Remember when you learned how to drive? Undoubtedly whoever taught you the rules of the road explained the danger of “blind spots”—those triangular areas on either side of the car in which your peripheral vision fails you. Unless you look over your shoulder while changing lanes, you could all-too-easily hit an unsuspecting occupant of the blind spot zone.
In the network management world, blind spots are just as dangerous. Getting total network visibility remains one of IT’s greatest challenges. Without due diligence to prevent blind spots, you’re looking at potential device failures, performance issues, unhappy users/customers, and even serious security threats. Thankfully, knowing what causes blind spots can help us prevent them.
What Causes Network Blind Spots?
1. A breakdown in IT teamwork
The “silo effect—when departments or teams fail to communicate effectively—also applies to IT teams. If you’re a larger organization, better information and data-sharing between network, security, and systems management teams leads to better business decisions and compliance with IT policies.
2. Unapproved IT
When IT staff does things their way instead of following company policies, bad things can happen. Even well-intentioned network admins can contribute to network blind spots. Making sure everyone follows company standards for adding new devices and storing data will protect you against greater troubles down the line.
3. Incomplete device inventory
Documenting every new device in the network can be a pain, especially if you’re doing it manually, but it’s a must. Without this information, it is very difficult to identify who’s responsible for devices, where they’re located, and what’s going on with your network operations.
4. Insufficient monitoring
All too often, IT teams fail to monitor these elements:
- Mobile technology: As more mobile devices connect to the network, it’s critical to keep an eye on them. Mobile devices are often responsible for unexpected increases in network traffic. That’s why the industry has developed unique tools geared toward mobile device management and support.
- Virtualized environments: Without intentionally monitoring virtual elements, it’s easy to miss the virtual traffic that they are driving.
- Internet of Things devices: If it has an IP address, you need to monitor it. As businesses acquire more interconnected technology, they need to keep network professionals accountable to monitor and support it.
- Encrypted traffic: More devices have a way to encrypt and decrypt data, but it can be difficult to track. As the number of websites that enforce SSL grows, using tools that can monitor encrypted traffic will help prevent dangerous traffic from slipping by unnoticed.
How to Prevent Network Blind Spots
Be on your IT game
Install updates regularly. Maintain hardware. Be proactive about updating and taking care of your IT infrastructure. The moment you stop could be the very moment you inadvertently create a security vulnerability.
Maintain an up-to-date network map
With a current visual of your entire network, including a way to detect new devices as they connect, you’ll be much less likely to be surprised by any out-of-the-ordinary network activity. Network mapping also helps you find devices faster when issues do arise, so problems can be resolved more quickly.
Monitor your network
Network monitoring remains one of the strongest defenses against blind spots. Monitor core, business-critical devices for sure, but also mobile technology, virtual elements, applications, Internet of Things devices… if you can monitor it, do! Regular monitoring helps establish baselines so surges and decreases in traffic are more apparent.
Analyze flows data
Analyzing flows data—basically, any data that is transferred between two hosts with the same characteristics—can help you maintain total network visibility. Using protocols like NetFlow, sFlow, and J-Flow can give you insight into the traffic that is flowing across your network, displaying possible DDoS attacks, uncharacteristic bandwidth spikes, or traffic from unusual sources, so you’re never in the dark about the traffic on your network.
Set up network notifications
Many monitoring tools have alert capabilities that will notify you when traffic exceeds preset thresholds. That way, whether you’re at your workstation, at lunch, or walking around the office, you’ll get wind of potential issues immediately and can begin resolving before they progress into something worse.
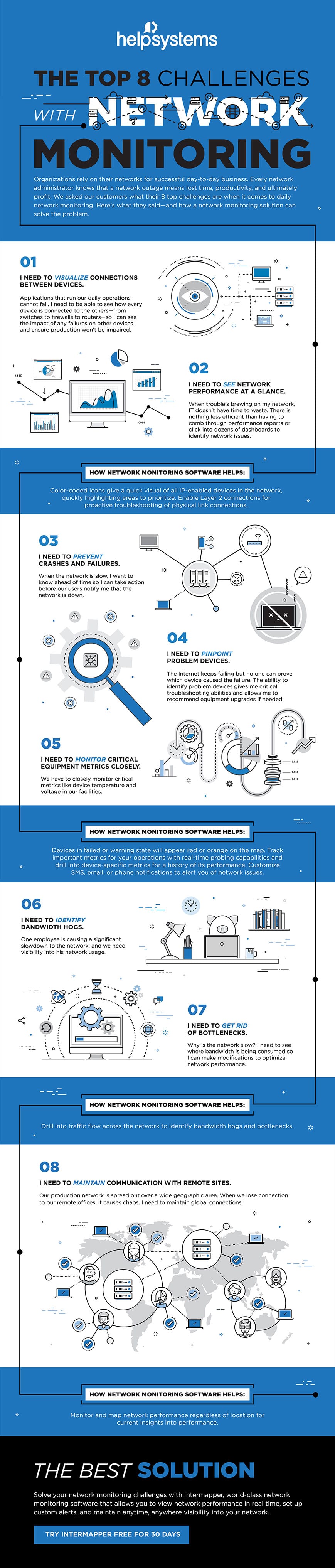
The Top 8 Challenges with Network Monitoring
What network monitoring challenges keep you up at night? Is it difficult to see exactly who is consuming all the network bandwidth? Are you struggling to identify the faulty device that keeps bringing the network down?
You’re not alone. IT professionals all over the world share similar network management challenges.
Check out the infographic below for eight of the most common challenges and how network monitoring tools take care of them.
⤓ PRINT ⤓
Survive and Succeed at IT
Learn how your peers succeed every day at work. The Network Professional's Survival Guide is full of their advice, tips, and favorite tools.
