Introduction
It’s hard to beat an enemy you don’t understand. Diving into enemy territory and learning the techniques, tactics, and the processes by which they launch successful cyberattacks can mean the difference between stopping them in their tracks and meeting them unprepared.
The cyber kill chain is used by both cybercriminals and defenders alike, albeit for different purposes, to guide them through the various stages of an online attack. Understanding how it works and its relevance in the cybersecurity landscape today can position defenders to take full advantage of the insights it affords.
What Is the Cyber Kill Chain?
The cyber kill chain refers to the interdependent, step-by-step processes that threat actors take to successfully execute a cyberattack. Coined by Lockheed Martin back in 2011, the phrase is derived from a longstanding military term, “kill chain,” which outlines the process by which a military target is attacked.
How Does the Cyber Kill Chain Work?
Also referred to as the cyber attack chain, the cyber kill chain comprises a series of interconnected actions which are dependent upon the step before. The “chain” must be completed in that order, and an interruption at any point could result in the dissolution of the whole thing. From a defender’s perspective, that is what we are counting on.
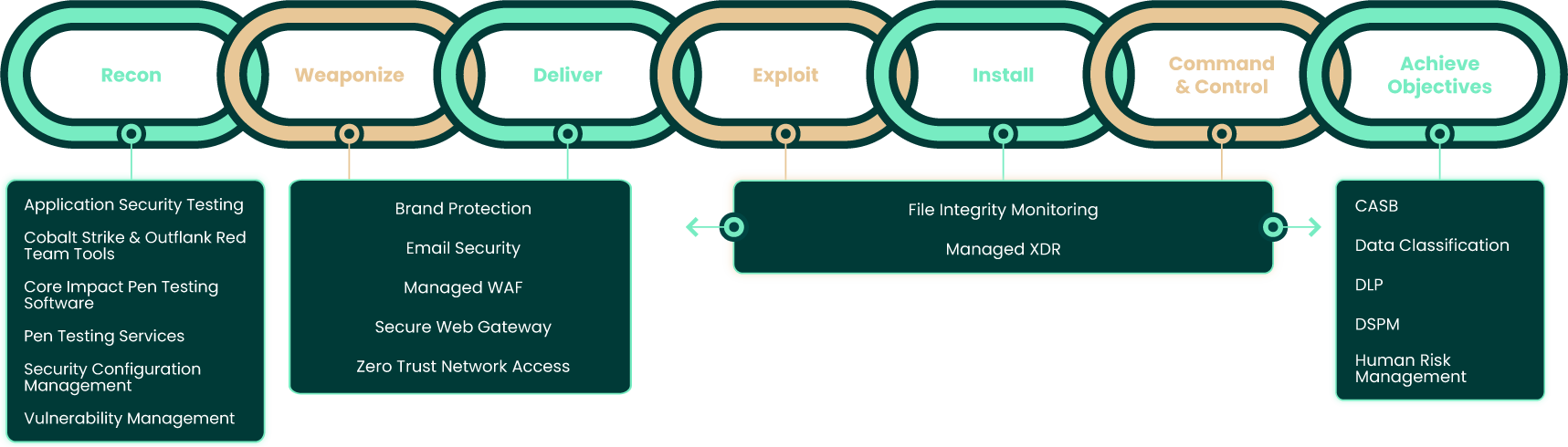
There are seven stages to the cyber kill chain:
The Impact of the Cyber Kill Chain on Cybersecurity Today
Understanding the various steps in the cyber kill chain can help security professionals know where an attacker has been, where they are planning to go, and how to stop them along the way. It is a blueprint that every attacker must follow to successfully pull off an attack, and yet because it is inescapable, it also makes attackers’ next actions transparent and therefore, easier to defend.
How to Use the Cyber Kill Chain?
Cybersecurity professionals can leverage the cyber kill chain in two primary ways:
Identify and Stop Attacks
To identify and stop attacks, because instances of compromise from ransomware to social engineering often follow the path of the cyber kill chain.
Bolster and Test Defenses
To bolster and test defenses. Once a vulnerability has been patched or a weakness remediated, offensive security teams can follow the cyber kill chain to see if that weakness is still exploitable by attackers or if it has been successfully fixed.
Think of the benefit of understanding the individual steps of a cyberattack. A much-used adage advises us to “know your enemy.” What could be more valuable knowledge than understanding their next malicious steps?
Limitations of the Cyber Kill Chain
However, the cyber kill chain doesn’t catch all exploits, especially as threats penetrate the cloud and infiltrate the web. One criticism of the cyber kill chain is that it does best at defending against perimeter-based attacks like malware and is weakest against credential-based attacks, insider threats, and web-based attacks. This may be true, but when things like ransomware still affects 92% of all industries and play a role in 32% of breaches (according to the Verizon 2024 Data Breach Investigations Report), using the cyber kill chain to tamp down on these types of threats is still highly useful.
Leveraging the Cyber Kill Chain with Fortra Solutions
Fortra solutions specialize in breaking the attack chain, disrupting threat actors’ in-progress plans and thwarting instances of compromise.
Meeting attackers at each step, Fortra pre-emptively severs the cyber kill chain by:
Thwarting Reconnaissance
Preventing Weaponization
Exposing Installation
Blocking Malicious Actions
For organizations today, understanding the cyber kill chain is not just about understanding attackers, but understanding how to stop them in their tracks, no matter what stage of the attack they’re in.
We Break the Attack Chain
Fortra provides advanced offensive and defensive security solutions covering the entire attack chain, enabling our customers to test, simulate, and strengthen their defenses in real time. Contact us today to learn more.