What Is NIST Cybersecurity Framework?
The NIST Cybersecurity Framework (NIST CSF) is a set of comprehensive guidelines and best practices for organizations to improve their security posture. This framework combines industry standards and best practices to provide recommendations and standards that enable organizations to better prepare in identifying and protecting against cyberattacks, and guidance on recovering from an incident.
Overall, NIST CSF is designed to help organizations identify and close security gaps in operational technology.
How it Works
NIST CSF educates organizations on how to prioritize and triage critical systems based on where the biggest negative impact tp business and operations is likely to occur. The framework helps to identify areas of low, moderate, and high impact, and apply security tools and controls appropriately.
The History of NIST CSF
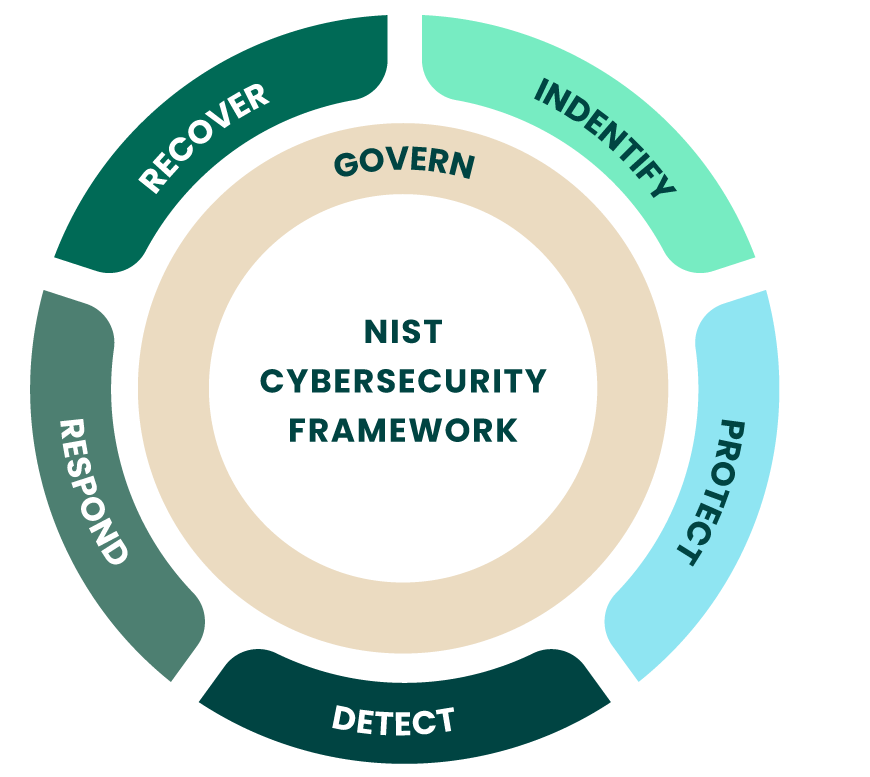
The original version (v1.0) was released in 2014 and intended for critical infrastructure such as energy and banking. Originally developed by the National Institute of Science and Technology (NIST) in conjunction with organizations in the critical infrastructure industry, NIST CSF was purpose-built to make securing complex environments simpler. The framework was made of five core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
While NIST CSF became a requirement for all federal agencies in May 2017, it's been widely adopted and used by organizations of all sizes across every industry due to its comprehensive nature. It’s now considered to be the gold standard to build and mature security programs as it provides metrics to measure progress, which assists in communicating to senior leadership the program’s efficacy.
Version 2.0 and the Sixth Core Function
The current version (v2.0) was released by NIST in February of 2024 and includes multiple updates. These include a sixth core function (Govern), recognized broader application with language changes, and clarification along with implementation examples. It also includes supply chain risk and aligns to other NIST resources.
Version 2.0 of the framework is clearer and more in-depth than the previous edition, but organizations may still require some guidance in order to use the framework to its fullest potential.
Tips for Using CSF 2.0
CSF Profiles
Checking existing CSF profiles can help to determine where the gaps are in your organization. NIST also has the CSF reference tool to find particular examples of implementation.
Buy-In
Ensure that business leaders are involved in the conversation about the adoption of the CSF. It is vital for security and IT teams to work hand in hand with C-suite executives and boards to create a cybersecurity strategy that maximizes the success of the business. Everyone should be on the same page regarding drivers, objectives, and long-term business goals so security teams can make informed decisions.
Future State
Bear in mind the target profile and the threat landscape. Keeping one eye on the current state of the business and the other on the future, companies can anticipate trends and use the framework to smooth the process of their adaptation to new and evolving threats. The ability to change your approach to cybersecurity in response to threat trends is an important skill.
NIST CSF Compliance Checklist: The 6 Pillars
Achieving NIST compliance can be a long process that considers software solutions, physical security, and internal processes. The primary objective of the NIST CSF 2.0 is to help identify areas of weakness, prioritize hardening efforts, and communicate to technical and business leaders through six core functions.
Govern
- Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy
- New step added in Revision 2.0 of the CSF to reduce complexity and support the other steps
- Provides guidance for how organizations can make internal decisions that support the security strategy
- Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy
- New step added in Revision 2.0 of the CSF to reduce complexity and support the other steps
- Provides guidance for how organizations can make internal decisions that support the security strategy
Identify
- Help determine the current cybersecurity risk to the organization
- Addresses asset management, risk assessment, and improvements to risk management processes and procedures
- Help determine the current cybersecurity risk to the organization
- Addresses asset management, risk assessment, and improvements to risk management processes and procedures
Protect
- Use safeguards to prevent or reduce cybersecurity risk
- Identity and access management, security awareness training, data security, and management of the IT estate
- Use safeguards to prevent or reduce cybersecurity risk
- Identity and access management, security awareness training, data security, and management of the IT estate
Detect
- Find and analyze possible cybersecurity attacks and compromises
- Includes continuous monitoring and analysis to surface anomalies and indicators of compromise
- Find and analyze possible cybersecurity attacks and compromises
- Includes continuous monitoring and analysis to surface anomalies and indicators of compromise
Repond
- Take action regarding a detected cybersecurity incident
- Guidance on incident management through documented incident response plan with forensics to determine full scope and inform hardening requirements upstream
- Take action regarding a detected cybersecurity incident
- Guidance on incident management through documented incident response plan with forensics to determine full scope and inform hardening requirements upstream
Recover
- Restore assets and operations that were impacted by a cybersecurity incident
- Implementation of hardening to prevent or reduce the risk of a similar incident and communication strategy.
- Restore assets and operations that were impacted by a cybersecurity incident
- Implementation of hardening to prevent or reduce the risk of a similar incident and communication strategy.
Best Practices for NIST CSF Compliance
Build your processes with data security in mind
Do not collect customer personal information that you don’t need. Only hold on to the information that’s required for you to carry out your business. Your service providers should also implement all necessary security measures. All third-party software tools used by the company should be updated and patched. Make sure all sensitive files are stored securely. Protect the devices that process important information.
Understand your systems and the data they collect
Identify the possible vulnerabilities in the company systems and the risks associated with loopholes. When these points are clearly understood by an organization, it’s easier to prioritize the cybersecurity tasks according to business requirements.
Implement the right safeguards for your infrastructure
Safeguards include training the employees regarding cybersecurity risks, limiting access to critical systems and data, and having the right cybersecurity procedures and policies in place. Non-public information should be guarded with administrative access. Use secure passwords and leverage multi-factor authentication. Protect your data when it’s stored and also during transit.
Develop and implement the right monitoring solutions and processes
Monitoring solutions and processes help identify the occurrence of a cybersecurity event. To do so, all information systems need to be monitored and processes have to be tested regularly to detect unusual activity. An intrusion detection system might be helpful here. Also, assess whether your applications are vulnerable to an SQL injection attack..
Have a strategy to follow if there's a cybersecurity event
This includes coordinating and communicating with stakeholders and law enforcement agencies, controlling the cybersecurity event in time, and rechecking the processes of the organization to incorporate what you’ve learned from the event.
Develop a recovery strategy
A recovery strategy will help you resume your business activities after the cybersecurity incident. The goal is to recover in the minimum possible time. There should also be ways to minimize the impact of the incident on all stakeholders.
Fortra and the NIST Cybersecurity Framework
Fortra’s portfolio of solutions for infrastructure protection and data security helps organizations meet the NIST CSF.
Identify
Protect
Detect
Respond
Penalties for Non-Compliance
NIST is a non-regulatory agency and non-compliance has no associated financial penalties. However, as the most widely-used cybersecurity framework in the United States, compliance with NIST CSF protects your business.
If an auditing agency becomes aware that you’re not adequately meeting compliance standards, your company could lose valuable certifications, which can limit your ability to partner with other organizations, bid on government projects, and qualify for contracts. If you’re already in business with a government organization and fail to maintain compliance, it can result in a termination of the contract and even result in legal issues.
Put Fortra's industry-leading team in your corner
Find out all the ways the Fortra team can make your life easier. From our constantly evolving solutions to our cutting-edge compliance tactics, we’re here to help.