What is the SafePay ransomware?
SafePay is a relatively new ransomware threat that was first observed around September 2024. Like other ransomware, SafePay encrypts victims' files so they cannot be accessed, and then demands the payment of a cryptocurrency ransom for their recovery. As part of a "double extortion" tactic, the hackers behind SafePay also steal data from affected organisations and threaten to publish it on their dark web leak site if a ransom is not paid.
What makes SafePay unusual?
Most modern ransomware gangs operate a Ransomware-as-a-Service (RaaS) model, where affiliates are allowed to deploy the ransomware in return for a percentage of the proceeds they manage to extort. However, SafePay does not operate like this. Instead, it appears not to offer itself to affiliates, but instead the same group develops and deploys the ransomware themselves rather than relying upon others.

Indeed, a banner on SafePay's dark web leak site says:
SAFEPAY RANSOMWARE HAS NEVER PROVIDED AND DOES NOT PROVIDE THE RAAS
Why would they not operate as a ransomware-as-a-service model? Aren't they turning their back on a lot of cash?
While it is true that SafePay may be closing the door on affiliate income, it does offer the benefit of better operational security and tighter control of how its ransomware is used.
Interesting. So, why is SafePay in the news?
A recently published threat report released by security experts at NCC Group revealed that SafePay was currently the most active ransomware group. In the month of May 2025 alone, 70 ransomware attacks were linked to Safepay, accounting for 18% of the total.
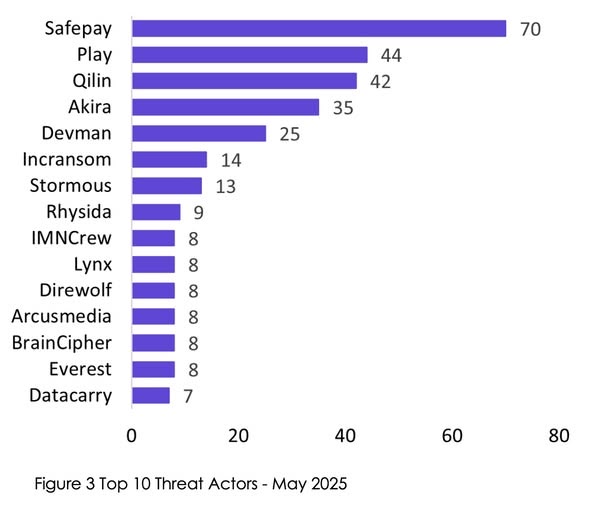
In an indication of the ransomware group's increased activity, this was the first time that SafePay had appeared in NCC Group's top 10 list of threat actors.
What has made SafePay so successful so quickly?
The answer to that question is not clear, but it is suspected that SafePay may be closely related to other notorious ransomware groups, including LockBit, BlackCat, and INC Ransomware.
In other words, the folks behind SafePay may not be new to the scene?
Correct. If the links to other notorious ransomware gangs are found to be true, it would mean that these are cybercriminals who are experienced in extorting money out of their victims, and have the resources to make a significant impact.
Which companies have been hit by SafePay?
UK telematics business Microlise, which offers vehicle tracking services to the likes of DHL and Serco, revealed that it had been hit by ransomware in October 2024, and was one of SafePay's first publicised victims after the theft of 1.2TB of data. Other victims have included a North Carolina anatomic pathology lab, which was breached in January 2025 in an attack that saw the theft of information related to over 200,000 patients, including names, birthdates, addresses, health insurance details, and medical treatment data.
Is no-one safe from being hit by SafePay ransomware?
Well, actually, yes, some people are. The SafePay ransomware is programmed to check the language settings of the computer it is running on, and if it spots the system is running any of the following languages, it will immediately stop running without causing any damage: If the system language matches any specified languages, the malware will immediately terminate. A complete list of languages checked can be seen below:
- Armenian
- Azerbaijani (Cyrillic)
- Belarusian
- Georgian
- Kazakh
- Russian
- Ukrainian
Why would the ransomware want to do that?
Two immediately reasons jump to mind. One is, for instance, that the ransomware does not want to count - say - Russian corporations amongst its unintended victims, in fear that local law enforcement agencies might come after it.
Makes sense. What other reason could there be?
Well, maybe the ransomware authors' themselves run computers which are configured to use those languages. They would hardly want to become accidental victims of SafePay themselves, would they?
I guess not. So, how can my business protect itself from the SafePay ransomware? I don't think it would be practical to change the language settings of all our PCs to Russian.
SafePay is known for breaking into organisations by using stolen VPN or RDP credentials. It has not been reported to have used phishing techniques frequently seen in many other ransomware attacks. Therefore, organisations that worry they might be targeted would be wise to enforce multi-factor authentication on all remote access points, disable unused RDP or VPN access entirely, and use IP allowlists or geofencing where possible. In addition, we recommend all companies follow our general advice for defending against ransomware attacks, which includes tips such as:
- Making secure off-site backups.
- Running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- Using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- Encrypting sensitive data wherever possible.
- Reducing the attack surface by disabling functionality that your company does not need.
- Educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Beating the Business of Ransomware
Learn how to beat cybercriminals’ ransomware business.

