What is Cloud Computing?
Over the past decade, cloud adoption has seen explosive growth at both consumer and enterprise level, and it is easy to see why. Cloud-based applications have significantly changed the way we work and share information. Efficient cloud-based computing has transformed IT and security infrastructures making them more flexible, scalable, and cost effective. According to Gartner, cloud-first strategies are a way for organizations to ‘transform, differentiate, and gain competitive advantage’ and many are progressing on their digital transformation journeys.
When moving to the cloud, organizations have several deployment options including:
- Public Cloud where all infrastructure is owned and managed by a cloud service provider such as AWS or Microsoft Azure.
- Private Cloud where a cloud computing network is used exclusively by one organization, either located at an on-site data center, or hosted by a third party.
- Hybrid Cloud where data and applications move between both public and private clouds, allowing organizations to reap the benefits from both environments.
- Multi-Cloud where data and applications move between multiple cloud service providers allowing organizations to deploy the best workload on the right cloud platform.
Protecting Your Cloud Environment
Whichever model an organization chooses, there are security implications to consider. When migrating to the cloud, a key consideration is ensuring that data, systems, and applications are fully protected from cyber threats and unauthorized access. An organization needs to ensure it can apply its security policies to the cloud in a way that's consistent with those applied to on-premises infrastructures. To achieve this, organizations use cloud security solutions and services, which protect data in the cloud and keep the organization compliant with data privacy laws and industry regulations.
What is Cloud Security?
Understanding the ins and outs of cloud data security is critical to protect your infrastructure, data, and brand reputation from the harm a cyberattack can cause.
How Does Cloud Security Work?
It’s key to remember that if you offload data or applications to the cloud with no review of the security settings, you’re essentially outsourcing your security to the cloud provider while retaining all the risk. The cloud provider is responsible for isolating their cloud tenants to ensure resources are separate and cannot be accessed (for public and hybrid cloud models). They also have to secure the virtual infrastructure and technology stack. However, the onus is on your team to ensure your cloud server is properly configured to protect data, platforms, systems, and networks.
Security in the Cloud vs. On-Premises
Cloud security largely functions in the same way as on-premises infrastructure security. You’ll want to pay the same level of attention to both types of environments. Unfortunately, IT professionals are often lured into a false sense of security when it comes to the cloud. They mistakenly think the cloud’s default security settings are more robust than they are. Users are tasked with properly implementing the same security policies for cloud and on-premises environments to protect against emerging threats.
Why Is Cloud Security Important?
When data isn’t properly secured in the cloud, it’s vulnerable to a host of threats. Often, as teams transition off physical deployments and shift workloads and data into the cloud, they assume security is handled automatically. Yet, an operating system in the cloud still has the same vulnerabilities as one down the hall, and it needs the same patches. It’s also important to review logs and run antivirus protection.
What often happens is that even when security policies are properly configured at the start, they can be changed accidentally or intentionally at any time. These changes can go unnoticed for days, weeks, or months. Meanwhile, the information your team thinks is secure is actually accessible by anyone who either stumbles upon it on the public cloud or searches for it with malicious intent.
Threats and Challenges to Cloud Security
Any IT infrastructure is susceptible to cyberattacks, and the cloud is no exception. Organizations need their products, services, and tools to be always available to employees or customers from any location. Downtime can cause major disruption, especially if it impacts essential services such as Office 365, Google Drive, Dropbox, LinkedIn, or Salesforce.
Below are all-too-common mistakes security teams make that can lead to unauthorized access to cloud resources in the forms of distributed denial-of-service attacks (DDoS), account hijacking, and data breaches with exfiltrated information.
Misconfiguration
Improper password management
Weak patch management
Open cloud access points
Not testing security
Shadow IT
Cloud Security Benefits & Solutions
As with most security solutions, cloud security solutions offer more benefits than simple peace of mind. Benefits include:
Visibility
Data security
Compliance
Encryption
Lower costs
Incident detection and response
Cloud Security & Compliance
Many organizations are tasked with securing data and infrastructure in accordance with one or more industry regulations. Achieving compliance requires attention to detail so you’re able to pass audits with flying colors and avoid fines. These requirements apply to on-premises infrastructure as well as your cloud instances.
Below are some of the most common regulations.
Best Practices for Security in the Cloud
Best practices for your cloud data security strategy starts with access. A zero-trust security model is the best framework for user verification, compliance requirements, and more. Native security features included in applications are also worth understanding and taking full advantage of. Finally, data loss prevention functions as a stopgap solution when sensitive data is accessed inappropriately.
Zero Trust
As organizations move to the cloud, incorporating a zero-trust security model is considered best practice. The model works on the premise that no user or device is trusted until verified by multi-factor authentication (MFA) and closely controls and limits who has access to the data. While not 100% effective, the approach minimizes data breaches perpetrated by bad actors both inside and outside the organization.
The zero-trust approach to cybersecurity in the cloud is also effective for compliance with data privacy laws. Cloud-storage can be segmented into small perimeters, each with its own strict authentication measures. This means that if someone does gain entry, they can’t roam undetected or freely access any sensitive data.
Native Security Features
Another best practice consideration is reviewing the native capabilities offered within the online versions of popular services, such as email in Office 365, to establish if they provide sufficient security, protection, and availability.
Data Loss Prevention
Email remains a business-critical function and any continuity issues could cause a major problem. Additionally, when it comes to cloud email security many organizations take a zero-compromise approach to threat protection and data loss prevention (DLP). They often elect to enhance the basic controls with complementary third-party solutions – a best practice approach recommended by security analysts at Gartner.
Using Fortra Cloud Email Protection alongside Office 365 allows organizations to embrace the cloud without sacrificing security or compliance.
Building a Cloud Security Strategy
Like all cybersecurity endeavors, strengthening your cloud security strategy takes time and prioritization. Below are factors to consider:
Understand and Identify
Understand how your team will leverage the cloud and the challenges usage presents. This will help you identify the cloud security solutions needed to minimize the risks and allow you to accelerate your adoption strategies with confidence.
Understand how your team will leverage the cloud and the challenges usage presents. This will help you identify the cloud security solutions needed to minimize the risks and allow you to accelerate your adoption strategies with confidence.
Prioritize
Prioritize the assets and datasets that should exist in the cloud.
Prioritize the assets and datasets that should exist in the cloud.

Assess Data Management Strategy
Reassess your data management strategy to understand where sensitive data resides throughout its lifecycle. A data-centric cloud security approach means focusing not only on the infrastructure but also on the data itself while it’s at rest and in motion.
Reassess your data management strategy to understand where sensitive data resides throughout its lifecycle. A data-centric cloud security approach means focusing not only on the infrastructure but also on the data itself while it’s at rest and in motion.
Review Security Settings
Carefully review default cloud security settings and make updates to bring them in line with your on-premises policies. This includes assessing your security vulnerabilities and implementing controls that deliver ROI.
Carefully review default cloud security settings and make updates to bring them in line with your on-premises policies. This includes assessing your security vulnerabilities and implementing controls that deliver ROI.
Create a Security Policy
Create a security policy that applies to cloud and on-premises infrastructure — and enforce it, including definition of who has access to which resources. Use automation wherever possible.
Create a security policy that applies to cloud and on-premises infrastructure — and enforce it, including definition of who has access to which resources. Use automation wherever possible.
Train Employees
Educate employees on cybersecurity risks with security awareness training.
Educate employees on cybersecurity risks with security awareness training.
Stay Current
Keep up on emerging best practices with the Cloud Security Alliance (CSA).
Keep up on emerging best practices with the Cloud Security Alliance (CSA).
Cloud Security Solutions and the Shared Responsibility Model
Cloud security operates on a shared responsibility model that defines a balance of security responsibilities between the cloud service provider (CSP) and the cloud customer. Generally, the shared responsibility model stipulates that the cloud service provider is responsible for security of the cloud. Customers are responsible for security in the cloud.
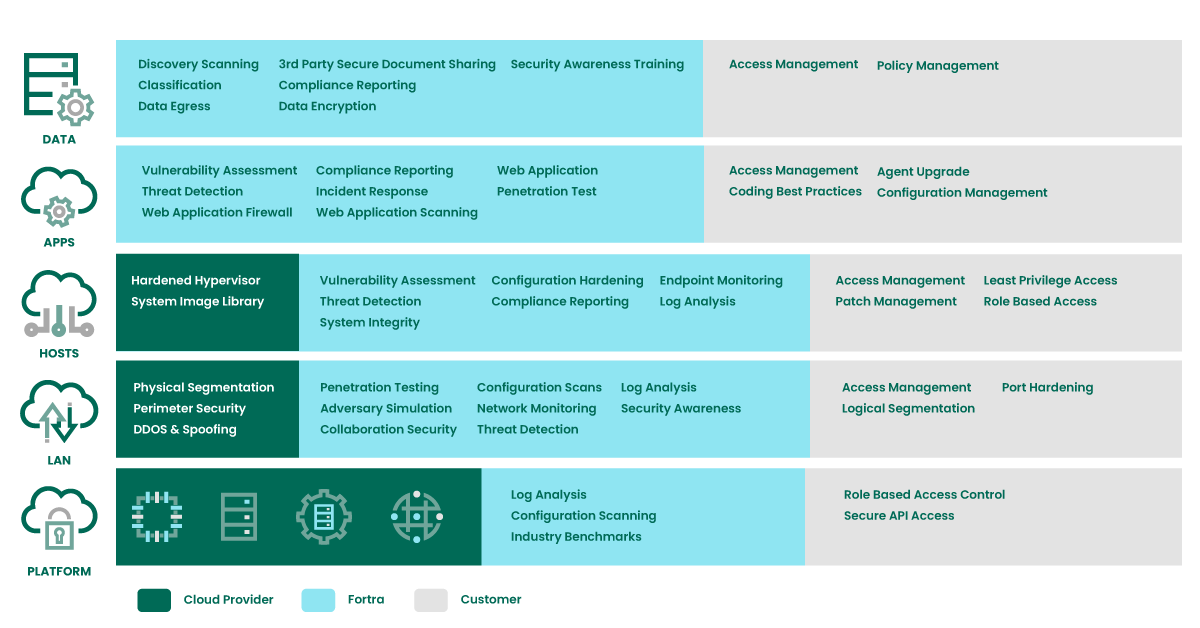
Fortra can help customers secure the cloud across these areas:
Data
LAN
The Future of the Cloud
As with all aspects of technology, cloud computing capabilities continue to grow and change. Fortune Business Insights projects the cloud computing market to grow from nearly $678 billion in 2023 to approximately $2,433 billion by 2030. This growth means expanded opportunities for threat actors to develop clever new methods of exploiting poorly protected cloud infrastructure for financial gain. When it comes to using the cloud effectively to protect the data in its realms, IT teams, cloud providers, and trusted vendors must work together to establish and implement well-thought-out policies to keep data secure.
Contact Us
Fortra experts are available to discuss your cloud security strategy. Let us know how we can help!
Looking for AWS resources?
While AWS provides you with tools to protect your AWS environment, it is still your responsibility to correctly deploy and maintain those security services across your AWS accounts and applications. Fortra can help!