
Overview
Scripted Sparrow is a prolific Business Email Compromise (BEC) collective with members spanning three continents. The scale of the group’s operation strongly suggests the use of automation to generate and send their attack messages. The group utilizes a combination of free webmail addresses as well as addresses on domains they’ve registered specifically for their operations. We also observed a handful of cases where the group appears to be operating out of compromised mailboxes at legitimate organizations. Details of the addresses used by Scripted Sparrow can be found in Appendix B.
The group operates by posing as various executive coaching and leadership training consultancies. They send a message to a member of the victim organization’s Accounts Payable team, typically with two PDF attachments: An invoice, containing ACH or wire transfer instructions, as well as a completed W-9 form. The body of their initial message contains a spoofed reply chain between the fictious consultancy and an executive of the victim organization. A typical initial lure message is shown in Figure 1 below.
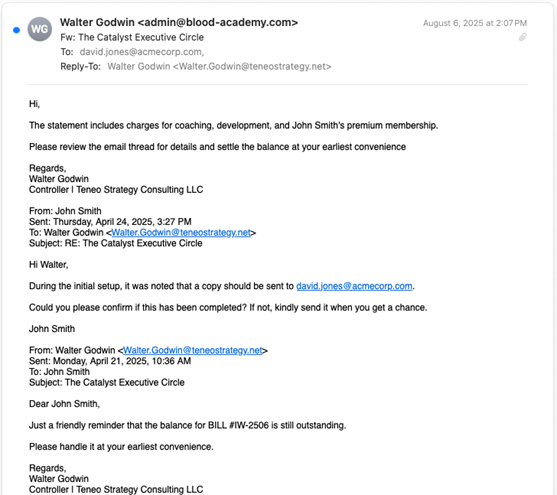
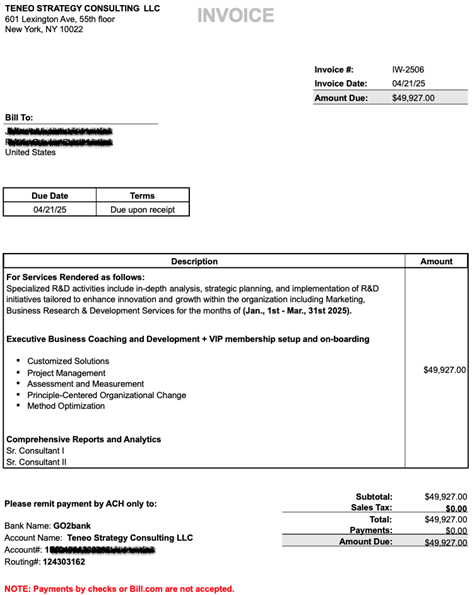
Early versions of messages from Scripted Sparrow included two PDF attachments. The first was an invoice, with an amount typically just under $50,000, complete with ACH transfer instructions for making payment. The second attachment would be a W-9 form for the “vendor.” More recently, the group has claimed to include an invoice and W-9 in their message but would intentionally omit the attachments. If the message is successfully delivered to the intended recipient, and the recipient falls for the ruse, the recipient will reply to the group asking for the “forgotten” attachment. In this way, the group avoids exposing their mule account until they have a potential victim gullible enough to respond to their initial message. Figure 2 and Figure 3 below show two sample invoices generated by Scripted Sparrow.

Activity
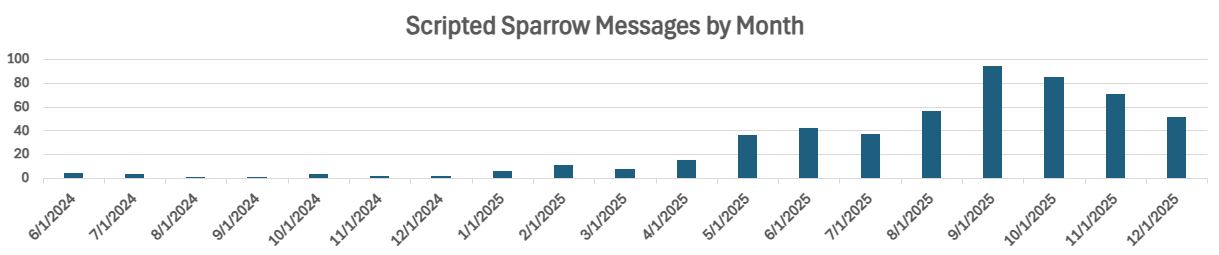
The Scripted Sparrow group was first observed by Fortra Intelligence and Research Experts (FIRE) in June 2024. Their activity has been increasing since then, peaking in September 2025 as seen in Figure 4. As of this writing, our team has identified 496 unique engagements that we can attribute to Scripted Sparrow. You may be thinking that 496 total engagements don’t really count as “prolific”; however, this number must be taken in context. These are messages forwarded to Fortra’s Suspicious Email Analysis (SEA) team by attentive users at companies who use our SEA service.
To better gauge the scope of the group’s operations, we looked at the domain kornferry.ws, which was used in one of our 496 engagements, to see if any of our Cloud Email Protection (CEP) customers saw activity from that domain. Looking at CEP data, we found that 23 organizations had been sent mail from that domain, with 70 users targeted.
While I wish that every company in the world was protected by Fortra CEP, a more realistic estimate would be that one out of every 1,000 companies worldwide uses CEP. In other words, a conservative estimate would be that for each message seen by our team, Scripted Sparrow likely sent 70,000 messages. The 94 engagements we conducted in September likely represent about 6.6 million targeted messages sent by the group.
Operational Security (OpSec) Measures
Our team conducted active defense engagements with the Scripted Sparrow group to learn more about their infrastructure, team member locations, and security measures used by the group. As part of these engagements, we would direct the threat actor to one of several websites operated by our team. This enabled us to see the IP addresses and user agents (browsers + devices) utilized by the group. These websites generate a unique fingerprint for each device + browser combination seen, enabling us to track a given actor across multiple interactions. Our team used social engineering to convince the threat actor to enable location services in their browser, giving us highly accurate geolocation information even when the actor was utilizing a VPN or other proxy. It should be noted that it is trivial to spoof a browser’s geolocation, either using one of several available browser plug-ins, or by using the developer tools available on most modern desktop browsers.
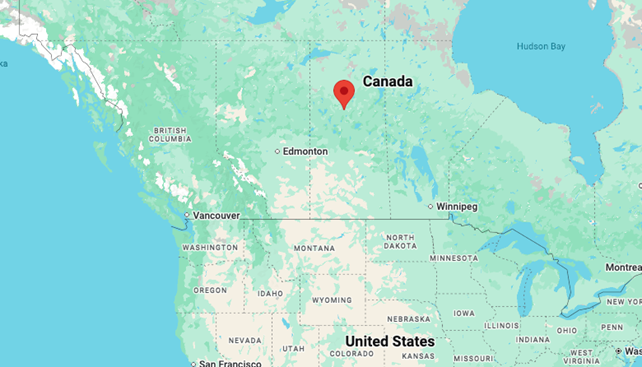
Many of the web interactions we recorded for the group occurred on Windows computers running Remote Desktop Protocol. In these instances, the locations we obtained were the locations of the machine running RDP, rather than the threat actor’s physical location. We also observed the use of location spoofing even when the attacker was utilizing Remote Desktop Protocol to mask their location, indicating a heightened level of paranoia as well as a lack of technical understanding of how RDP functions. We can see this in Figure 5 below; it is highly unlikely the threat actor was in such a remote part of Saskatchewan.
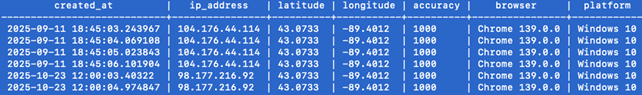
In some cases, we were able to identify location spoofing using the browser fingerprint we derived from each interaction. The idea here is that each device/browser combination is highly likely to generate a unique fingerprint. In Figure 6, we see an example of a threat actor who switched IP addresses on their device on November 4th at 1:50pm UTC and managed to change their GPS location from the San Francisco Bay Area to a Toronto suburb in less than 5 seconds.
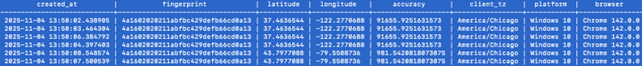
Our team also observed numerous device locations where the accuracy was exactly 1,000 or 100 meters, yet both the latitude and longitude had 4 or fewer decimal places of precision. This suggests the use of a browser plug-in to spoof the attacker’s location, as such a highly accurate geolocation would typically result in more than 4 decimal places of precision in latitude/longitude. Figure 7 shows an example of such an inconsistency.
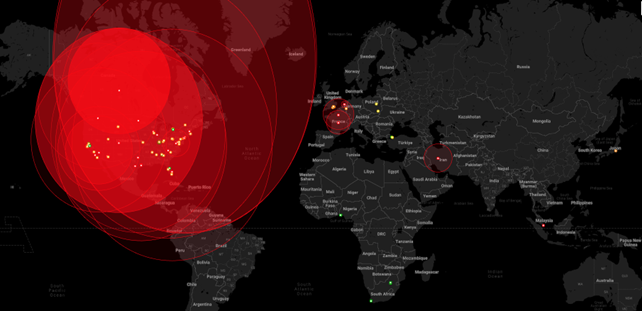
We mapped the raw geolocation data we collected from members of the Scripted Sparrow group; this is shown in Figure 8. The radius is generated based on the accuracy value obtained from the geolocation reading.
Our team developed a machine learning algorithm to assign a trust score to each set of location data we obtained when Scripted Sparrow members visited one of our websites. The algorithm considered a variety of factors, including time zone inconsistencies, disagreements between stated geolocation accuracy and the precision of latitude/longitude measurements, whether Remote Desktop Protocol was running on the client machine, disagreements between the platform and the quality of the geolocation data, and several additional criteria.
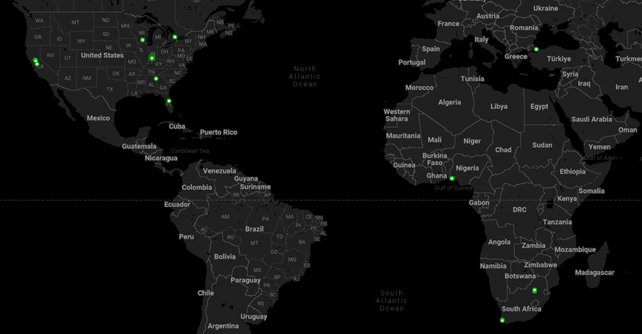
After running our algorithm against the raw data, we mapped only the high-confidence locations. The result is shown in Figure 9. Based on our analysis, we believe the Scripted Sparrow group has members located in Nigeria, South Africa, Türkiye, Canada, and the United States.
Infrastructure
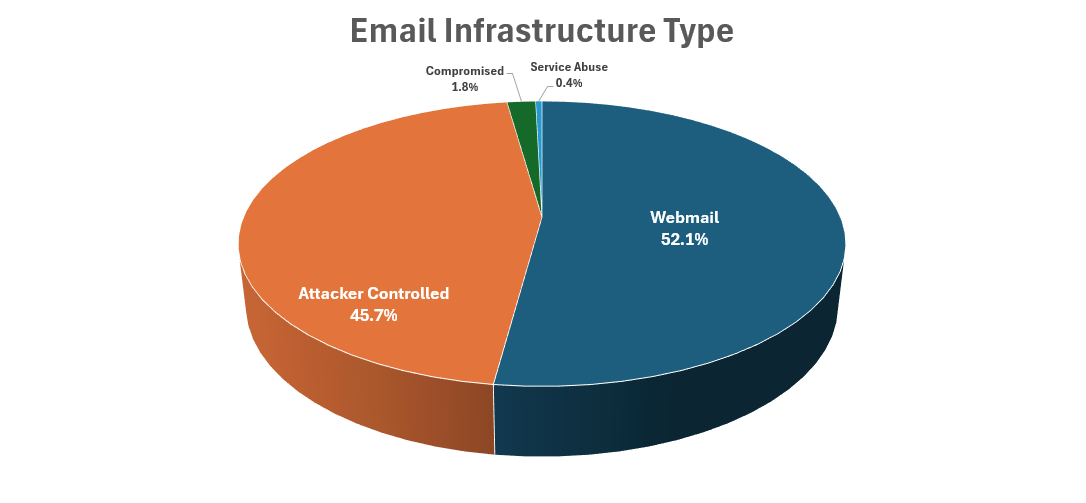
The Scripted Sparrow group utilizes a combination of webmail addresses as well as addresses on domains that they registered. We also observed a small number of addresses that we believe were likely compromised by the group as well as a single email address that abused Microsoft’s Exchange Online service. Figure 10 provides a breakdown of the type of email infrastructure used by Scripted Sparrow.
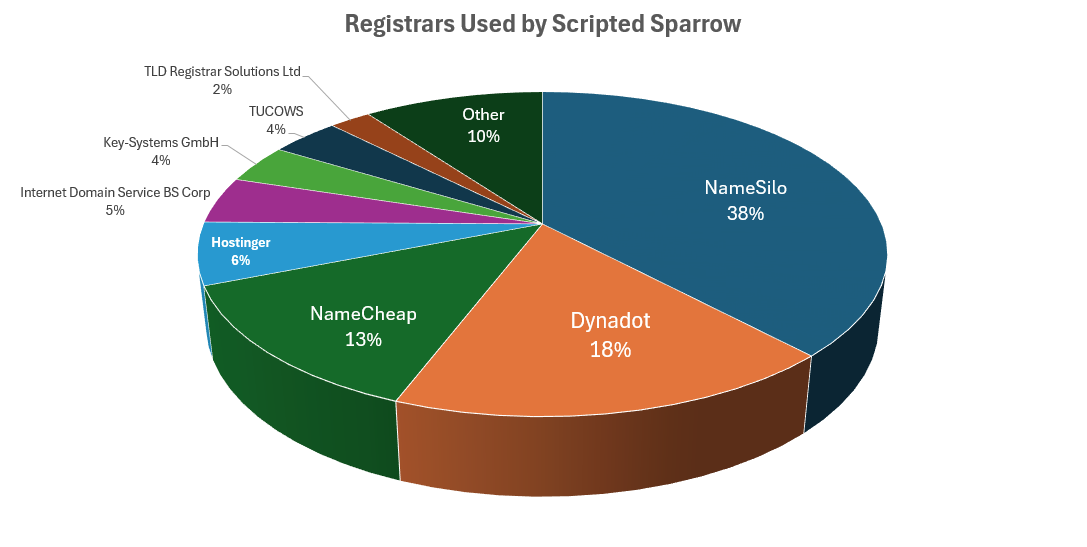
When Scripted Sparrow registered a domain for their activities, they tended to use a relatively small number of registrars. The group overwhelmingly favored NameSilo and Dynadot; Figure 11 provides a detailed breakdown of the registrars used by Scripted Sparrow.
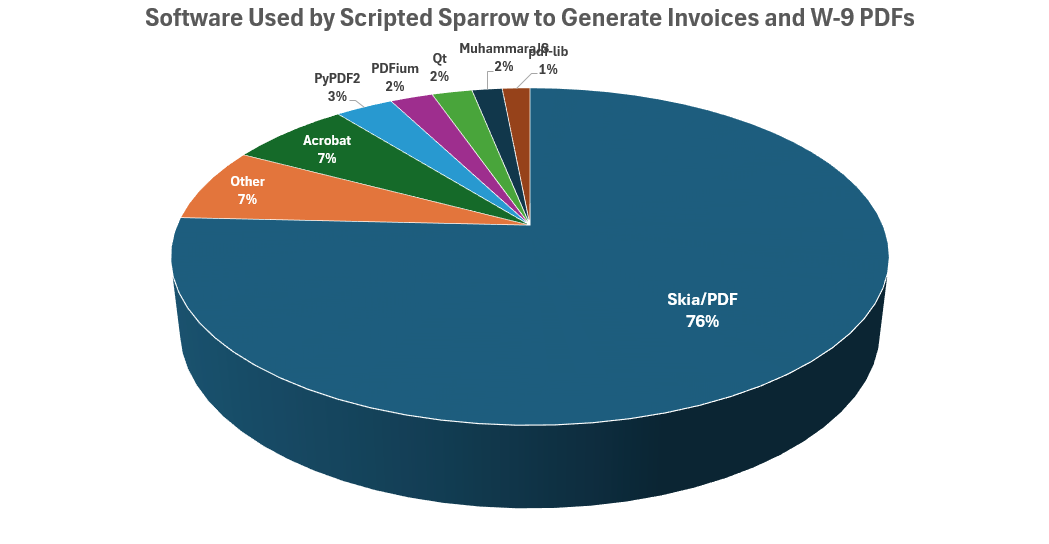
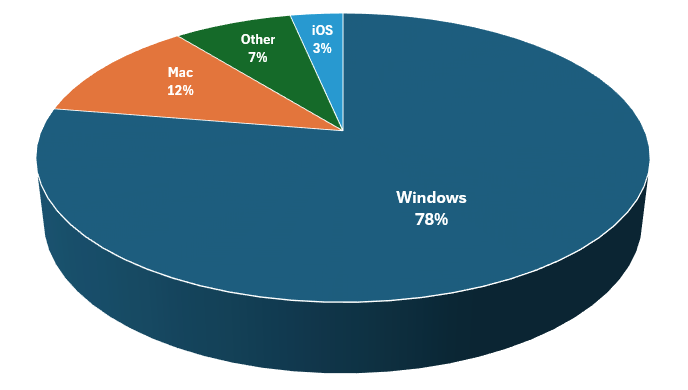
Scripted Sparrow sends their bogus invoices and W-9 forms as PDF message attachments. We were curious to see what tool or tools the group was using to produce these documents, so we extracted the metadata from the PDF attachments. Of the 734 documents we examined, 555, or about 76%, were produced using Skia. The rest were produced by a variety of other tools, as shown in Figure 12.
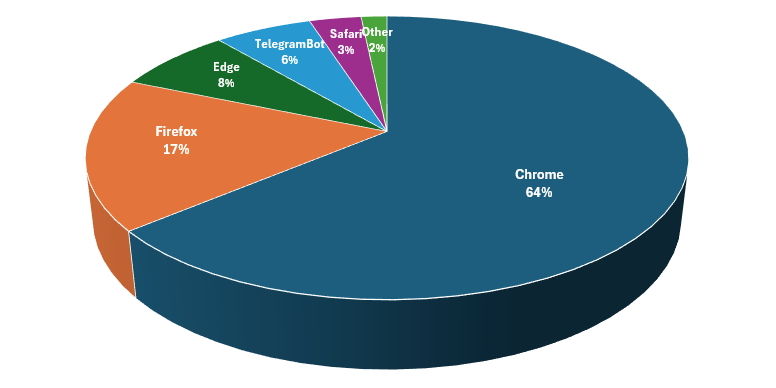
Platforms and Browsers Used by the Group
The Scripted Sparrow group utilizes a combination of webmail addresses as well as addresses on domains that they registered. We also observed a small number of addresses that we believe were likely compromised by the group as well as a single email address that abused Microsoft’s Exchange Online service. Figure 10 provides a breakdown of the type of email infrastructure used by Scripted Sparrow.
Use of Telegram for Communication
While examining the user agent strings we noticed a few dozen entries with the user agent string “TelegramBot (like TwitterBot).” The ASN for these IP addresses was 62041, which belongs to Telegram Messenger. A quick web search revealed what was happening. When a Telegram user posts a link into a chat, Telegram attempts to fetch a preview of the web page from their servers. This is a strong indicator that at least some members of the group use Telegram for communication.
Mapping the Connections
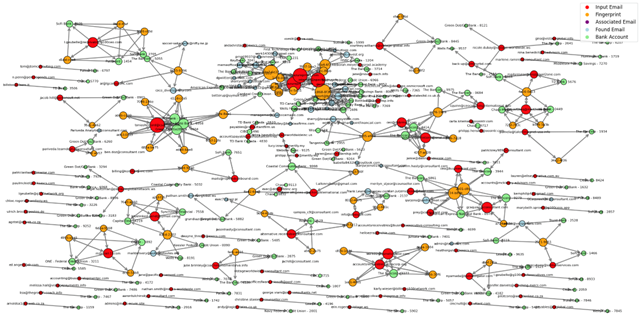
By combining all our intel related to Scripted Sparrow, we were able to map out different clusters within the group based on shared browser fingerprints, bank accounts, and email addresses. The result is shown in Figure 15. The structure of their network suggests the group is a loose collective of fraudsters, all working off the same basic playbook.
Evolution in Tactics
The first few Scripted Sparrow messages we encountered were more generic, using language such as “Dear Customer” rather than the name of the executive who allegedly underwent executive coaching. The spoofed reply-chain in these early messages contained only a single prior message, versus the more recent examples we’ve collected which typically show several back-and-forth messages between the executive and the coaching consultancy before the accounts payable contact was brought into the conversation.
Over time, the group refined their techniques, adding additional customization as well as more natural sounding and complex spoofed reply chains. In some of the more recent engagements, we saw the group pose as both the consultancy as well as the executive, with the executive jumping back into the conversation to state that the “expense is approved.”
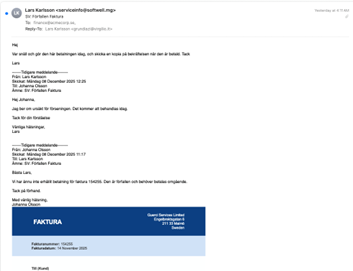
This past week our team observed our first non-English Scripted Sparrow message. This message is shown in Figure 16. The requested amount was only €9,905, which is less than the typical Scripted Sparrow request of just under $50,000 US; however, the invoice was for “Ledarskapscoaching & Managerutveckling” (Leadership Coaching & Manager Development) and the message content included a faked reply chain, both of which are consistent with the group’s activities. We can only surmise that the lower requested amount may be the group’s way of testing a new market for their scam.
We expect the group will continue to refine and expand their tactics over time. If the group is not already leveraging generative AI, it will no doubt soon incorporate the technology into its repertoire.
Conclusions and Recommendations
Scripted Sparrow is a loosely organized collective of fraudsters who utilize social engineering, scripting, and an array of operational security measures to conduct Business Email Compromise on a global scale. Researchers at Fortra have identified 119 domains registered by the group as well as 245 webmail addresses used by the collective. We have identified 256 bank accounts used by Scripted Sparrow to move money out of victims’ bank accounts. The group has members in at least 5 countries spanning 3 continents, and we estimate the group sends upwards of 3 million highly targeted email messages each month.
Organizations should ensure that standard payment approval protocols are followed, regardless of the invoice amount involved. Never trust a reply chain contained in an email from an external source, as this is easily spoofed. Always verify expenses with the employee who allegedly purchased a product or service, and make sure you use the official communication channel(s) for that employee, rather than simply replying to the original message you received.
