Cyber criminals target business from all angles, so defenders need solutions that span the entire attack chain. But breadth of coverage is useless without deep intelligence to stop ever-evolving attacks and break the chain.
Fortra Offers Adversarial Intelligence
In Various Forms
Strategic
Tactical
Operational
Technical
Applied Threat Intelligence Breaks
The Cyber Attack Chain
At Fortra, we believe that decisions are only as good as the information behind them.
That’s why we make it our mission to produce world-class threat intelligence. Our approach is built on three fundamental pillars:
- Fortra Threat Brain
- Fortra Intelligence and Research Experts (FIRE)
- Threat Community Involvement
Using cutting-edge technology and the best strategies and expertise available, Fortra produces top-tier threat intelligence to thoroughly inform security content and the decision-making process.

Fortra threat intelligence gives you the power to break the attack chain at any stage.
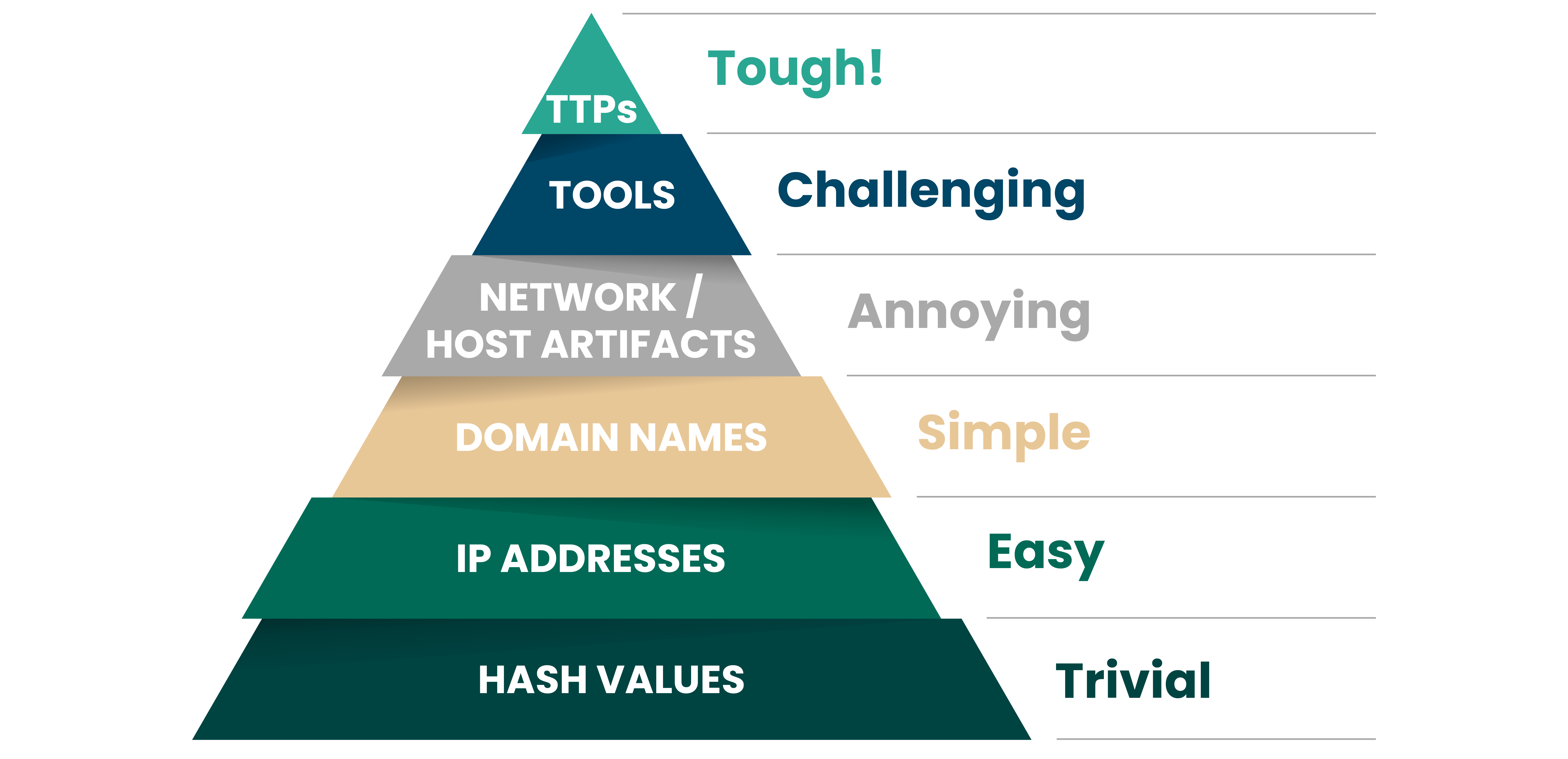
It’s time to hit adversaries where it hurts. Security professional David J Bianco invented the notion of the Pyramid of Pain, a ranking of which indicators of compromise cause the most “pain” to attackers to reinvent when denied through applied threat intelligence.
All indicators have a role to play in breaking the chain, but to maximize threat actor pain, Fortra threat intelligence focuses on the highest indicators on the pyramid.
Indicators at the top of the pyramid stay relevant for longer, delivering sustained security value and forcing adversaries back to the drawing board. Indicators at the base of the pyramid are simpler to refresh, but are still valuable in detecting and disrupting attack sequences.
Together the Fortra Threat Brain and FIRE cover the entire pyramid to cause comprehensive pain to threat actors.
Fortra Threat Brain automatically collects and unifies Trivial, Easy, Simple, and Annoying indicators across open source, public, and proprietary feeds, prioritizes them based on active (anonymized) campaigns seen in our customer base, and archives them when attackers evolve their tactics.
TTPs and tooling are the most challenging for attackers to reinvent, so it follows that they also require expert research and curation to be effectively applied to attack disruption. Our Fortra Intelligence and Research Experts (FIRE) team stay on top of attacker TTPs, build, on indicators collected in Fortra Threat Brain, and apply intelligence across the Fortra platform, point products, managed services, and empower end users.
The powerful combination of Fortra Threat Brain and our FIRE team ensures that Fortra has both the breadth and depth of coverage necessary to break the attack chain at any stage, minimize impact, and keep organizations operational.
