What is File Integrity Monitoring (FIM)?
Every cyber incident begins with a single change, whether it occurs via malicious intent or human error. File integrity monitoring is the process of detecting changes in digital systems that indicate potential exposure and remediating those changes before a cyberattack can succeed. The core purpose of FIM is to establish and maintain the integrity of your organization’s digital environment so that you can reliably assess and respond to risks as they arise in real time. FIM is also a crucial part of regulatory compliance, providing proof of alignment with compliance policies.
The Importance of File Integrity Monitoring
FIM has expanded to encompass much more than just files and is now one of the most important security controls relied upon by large enterprises, organizations, and agencies worldwide. Implementing FIM software shrinks the attack surface, promotes operational efficiency, and aligns systems with regulatory compliance standards.
Fortra's Tripwire introduced FIM to the cybersecurity community more than 25 years ago, and it quickly became a requirement of the Payment Card Industry Data Security Standard (PCI DSS). In the time since, it has also become a requirement of North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP), the Sarbanes-Oxley Act (SOX), and the Health Insurance Portability and Accountability Act (HIPAA).
How FIM Works
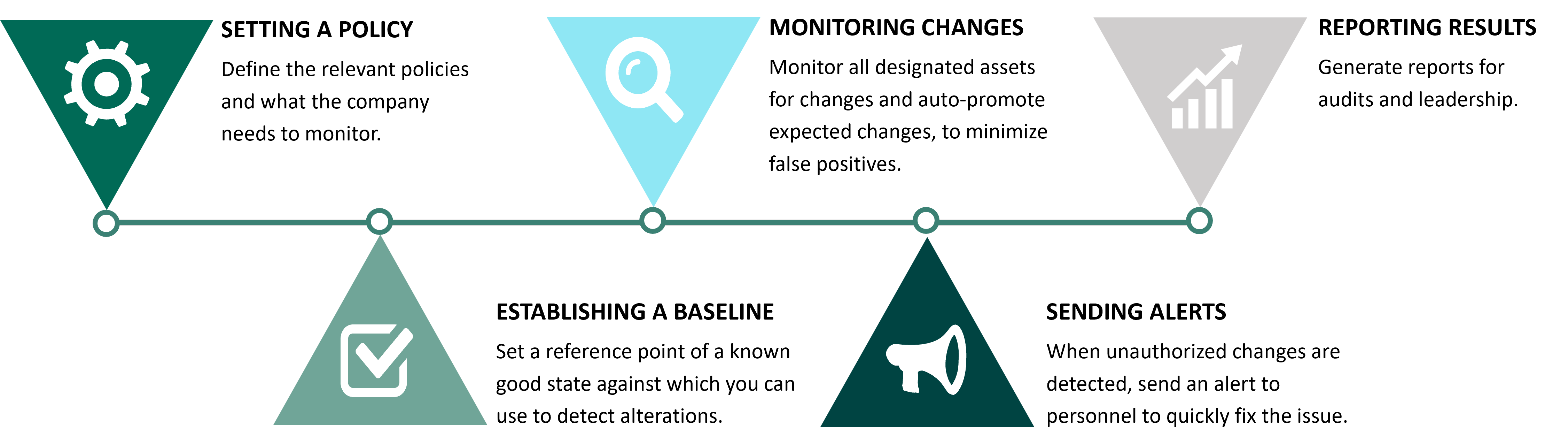
The file integrity monitoring process consists of five essential steps:
Designate your policies: The first step of implementing FIM software is choosing which policies you will enforce across your digital environment. These can be regulatory requirements, vendor guidelines, best practice frameworks, or internally created policies.
Set a Secure Baseline: In order to monitor for suspicious or unauthorized changes, your FIM software first needs to capture a reference point of your systems and assets in a trusted state, known as a baseline.
Monitor for change: After establishing a detailed baseline, you can use your file integrity monitoring software to detect deviations from that baseline across your organization while promoting expected changes automatically to reduce noise.
Alert on Suspicious Changes: When unauthorized or otherwise suspicious changes are detected by the software, it alerts the right personnel with instructions for remediation.
Generate Reports: FIM reporting is an important aspect of audit preparation, used to provide proof of compliance and track security hardening progress over time.
File Integrity Monitoring Benefits
Reduces breach frequency and severity
Provides visibility into your current attack surface
Gives you situational awareness and change context
Automates compliance enforcement and audit reporting
Boosts operational efficiency with minimal downtime
File Integrity Monitoring Best Practices
FIM for Different Operating Systems
Large, complex organizations rely on an assortment of different operating systems, making it essential to have a file integrity monitoring solution with the adaptability to monitor your current systems and support room to expand. Whether it's AIX, Amazon, VMware, or Windows, ensure your FIM solution can enforce continuous monitoring across your chosen operating systems.
Tripwire’s File Integrity Monitoring Solutions
Tripwire Enterprise
Tripwire® Enterprise pairs the industry’s most respected FIM with security configuration management (SCM) to provide real-time change intelligence and threat detection. For the compliance officer, it delivers proactive system hardening and automated compliance enforcement—resulting in a reduction of audit cycles and cost.
Tripwire ExpertOps
Tripwire ExpertOps provides file integrity monitoring (FIM), security configuration management (SCM), and vulnerability management (VM) as a managed service to arm you with the solution operation, support, and advice you need to stay compliant and reduce your attack surface.
Tripwire is your ally in integrity management.
Simply request a demo here to get started.