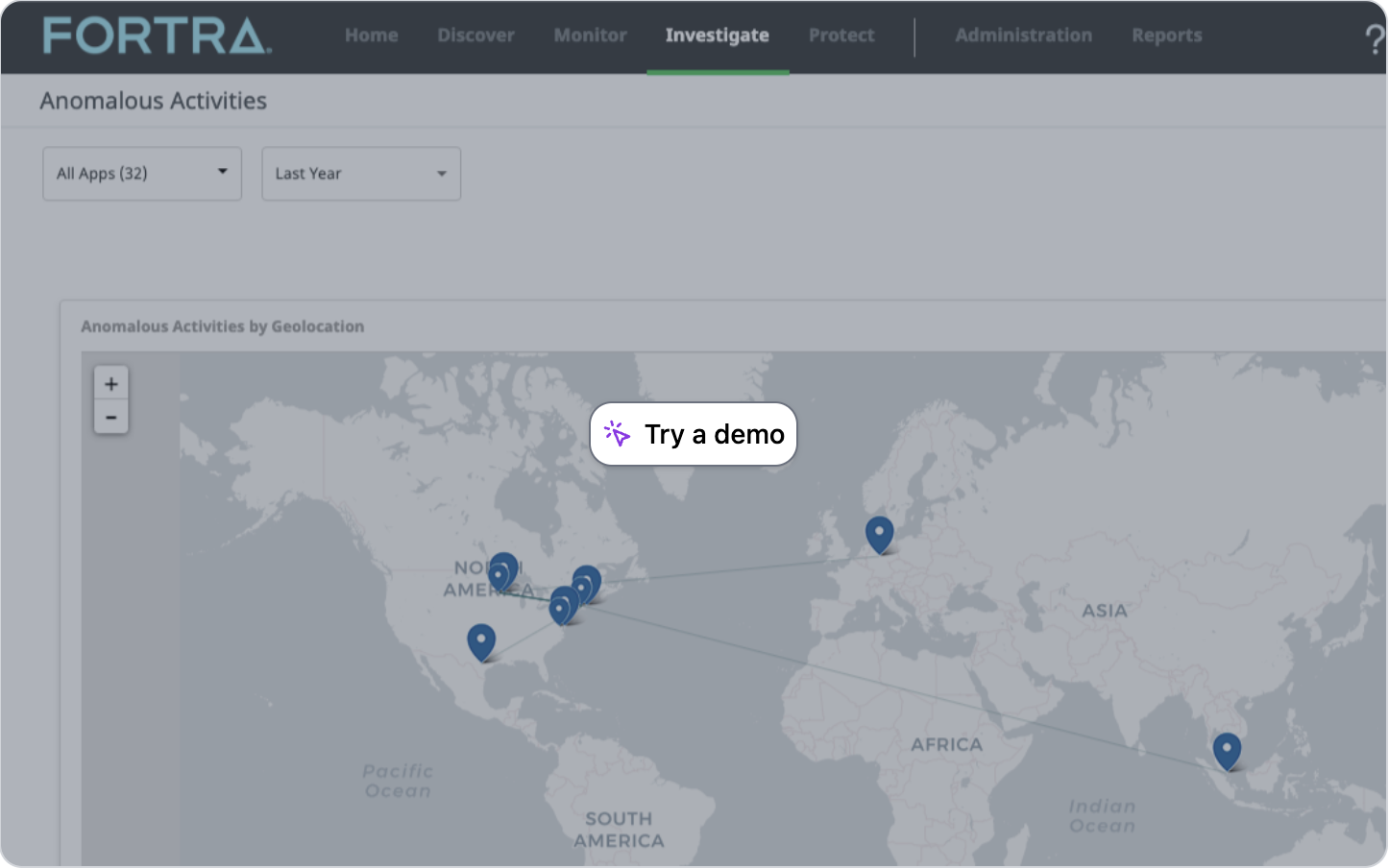
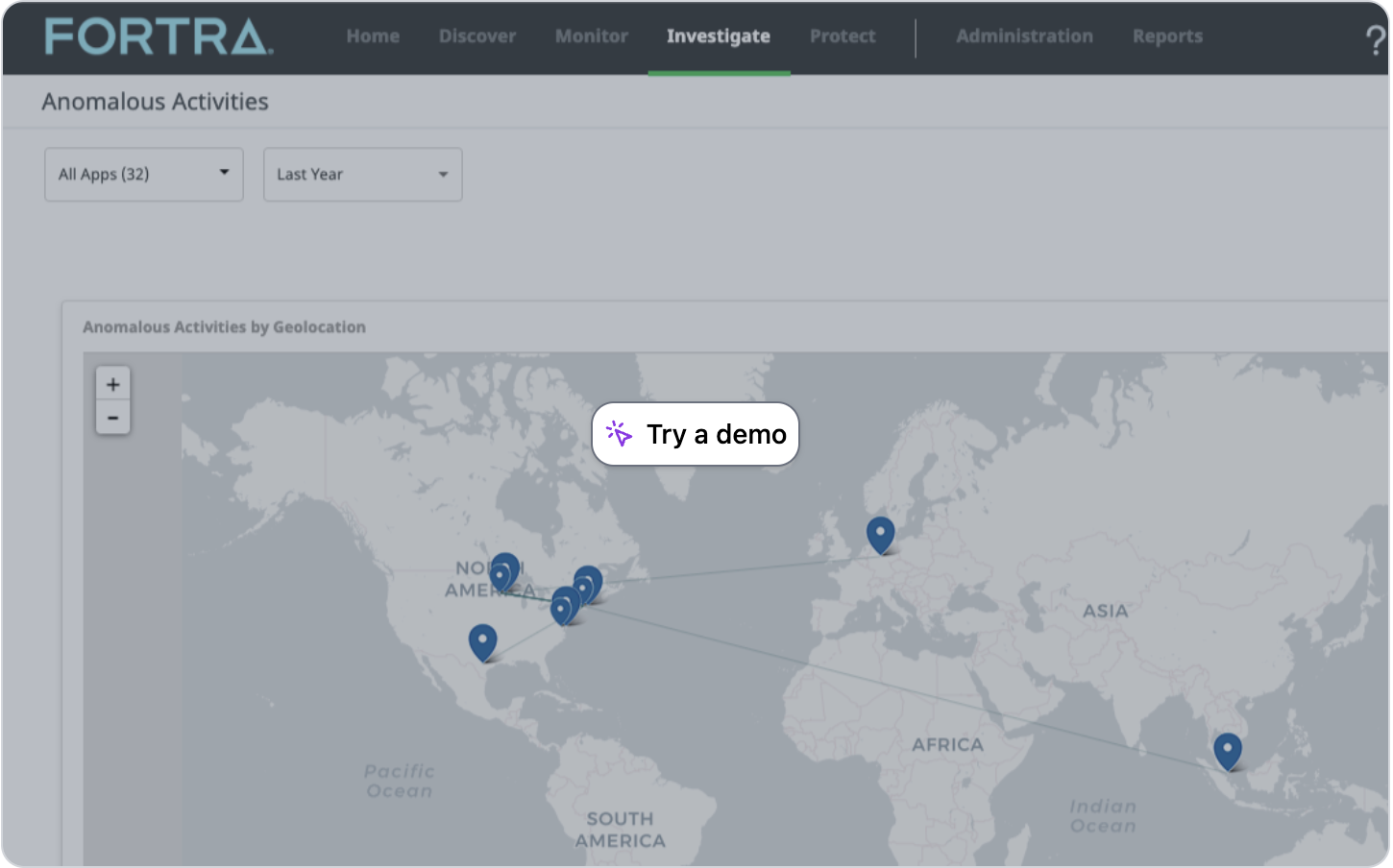
Reviewing Anomalous Activities
By leveraging machine learning, User and Entity Behavior Analytics (UEBA) monitors and analyzes user behaviors to identify anomalous activities that could indicate potential security threats. This approach enhances threat detection and also enables you to respond quickly to suspicious actions.
Take the tour >
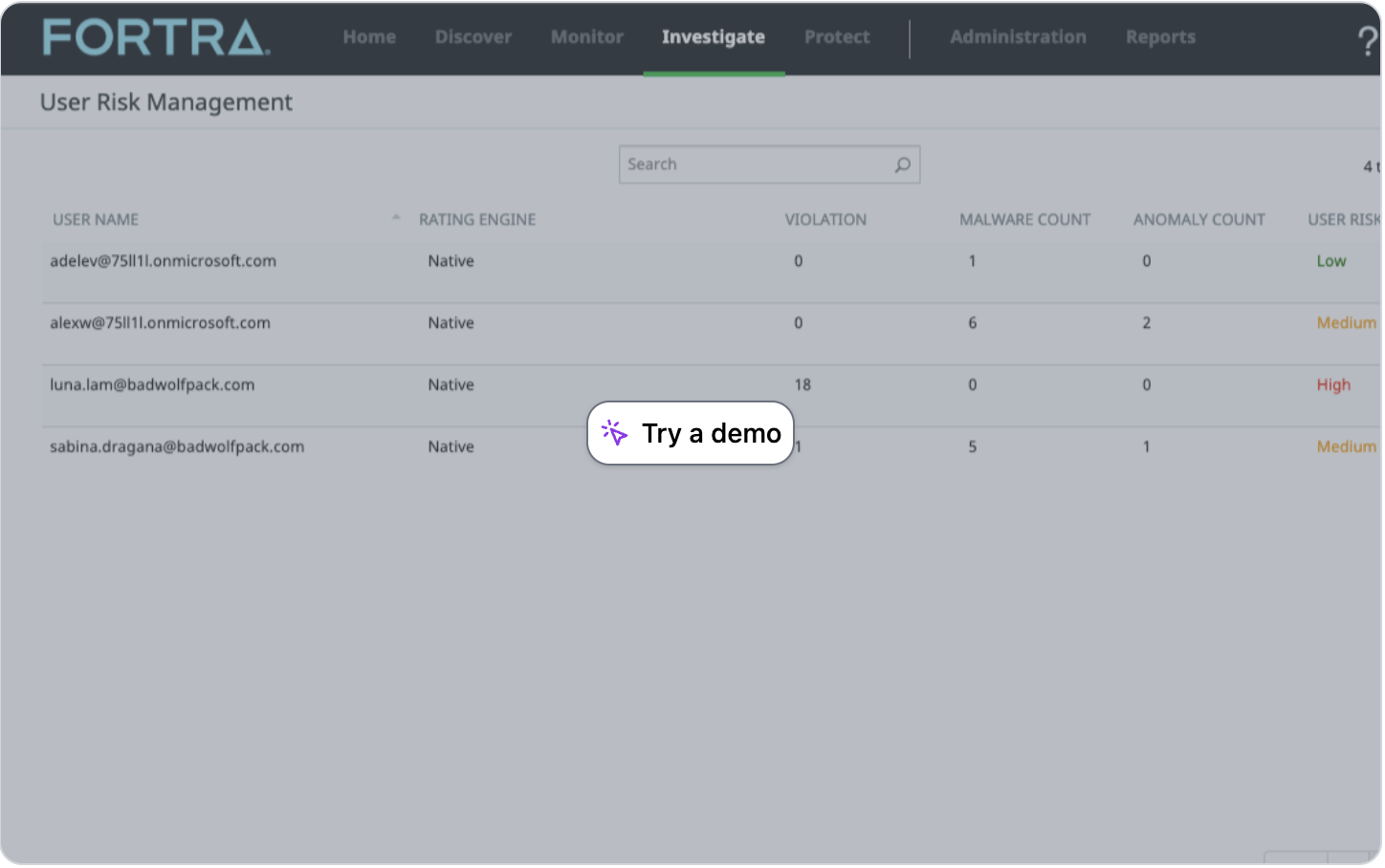
Managing User Risk
With User and Entity Behavior Analytics (UEBA), machine learning creates a profile for each user to generate a risk score that you can use as a context in your security policies.
Take the tour >
Anomalous User Behavior
The anomalous activities dashboard provides a centralized view of potential security risks within your environment. A compromised user account may exhibit a geolocation anomaly, appearing to be in multiple, geographically distant locations at the same time.
Take the tour >
DLP
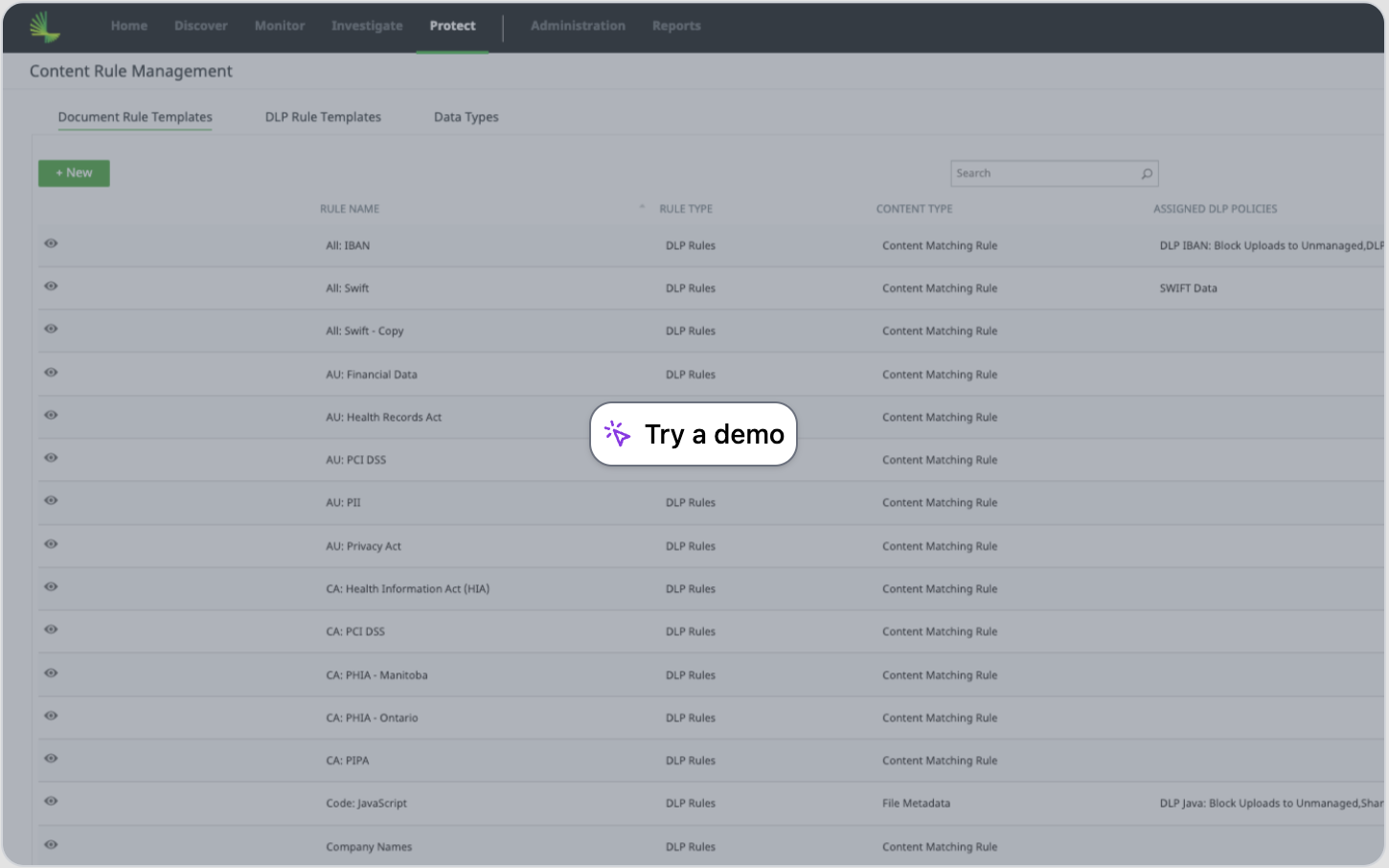
Fine Tuning Enforcement
Data loss prevention rules can be further refined to help reduce the potential of detecting false positives. When you are looking for data contained within files (unstructured data), you can leverage document rules to provide greater granularity into specific file criteria.
Take the tour >
Defining Compliance Rules
Data loss prevention (DLP) compliance rules enable you to consolidate various data types into a single configuration that meets specific regulatory standards. Start with one of our 300+ preconfigured compliance regulations or create rules specific to your data compliance needs.
Take the tour >
Discovering Data Types
Understanding your important data types is crucial for effective data loss prevention (DLP). To quickly get started with discovering your data, you can leverage a library of roughly 900 pre-configured data types.
Take the tour >
Data Compliance
Prevent Data Leaks on Social Media
Your users are sharing information on social media to build their personal brand, connect with their professional network, and showcase their expertise or achievements.
Fortra SSE can help prevent such leakage by monitoring and controlling data flow across platforms, ensuring that sensitive information remains protected from unintended exposure.
Take the tour >
Ready to Get Started?
Connect with one of our experts to discuss your business's needs.