Over the years, organizations have taken different approaches to defining and managing operating system security configuration for their UNIX and Linux implementations. For example, a simple item like enforcing password length and complexity is implemented using five separate methods on today’s enterprise Open System platforms.
Core Privileged Access Manager (BoKS) takes care of the underlying technical specifics of how security policy changes are achieved. This can be done via each supported platform or by live updates from its distributed security database.
Core Privileged Access Manager (BoKS) makes it easy with two main methods of centralized security administration for all technical platforms.
You can select the right option for your business depending on the personal preferences of your staff and their experience with the command line.
How We Help You Gain Control
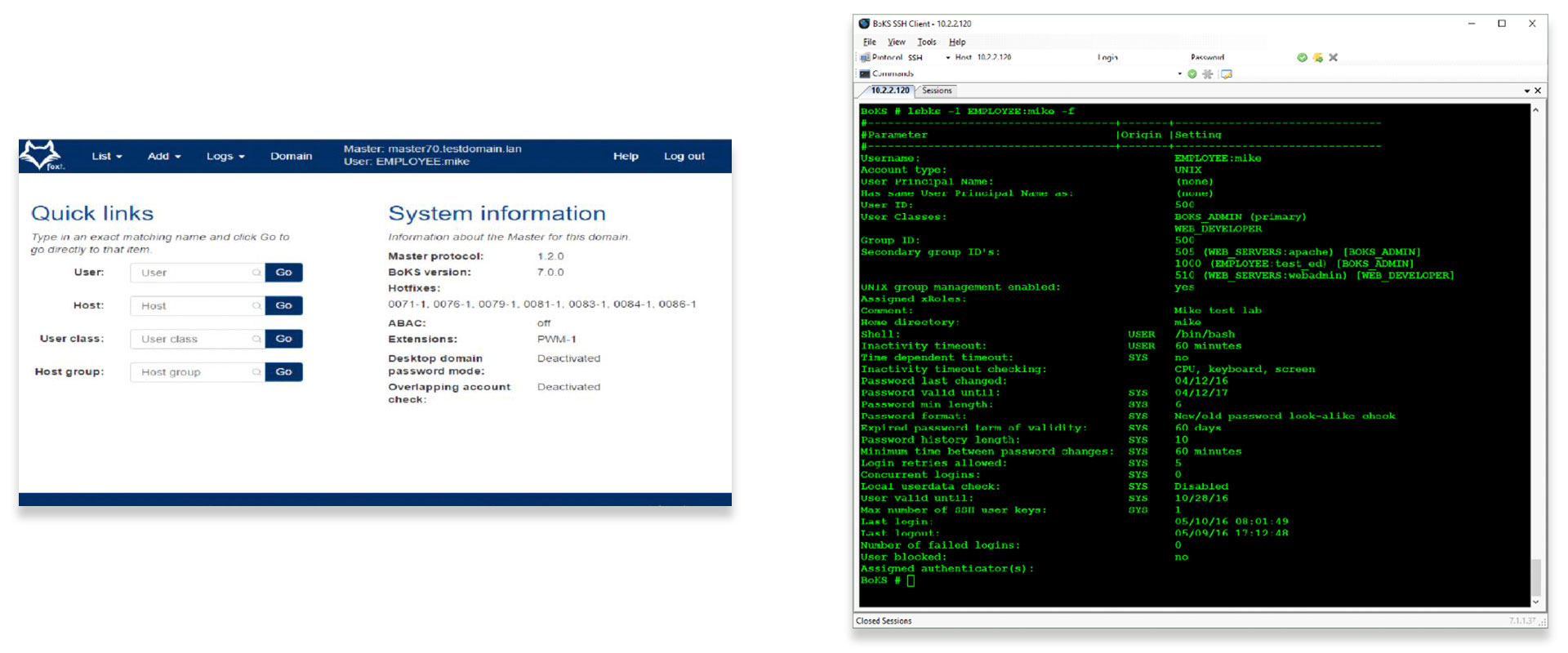
Access the Web Portal
Leverage TLS Encryption
Rely on the Web-Based Interface
Manage Sub-Administration Controls
What This Means to You
Meet Compliance Requirements
Reduce Admin Overhead
Significantly minimize training requirements with BoKS. Users don’t need specific platform-based security training for different technical platforms including Linux, AIX, HP-UX, Solaris, zLinux, PowerLinux, OpenStack, and/or Hadoop.
Prevent Breaches
Achieve administrative consistency, which eliminates the need for your technical staff to manage platform-specific implementation details. With BoKS there is no need to script or “recipe” with configuration management tools.
See Core Privileged Access Manager (BoKS) in action
Learn how Core Privileged Access Manager (BoKS) can centralize security and administration to better manage your security policies by watching our product demo.