1. Introduction & Survey Highlights
3. IT Initiatives & Trends (current page)
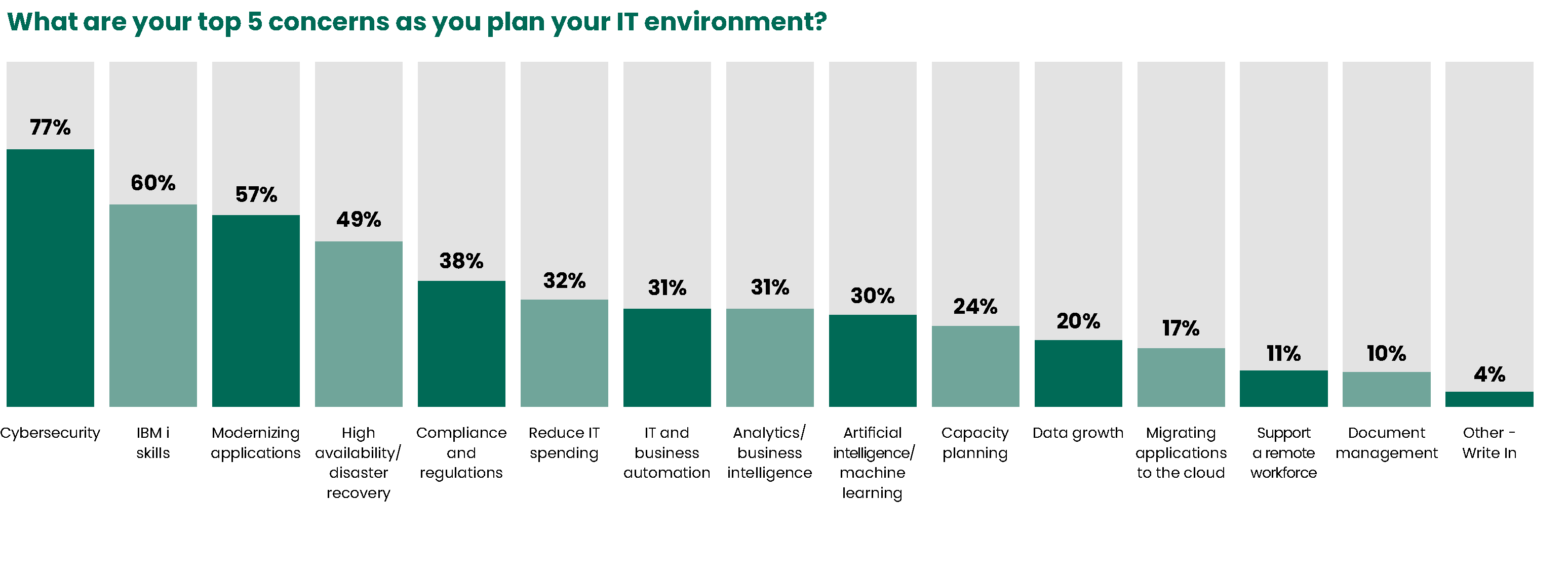
Top Concerns
Cybersecurity ranking as the number one concern is nothing new – it has held that spot since 2017. In 2025, 77% of respondents rank cybersecurity as a top IT concern, just two percentage points lower than the record high of 79% set last year. Clearly, IT leadership remains aware of the devastating ramifications of suffering a cyberattack.
IBM i skills comes in next, closely followed by modernizing applications. This is likely related to the retirement of key IBM i personnel and organizational efforts to replenish IBM i skills and modernize applications to maximize current expertise. We encourage you to read our guides on what to do when your AS/400 talent retires and what to consider before moving to the cloud.
High availability/disaster recovery fell considerably from 63% to 49%, while compliance and regulations rounds out the top five at 38%. As industries like healthcare and finance continue to tighten regulations and expand cyberinsurance coverage, IBM i is brought more into the scope of organizations’ compliance efforts. For those who expressed concern over their HA/DR processes, you have options, and this guide is a good place to start.
Outside of the top five, artificial intelligence and machine learning rose from 18% to 30% — indicating a legitimate and growing interest in embedding these revolutionary technologies into everyday processes. Additionally, capacity planning jumped from 10% to 24%, showing a renewed need for improved planning resources, application performance, and capacity planning expertise.
RECOMMENDATION:
It’s crucial to continue gaining a deeper understanding of the cybersecurity environment. Fortra’s State of IBM i Security Study provides exclusive insight into the tools and strategies organizations are using to secure IBM i and where systems are most often left vulnerable. You can also check out the IBM i home page to discover all the different ways the platform facilitates modernization.
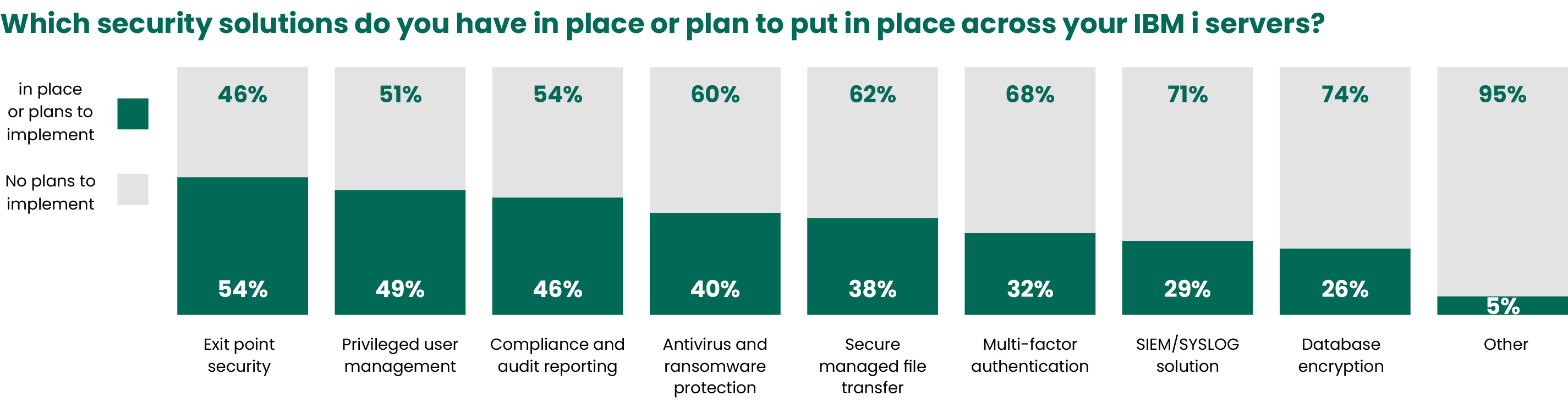
Cybersecurity
Cybersecurity is a top priority for most businesses today. We’ve seen enough organizations brought to their knees by data breaches, ransomware, and security vulnerabilities to realize that failing to prioritize cybersecurity is often at the root. Even though businesses that prioritize security appear to be deploying many solutions, organizations often lean too heavily on built-in security features.
With ransomware attacks on the rise, it is surprising to see that only 40% of respondents have antivirus and ransomware protection. IBM i carries a reputation of being one of the most secure platforms on the market, but threats are increasingly advanced and more prone to target higher value victims like IBM i customers. Additionally, IBM i has never been more interconnected – and therefore exposed – if proper security measures are not in place. Employing solutions that continuously scan your IBM i for malware is a necessity today.
Although only one security solution category is above 50% adoption, it is encouraging to see that every category is seeing growth. This indicates that organizations are taking action in response to near record-high security concerns and tightening compliance regulations.
To cover the financial risks of a cyberattack, many are seeking cybersecurity insurance. Gaining coverage can be difficult, and often requires organizations to have a variety of security measures such as MFA already in place. Even more are integrating IBM i with enterprise solutions via SIEM integration to help combat ransomware with improved visibility over critical IBM i messages and events. At Fortra, we are unique in our ability to combine SIEM with XDR/MDR and treat IBM i as another end point in your infrastructure.
The adoption of antivirus and exit point technology should be prioritized. The old adage that IBM i is behind a firewall is still true, but we have seen many CVEs around firewall appliances and poorly configured equipment result in devastating attacks. Fortra’s Powertech Exit Point Manager and Powertech Antivirus for IBM i provide you with an important layer of defense against intrusion attempts.
RECOMMENDATION:
If your organization is one that currently has no plans to implement certain cybersecurity solutions, it’s worth rethinking that approach. If you are unsure of how to start, our free IBM i Security Scan and a team of experts will point you in the right direction, and The State of IBM i Security Study provides even more insight into the tool and strategies organizations are using to secure IBM i.
Cybersecurity Challenges
Of all the IBM i security challenges organizations face, difficulty with balancing security controls and business efficiency topped the list this year. Very close behind and tied for second place: a lack of security knowledge and skills, and threats that are constantly changing. These have been the top three security concerns for the last four years and reflect the current state of cybersecurity across all industries and boardrooms.
It is also interesting to note that concern over ransomware dropped from 34% to 28%. This is likely, in part, due to the increased adoption of antivirus and ransomware solutions, which jumped from 37% to 40%. Significant increases in concern among other categories such as balancing security controls and efficiency (42% to 48%) and complexity of government and industry regulations (17% to 21%) also likely contribute to this trend.
Adaptation is the overarching goal in the face of cybersecurity threats. The ever-evolving nature of threats requires ongoing vigilance on the part of businesses.
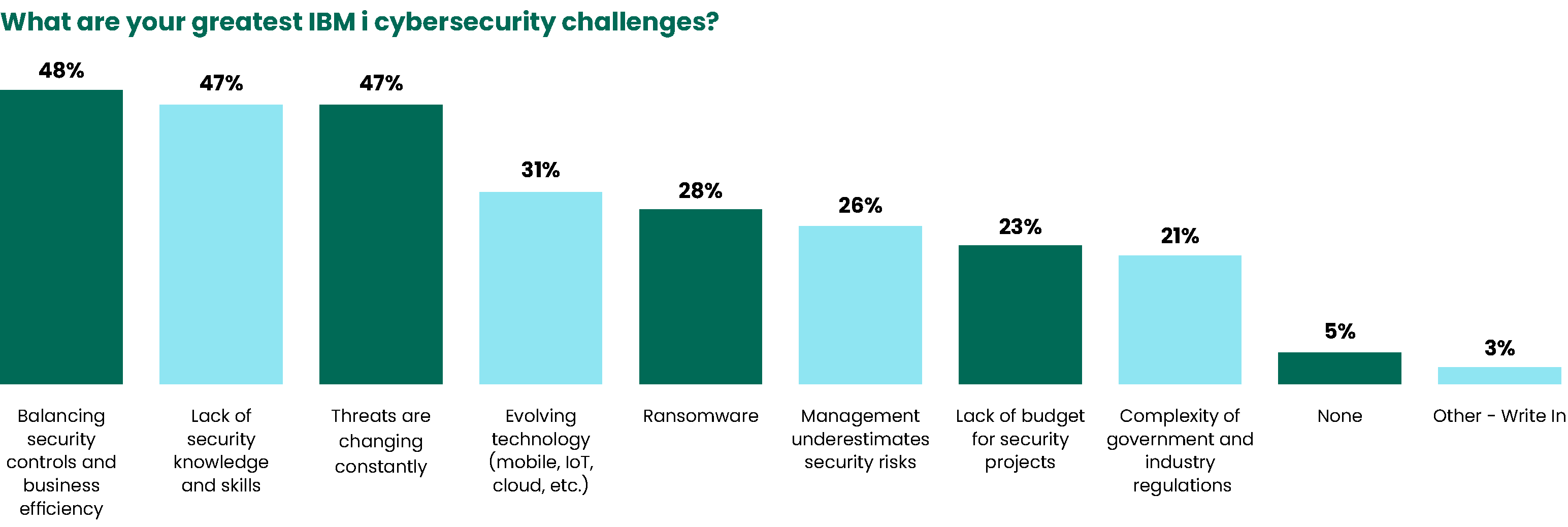
RECOMMENDATION:
In a year that continues to serve up fresh cybersecurity challenges, choosing a cybersecurity partner who understands how to manage constantly evolving threats becomes even more important. Managed Security Services (MSS) from Fortra is a great option to fill in skills gaps on IBM i or your entire enterprise. Our services team has also had great success assisting customers looking to implement SSO on IBM i, which is an excellent way to mitigate the costs and risks associated with manual password management. Ransomware is still a threat, so make sure you’re building a strategy to prevent and detect attacks.
Regulations
IT and industry have shifted over the past several years toward implementing long-overdue improvements in data privacy, and this movement has also gained substantial traction at the national and state levels. Growth in both the number of regulations and the severity of punishments for breaking them indicate that compliance mandates are here to stay. 81% of respondents reported that they are adhering to at least one regulation, namely GDPR, PCI DSS, Sarbanes-Oxley, and HIPAA.
19% of our respondents still do not adhere to any compliance mandates. This is likely due to the fact that many of these organizations are privately owned. Although they do not abide by any regulations, private organizations are still highly concerned about security, as they are generally less likely to recover from the consequences of a ransomware attack.
If you are a privately owned business that does not need to comply with certain regulations, it is worth looking to widely adopted frameworks such as the CIS benchmarks for guidance in crafting your security strategy. Many of the guidelines set forth by these frameworks offer security best practices that, if adopted and maintained, can help you create sustained security success for your organization.
Also, many businesses are now bound by state regulations, such as those in California and New York. As more countries pass national or regional regulations – such as Europe’s DORA for large financial institutions – the number of organizations required to adhere to these laws will grow in the years to come. The International Association of Privacy Professionals estimates that 70% of nations worldwide are covered by some form of national data privacy law, and new laws and regulations are enacted every year, especially in the EU (such as DORA and Data Governance Act). It is essential to be vigilant of the changes and adapt data governance policies accordingly.
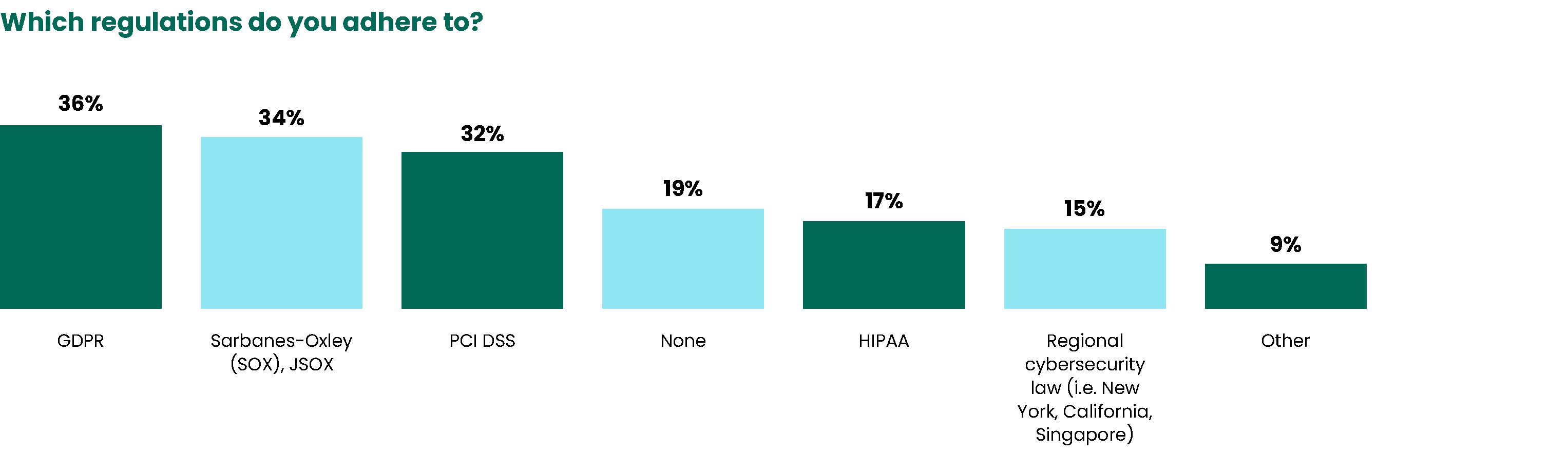
RECOMMENDATION:
Compliance is incredibly important, but some organizations struggle to find the resources to manage requirements efficiently. This compliance monitoring and reporting software for IBM i simplifies compliance report generation and allows you to quickly and easily provide auditors with the information they need. Automating audit processes is becoming a necessity for many organizations, as they cannot afford to continue using manual and time-consuming methods. You can save your staff time by offloading compliance processes with Fortra’s Managed Security Services.
Development Languages
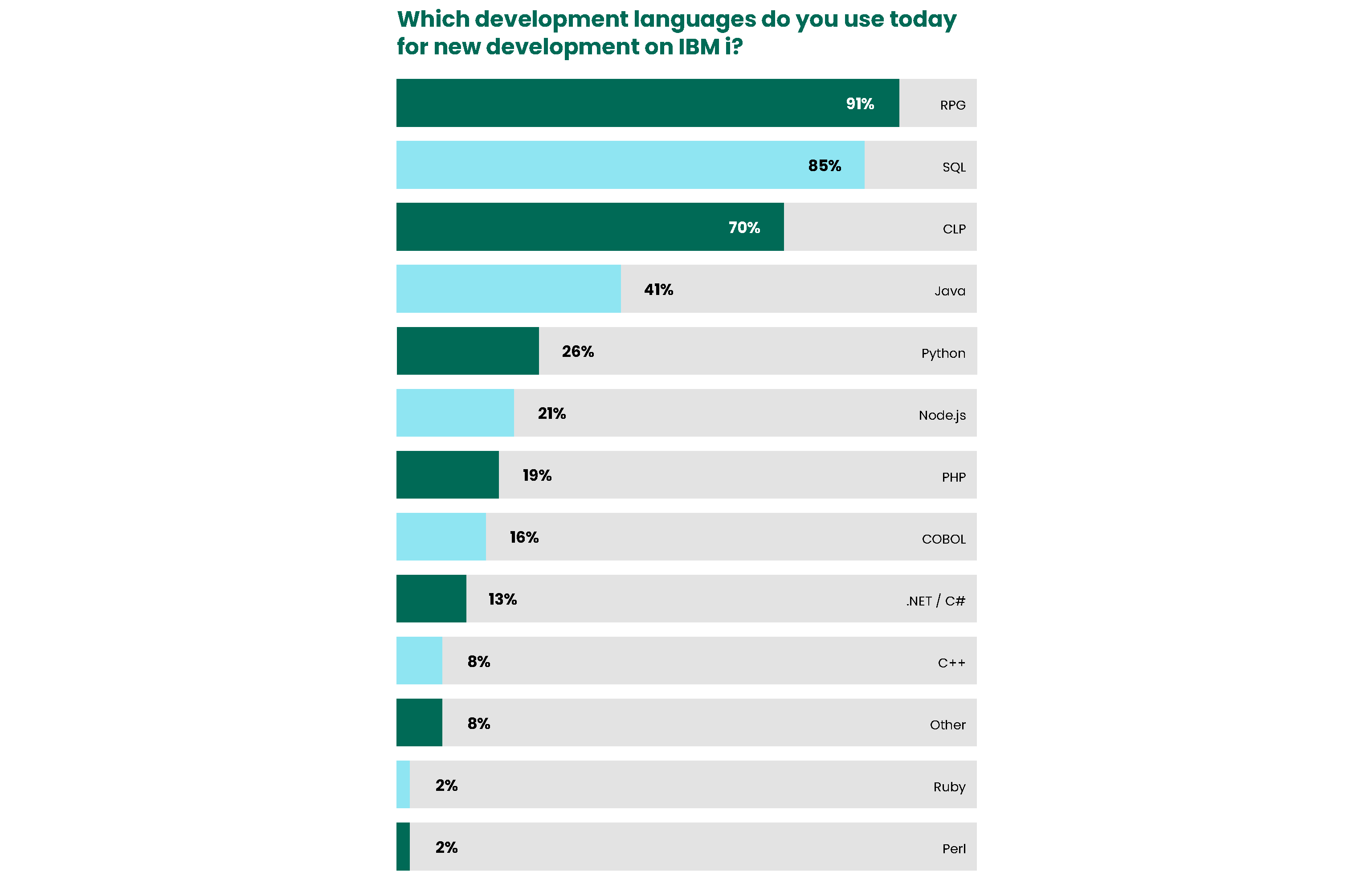
This year, the development languages used for new development on IBM i show interesting trends. The usual leaders—RPG and SQL— remain at the top and show year-over-year increases in usage. People have worried that RPG would fade away, but IBM’s modernization of the language and its integration with DB2 have helped it become a viable language for the future. It has the ability to call services and integrate open source, SQL, and other modern techniques. Organizations are using modern, modular, free-format RPG for new development, and they are pairing this with other languages, which is evident in the number of languages that have significant usage.
Java and CLP remain stable. CLP helps with the automation efforts as there is basically a command line interface to automate just about anything on IBM i. The number of users for other, more traditional development languages is also very steady.
Another interesting trend is that both Python and Node.js usage jumped. Python is the preferred language for performing AI development while Node.js is generally preferred for developing services. Considering the increased demand for AI and services, this indicates that the right languages are being used for the appropriate use cases, and therefore IBM’s strategy is being supported.
We are seeing more people writing in a combination of languages, especially because modern RPG looks and acts like other languages, which also makes it easier to teach. This is promising for the future of IBM i and can help to close the IBM i skills gap.
RECOMMENDATION:
As technology and development landscapes continue to evolve over time, it’s increasingly important for organizations to stay on top of current trends. If you’re looking for educational resources, organizations like COMMON, Fresche Solutions, Perforce, Profound Logic, and Lansa often offer webinars or other types of training that may be beneficial.
Open Source Development Tools
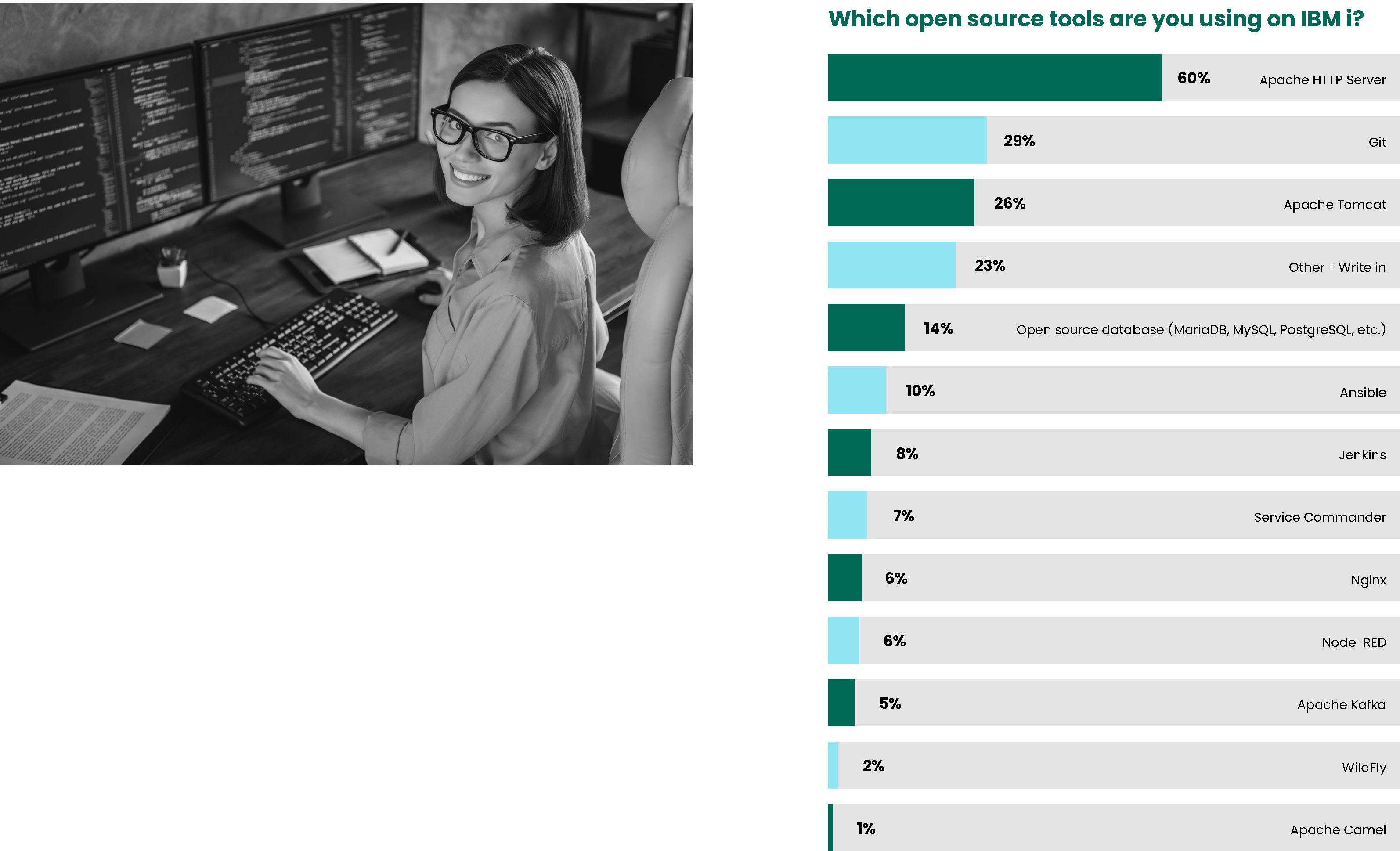
Open source, much like the rest of the IT world, is always developing. IBM puts substantial effort into increasing the availability of open source alternatives, and it shows in the growing number of open source tools being implemented on IBM i.
The most significant change is that Git usage jumped from 21% to 29%. This corresponds with last year’s emphasis on modernization, as Git is generally the open source tool of choice for IBM i shops looking to manage modernized applications and the languages used.
Jenkins and Ansible continue to appear in the table, and together, with the use of Git and Bash, is a strong indication that businesses are putting DevOps approaches to use in IBM i workloads. This is part of the modernization conversation and helps explain why application modernization is near the top of the list of IT concerns.
RECOMMENDATION:
With open source development almost certain to increase over the coming years, it is wise to ensure your development teams are ready for this. Visit IBM’s website for information about support for open source on IBM i.
Application Development Tools
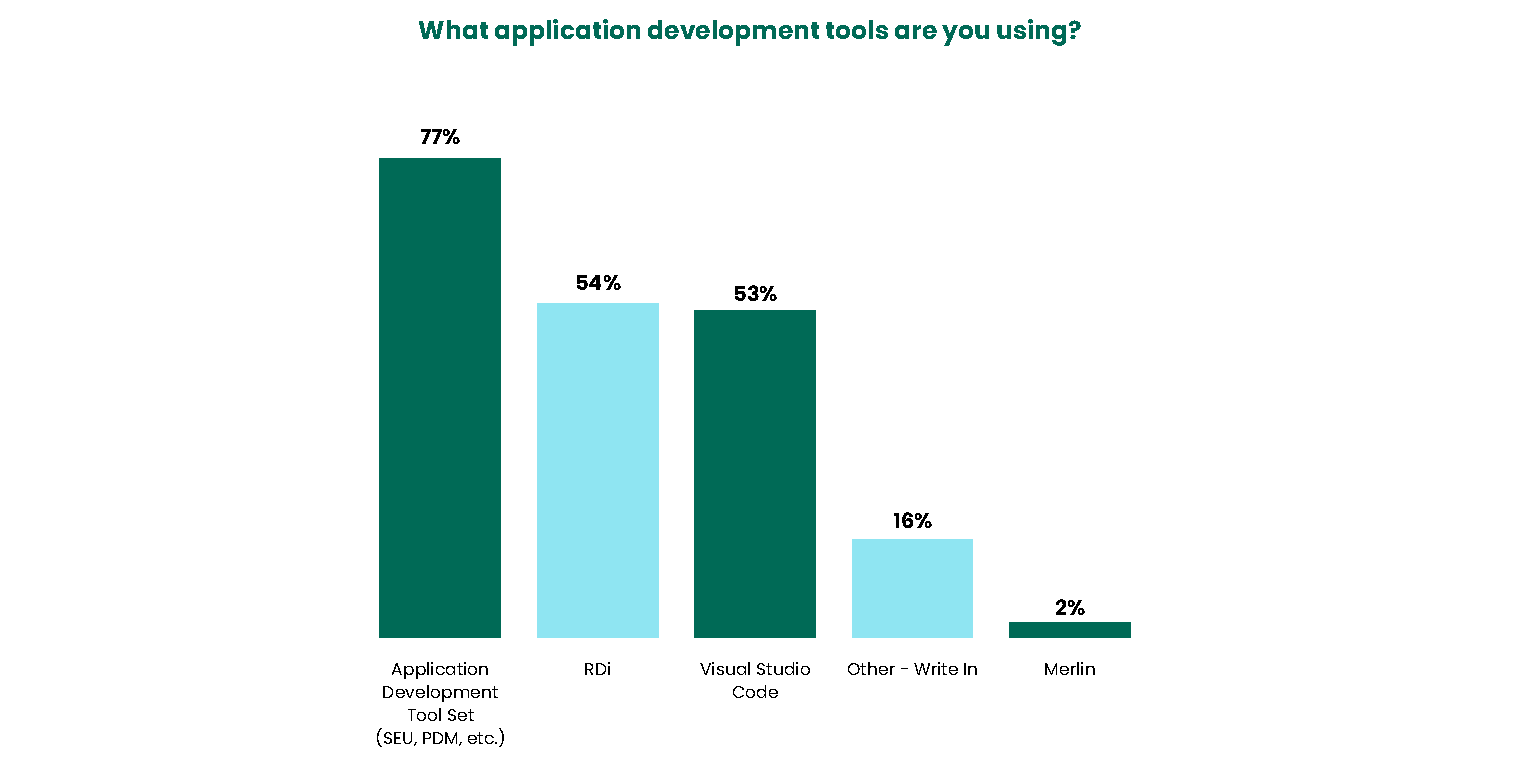
This year’s responses show a balanced use of older tools from the Application Development Tool Set and more modern tools like Rational Developer for i (RDi) and Visual Studio Code. The Application Development Tool Set (composed of SEU, PDM, and more) came in first at 77%, followed by RDi at 54%, and Visual Studio Code at 53%. Visual Studio Code usage continues to grow at a rapid pace and is expected to surpass RDi within the next year.
It is not surprising that such a large percentage of respondents use the Application Development Tool Set, since the more experienced developers are familiar with these tools. However, the adoption of cutting-edge practices is essential for attracting and retaining talented software developers, and the wide use of more modern tools like RDi, Visual Studio Code, and Merlin points toward a bright future for young developers working on this platform. Overall, the results indicate that IBM i developers are using a range of tools for different development activities – and their choice of tool often depends on what they are most familiar with.
RECOMMENDATION:
RDi is technology rich with potential for any IBM i shop. If it’s a question of not being quite sure how best to deploy it, these six RDi tutorials contain a wealth of suggestions and tips to maximize the value from RDi. There are also plenty of instructional Visual Studio Code videos on YouTube to help you get started.
Automation
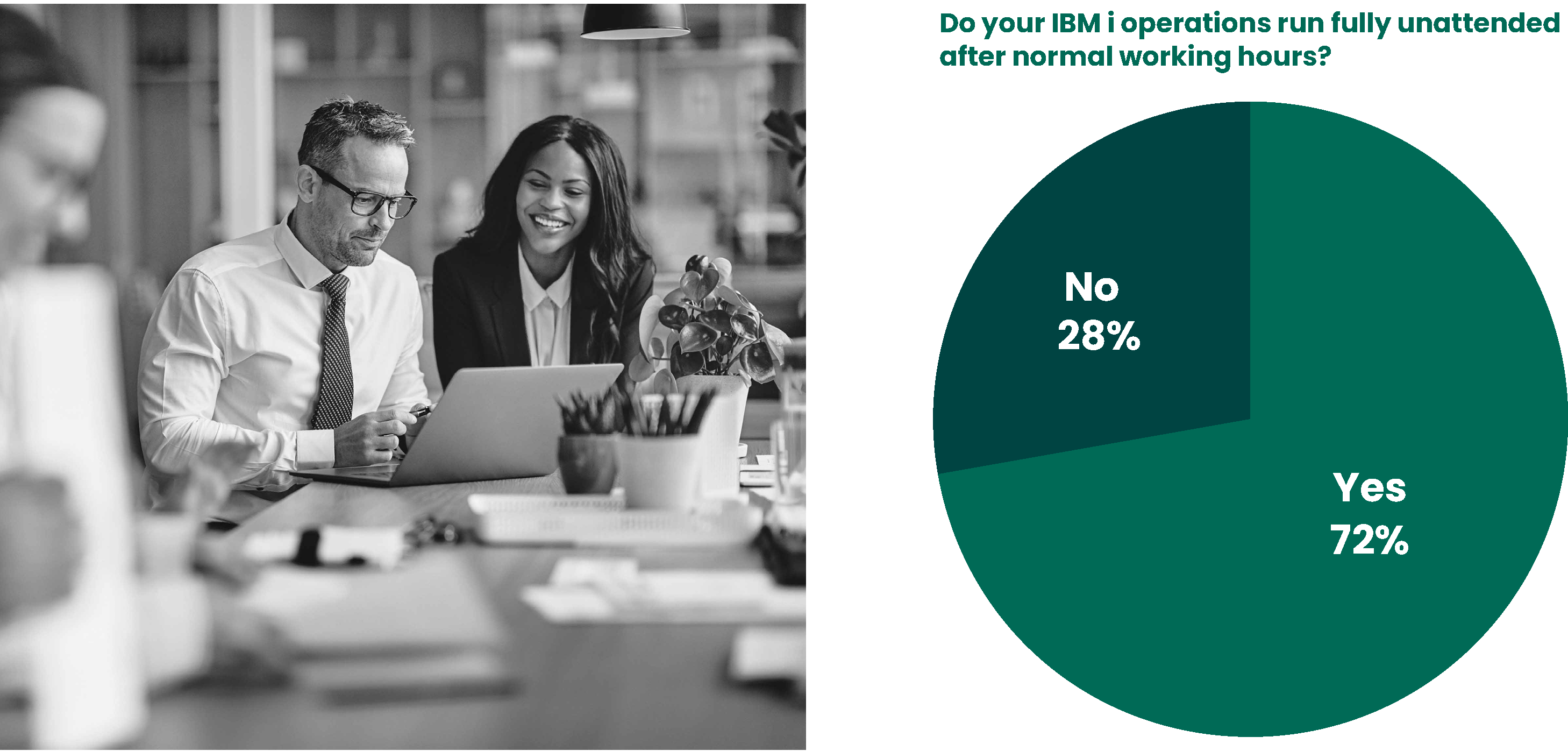
When asked, “Does your IBM i run fully unattended after working hours?”, 72% of respondents said yes. This is a trend that has fluctuated from year to year but has shown an overall consistent growth pattern since 2015. For the fourth consecutive year, less than a third of respondents said they attend to IBM i operations outside of normal business hours.
31% of respondents listed IT and business automation as a top concern for 2025, signaling a significant interest in RPA. With RPA and IBM i automation, you can "set it and forget it," while still readily adjusting as your organization evolves thanks to the rule-based technology that underpins both.
To help clients that run many instances of IBM i, IBM has been developing deployment and configuration automation tools. Ansible and Bash are two items used in helping with deployment and system configurations.
RECOMMENDATION:
Automation can be incredibly useful for any IT department, saving time, money, and resources. If you are unsure whether more automation is suitable for your organization, a Fortra guided automation assessment can help with the decision-making. If you’re working towards going paperless, check out our document management solutions that automate key business processes by electronically capturing, managing, and distributing documents and forms on-premises or in the cloud.
High Availability
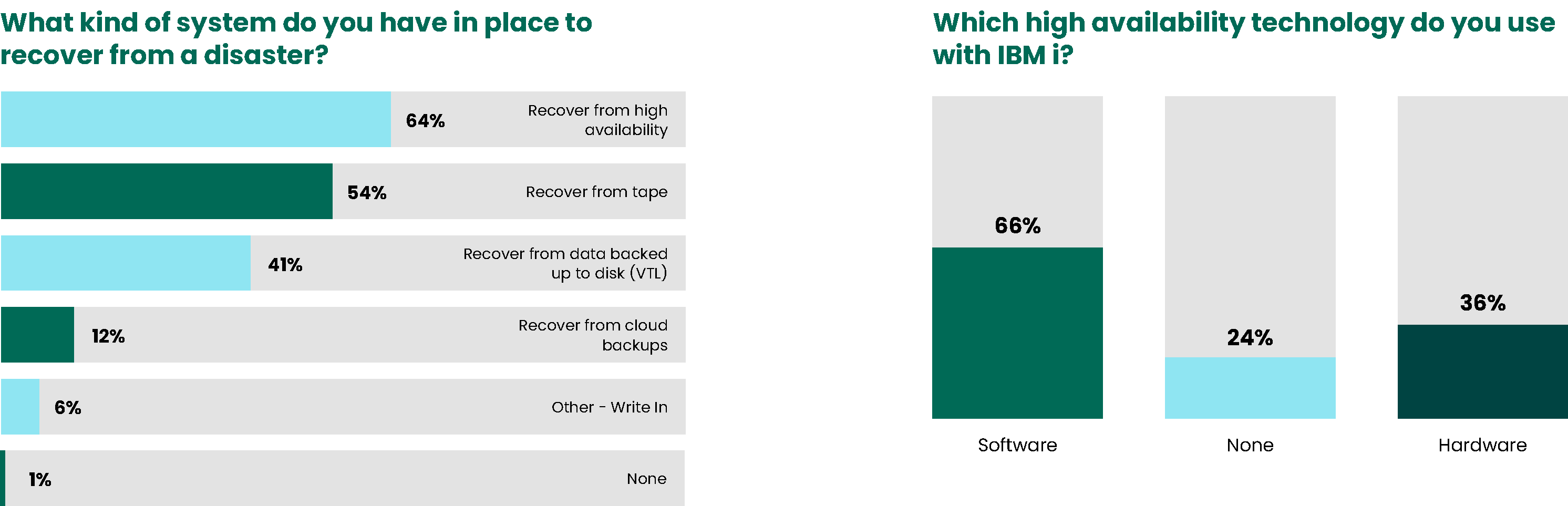
49% of our respondents this year cite high availability/disaster recovery as a top concern when planning their IT environment, down considerably from 63% in 2024. This decrease in concern is likely due to the fact that nearly all of the survey respondents have one or more systems in place to recover from a disaster. IBM i customers have a multitude of backup and recovery options to match their desired recover time objective (RTO) and recovery point objective (RPO).
54% of organizations rely on recovering from tape and 64% have high availability. Customers today are also using storage point-in-time backups like FlashCopy. We expect to see a rise in the reliance on all different types of recovery in the future.
Software-based replication continues to be the clear favorite when it comes to the type of high-availability technology that organizations use. However, we have also seen a consistent increase in the use of hardware-based replication.
When we talk about modernization, we tend to talk just about application modernization, but how you implement infrastructure to be more resilient is a type of modernization that is just as crucial.
RECOMMENDATION:
Disaster recovery cannot be left to chance or ignored completely. Fortra has a range of business continuity solutions and services that can help you plan for (and recover from) the worst. Our team can guide you through the various IBM i HA/DR tools such as PowerHA, Robot HA, and Db2 Mirror for i.