What is the Warlock?
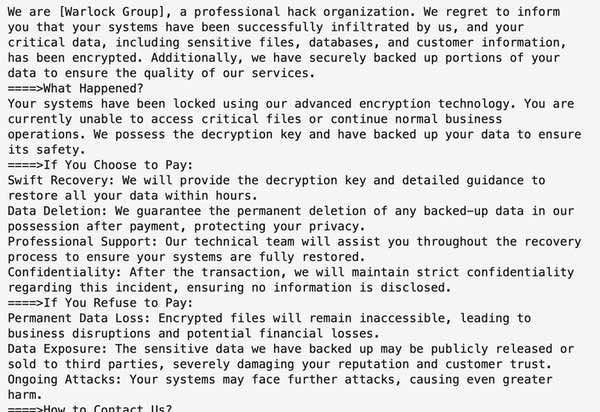
Warlock is a ransomware operation that emerged in 2025, combining the traditional "double extortion" tactics of encrypting victims' files so they cannot be accessed, and threatening to release data stolen from the company's network.
Nasty, but sadly not that unusual.
Unfortunately, that’s right.
The Warlock ransomware group seems to have stepped up its attacks in recent months, hitting a number of organisations including government agencies and departments.
Victims have included a water and waste service authority in Portugal, a government education agency in Croatia, and BTHK - the Turkish IT and communications authority.
So why is it in the news now?
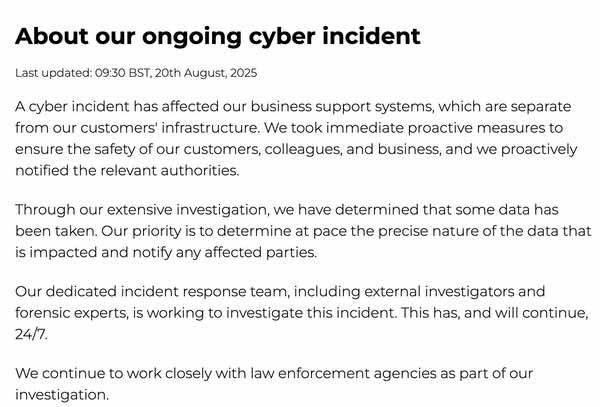
On August 12, UK-based telecoms firm Colt Technology Services was hit by a cyber attack which has caused some of the company's systems to be taken offline for multiple days.
The attack saw the firm advise its customers to not rely upon its its online portals for communication, but instead use email and phone instead - and to expect a slower-than-normal response.
Colt Technology Services said that it has informed the authorities about the incident, and that it has staff working around the clock to restore normal operations.
And this was Warlock?
Colt hasn't shared details about the nature of the cybersecurity incident it is experiencing or who is behind it, but someone claiming to represent the Warlock ransomware group has posted on a dark web forum that they are offering to sell one million of Colt's stolen documents for US $200,000.
The data is said to include financial, customer, and employee data, as well as internal emails. Sure enough, WarLock's data leak site on the dark web includes an entry for Colt, and has announced that it is auctioning the data to whoever might want it.
So how do we think the Warlock gang might have broken in?
Security researchers believe that the malicious hackers may have made entry into Colt's systems by exploiting the CVE-2025-53770 Sharepoint vulnerability, which Microsoft has said is being actively used by attackers.
Nasty. Presumably patches are available?
Yes, and Microsoft is advising customers to apply them immediately to ensure that they are protected.
Microsoft experts published an article last month sharing detailed intelligence about how the Warlock ransomware has been deployed by exploiting the software flaws, and how customers can mitigate and protect themselves.
Of course the hackers don't have to use that particular method to break in, right?
Correct. Malicious attackers can use any number of different methods to infiltrate organisations and plant ransomware on their systems.
If you don't have adequate defences in place, there is a chance that you could come into your office one day to be greeted by a ransom note from a group like Warlock.
So what should my business do to defend itself?
Organisations who feel they may be at risk of being hit by the likes of Warlock would be wise to follow Fortra's general advice for defending against ransomware attacks, which includes tips such as enforcing multi-factor authentication, running up-to-date security solutions, and keeping software patches up-to-date.
In addition, it's recommended that all companies follow best practices for defending against ransomware attacks, which include tips such as:
- Making secure off-site backups.
- Using hard-to-crack unique passwords to protect sensitive data and accounts.
- Encrypting sensitive data wherever possible.
- Reducing the attack surface by disabling functionality that your company does not need.
- Educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Cybercrime Intelligence Shouldn't Be Siloed
Fortra® experts are dedicated to protecting organizations and the public by delivering the latest insights, data, and defenses to strengthen security against emerging cyber threats.

