"Operation Elicius", a joint international law enforcement operation involving Europol and police forces in Italy, France, and Romania, has successfully dismantled a Romanian ransomware gang that targeted network-attached storage (NAS) devices and arrested its suspected leader.
The so-called "DiskStation Security" ransomware group has targeted and compromised NAS devices - particularly those manufactured by Synology - since 2021, leaving the data of businesses and non-profit organisations encrypted, and demanding a ransom for its recovery.
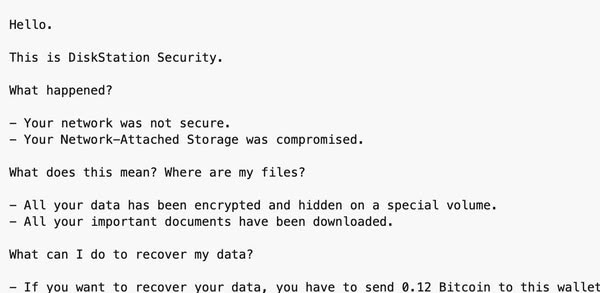
Police say that their investigation began after a series of complaints from numerous companies in the Lombardy region of Italy, complaining that their operations had been paralysed because they were unable to access their data without agreeing to give in to the extortionists' demand for a substantial amount of cryptocurrency.
The DiskStation ransomware gang, which has worked under other names including "7even Security", "LegendaryDisk Security", "Umbrella Security", and "Quick Security" has hit victims from a wide spectrum of industries, including graphic design, event organisation, film-making, as well as non-government organisations such as charities.
A two-pronged police investigation - combining an indepth digital forensic analysis of hacked computer systems and close examination of the blockchain - ultimately led authorities to Bucharest, Romania.
In June 2024, police searched the homes of suspects in Bucharest, and arrested a 44-year-old Romanian national, who is suspected of being a key figure behind the ransomware group. The man, who has not been named, face charges of extortion and unauthorised access to computer systems.
With the arrest of the alleged ringleader of the DiskStation ransomware group, police are hoping that they have dealt a significant blow to the criminal operation that has shown no scruples about the types of organisation it has attacked.
Synology has been advising users on how to protect their NAS devices from ransomware attacks for several years. Much of the advice revolves around minimising the exposure of NAS devices to the internet, hardening password security, and ensuring that regular backups are made of critical data.
The accounts used to secure NAS devices are no different from any other when it comes to security - you should ensure that passwords are unique, and not easy-to-crack. Attackers will often use automated tools to brute force their way into poorly-secured devices, or take advantage of users who have used easy-to-guess, predictable passwords.
To further reduce risk, users are urged to enable two-step verification (2FA) and, where possible, disable or rename the default “admin” account altogether, as it is a common target for malicious hackers.
The exposure of NAS devices can be limited by disabling remote servies like QuickConnect, WebDAV, and SSH if they are not required. Synology’s built-in firewall can also be used to restrict access by IP address, region, or protocol, helping to prevent unauthorised connections.
In addition, it is sensible to ensure that NAS devices are kept up-to-date with the latest security patches and updates.
More information about how to better secure NAS devices from ransomware can be found on Synology's website.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Cybercrime Intelligence Shouldn't Be Siloed
Fortra® experts are dedicated to protecting organizations and the public by delivering the latest insights, data, and defenses to strengthen security against emerging cyber threats.

