What is AiLock?
AiLock is a ransomware-as-a-service (RaaS) operation that first came to light in March 2025. Security researchers at Zscaler noted that they had identified a cybercriminal group extorting ransoms from organisations through threats.
I'm guessing the threat was the usual story of "We've stolen your data and encrypted the files on your systems - pay up or we'll dump the information on the dark web", right?
Well, there was that. But the criminals revealed another threat in the ransom note (called ReadMe.txt) left in each impacted directory on the victims' systems.
Which was?
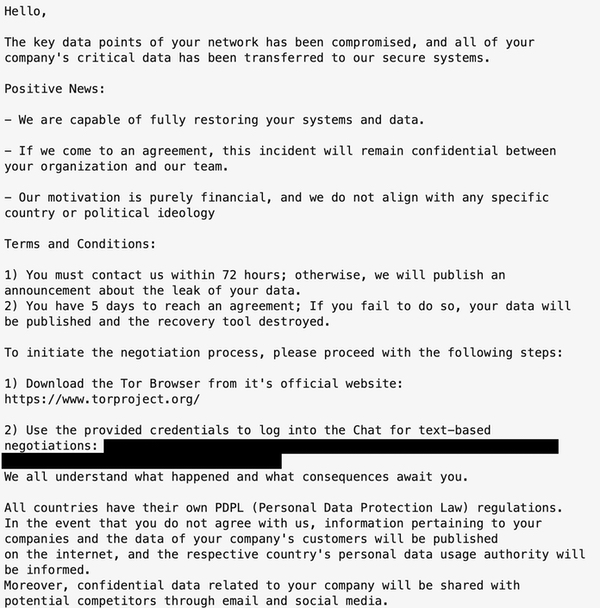
AiLock says that if you do not agree to give in to its demands, regulators will be informed about the data breach and competitors will be informed via email and social media.
All countries have their own PDPL (Personal Data Protection Law) regulations. In the event that you do not agree with us, information pertaining to your companies and the data of your company's customers will be published on the internet, and the respective country's personal data usage authority will be informed.
Nasty. In other words they are playing on a company's fear that they may fall foul of the law...
Yes, or that business rivals will make capital out of a victim's cybersecurity breach. Bad enough that your sensitive data (and potentially that of your customers and business partners) could be released onto the dark web for anyone to download, worse still, if you find yourself in a further financial pickle and battling to recover your company's reputation in the marketplace.
AiLock goes on to say that victims have just 72 hours to respond to the initial communication, and will then have five days to pay.
"If you fail to do so, your data will be published and the recovery tool destroyed."
But if you do pay up?
If you give in to AiLock's ransom demands then they say they promise to keep everything confidential, will provide "deletion logs" as supposed confirmation that stolen data has been wiped, and even provide "expert advice tailored to strengthen your company's IT infrastructure against future threats."
How very generous of them (!) Can they be trusted?
How trustworthy would you consider anybody who is prepared to break the law by hacking their way into a computer system, encrypting the data they find, and demanding money with menaces?
Good point.
Although obviously it's bad business sense for a ransomware operation not to behave as it promises. After all, who would ever pay a ransom if it became common knowledge that handing over a large pile of cryptocurrency did not result in receiving instructions on how to decrypt your network or did not stop the attackers from releasing sensitive data on the dark web anyway.
Ransomware operators like AiLock are motivated by money. Although you can never be 100% sure that paying a ransomware gang will stick to its promises, it does not make long term financial sense for them if they don't.
How will I know if my computer has been hit by the AiLock ransomware?
Aside from the ransom note left in each impacted directory, encrypted files will have had their file extension changed to ".ailock", their icons changed to a green padlock containing the word "AiLock", and the computer's wallpaper changed to the AiLock logo of a robot-like angular skull, against a background of radiating red and pink circuit-like lines.
How can my company protect itself?
Organisations who feel they may be at risk of being hit by AiLock would be wise to follow our general advice for defending against ransomware attacks, which includes tips such as: organisations that worry they might be targeted would be wise to enforce multi-factor authentication on all remote access points, disable unused RDP or VPN access entirely, and use IP allowlists or geofencing where possible.
In addition, we recommend all companies follow our general advice for defending against ransomware attacks, which includes tips such as:
- Making secure off-site backups.
- Running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- Using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- Encrypting sensitive data wherever possible.
- Reducing the attack surface by disabling functionality that your company does not need.
- Educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Beating the Business of Ransomware
Learn how to beat cybercriminals’ ransomware business.

