What is Cephalus?
Cephalus is a relatively new ransomware operation that emerged in mid-2025, and has already been linked to a wave of high-profile data leaks.
Like many other ransomware attacks, Cephalus not only encrypts but also steals sensitive data - with victims named-and-shamed on a dedicated leak site hosted on the dark web.
Where does it get the name Cephalus from?
Cephalus is a character from Greek mythology who was given a spear by Artemis that "never missed its aim." Perhaps the ransomware group is trying to convince onlookers that it similarly always hits its intended targets.
Thanks for the classics lesson. So which types of companies has Cephalus been targeting?
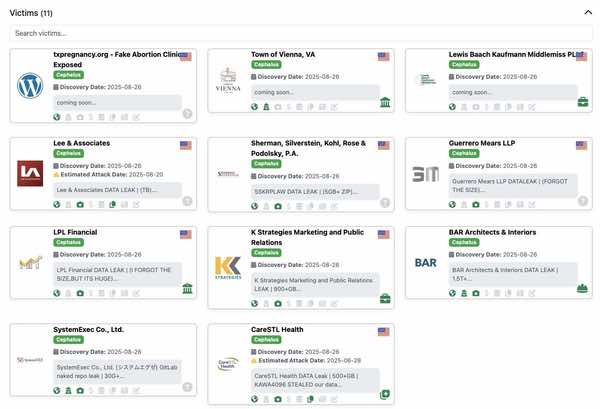
So far, Cephalus has targeted law firms, financial services, healthcare organisations, a US architectural practice, a Japanese IT firm, and marketing agencies.
Earlier this month, Cephalus claimed to have leaked over 5GB worth of data from New Jersey law firm Sherman Silverstein - including what were said to be sensitive internal files, including financial records, credentials, and legal case files.
Most recently, Cephalus has added Vienna in Fairfax County, Virginia to its victim list - although there has been no official confirmation of the attack on the town's official website. A list of Cephalus's recent claimed victims can be found on its leak site.
Nasty. How does Cephalus break into a network?
Cephalus compromises systems by leveraging Remote Desktop Protocol (RDP) accounts that have not been secured with multi-factor authentication (MFA).
If the malicious hackers have already managed to gather credentials to remotely log in via RDP, the lack of MFA makes it easy for the attackers to slip through.
And when it's in...?
According to a report from researchers at security firm Huntress, Cephalus takes an unusual approach to launching its ransomware payload.
Cephalus drops a real program from security firm SentinelOne (SentinelBrowserNativeHost.exe) into the targeted computer's Downloads folder. That program, which security software is likely to assume is legitimate and safe, is tricked into sideloading a malicious DLL, that runs another file called data.bin that contains the actual ransomware code.
Why would they do all that?
It's an attempt by the attackers to evade detection by security software.
Sneaky. What else does Cephalus do?
Like many other flavours of ransomware, Cephalus will delete Windows Shadow Copy files - which a company might hope to recover their data from. In addition, Cephalus stops and disables Windows Defender from running, allowing it to encrypt a victim's files without resistance.
How will I know if my computers have been hit by Cephalus?
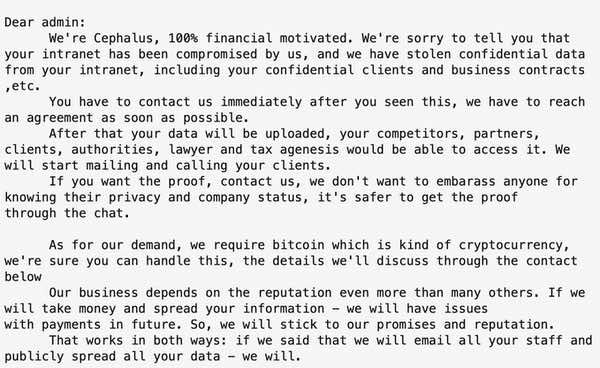
The first thing you might notice is that Cephalus has locked you out of your files, and changed their names to have a ".sss" extension. In addition, a ransom note will have been left by the attackers which reads in part:
Dear admin: We're Cephalus, 100% financial motivated. We're sorry to tell you that your intranet has been compromised by us, and we have stolen confidential data from your intranet, including your confidential clients and business contracts ,etc.
How can my company protect itself from ransomware like Cephalus?
Organisations who feel they may be at risk would be wise to follow Fortra's general advice for defending against ransomware attacks, which includes tips such as ensuring MFA is enabled on all remote access points, disabling unused RDP or VPN access entirely, and use IP allowlists or geofencing where possible.
In addition, it's recommended that all companies follow best practices for defending against ransomware attacks, which include tips such as:
- Making secure off-site backups.
- Running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- Using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- Encrypting sensitive data wherever possible.
- Reducing the attack surface by disabling functionality that your company does not need.
- Educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Cybercrime Intelligence Shouldn't Be Siloed
Fortra® experts are dedicated to protecting organizations and the public by delivering the latest insights, data, and defenses to strengthen security against emerging cyber threats.

