Defining Offensive Security
Offensive security is a proactive process that is imperative in modern cybersecurity. The threat landscape is in constant growth and evolution, meaning penetration testing, red teaming, and vulnerability management have become vital.
An offensive security approach exposes and closes security gaps before a breach ever occurs. An ethical hacker will employ offensive security strategies like penetration testing and red teaming to identify weaknesses using the same exploitation and post-exploitation techniques as threat actors to determine risk and possible damage.
To put it simply, the goal of offensive security is for organizations to emulate the tactics and techniques threat actors use to find security issues within their own systems and to put the defensive measure they have in place to the test.
What is the Difference Between Offensive and Defensive Security?
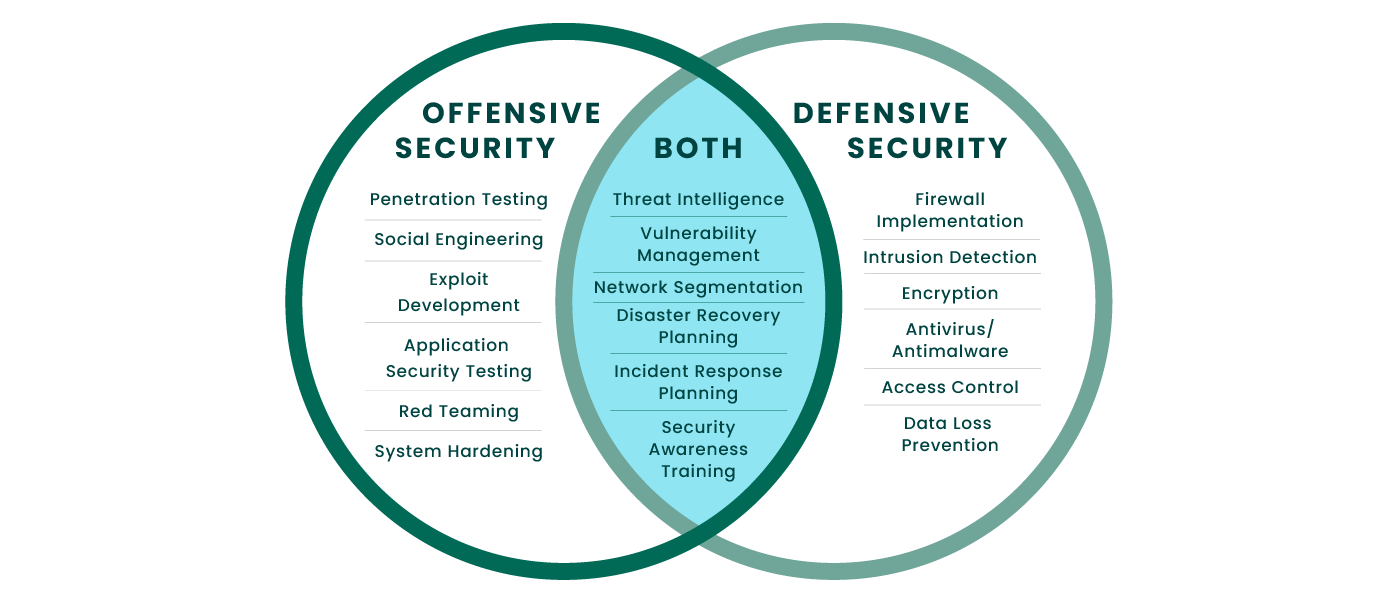
Offensive security focuses on identifying and anticipating attack vectors, determining their exploitability and what assets they put at risk. Pen testing, red teaming and their respective tools are vital components of offensive security, with vulnerability management straddling both the offensive and defensive security worlds.
Defensive security concentrates on detecting, blocking, and containing active attacks. Defense security methods are antivirus, antimalware, firewalls, encryption, and intrusion detection that work to keep attackers out of a system and minimize damage.
When used together, offensive security and defensive security create a comprehensive strategy that ensures your organization is a less attractive target to malicious actors.
Why is an Offensive Security Strategy valuable?
Proactively Reduce Risk
Implementing offensive security greatly reduces the risk of a successful cyberattack. Actively prioritizing vulnerabilities and testing the depth of their weaknesses helps security team's remediate security gaps before they can be exploited.
Build Stronger Defenses
In the cybersecurity realm, nothing is ever static. Discovering new and trending vulnerabilities and attack methods is half the battle. Testing those vulnerabilities can find what sensitive data is accessible and helps your security team bolster your defensive efforts.
Increase Response Time
Practice makes “perfect” and learning the same tactics, techniques, and methodology of a real-world attacker helps reduce attack response time. Offensive security techniques use the same attacks a cybercriminal would use, which helps security teams prevent attacks or anticipate, detect, contain, and respond faster to minimize damage.
Regulatory Compliance Management
Most industries, especially those dealing with sensitive health or financial data, have mandated standards over their cybersecurity measures. Offensive security like penetration testing and red teaming helps organizations meet compliance standards and safeguard consumer data.
Minimize Business Disruptions
Managing your attack surface proactively reduces the likelihood that a cyberattack will be successful. This prevents costly system downtime as well as compliance penalties and reputational damage. The right offensive security portfolio can save your security team valuable time too, improving their efficiency by prioritizing tasks by risk so the team stays focused on what matters most.
Methods of Offensive Security
Penetration Testing
See your security posture through the eyes of an attacker and how far they can go after a vulnerability has been discovered. With penetration testing, security professionals identify potential attack paths and exploit weaknesses, bypassing security efforts and exposing sensitive data. Penetration testers can also develop custom exploits to identify unknown weaknesses unique to a specific organization’s infrastructure. After a successful pen test attempt, reports are generated with detailed information that can help any security team better protect that data and close those security gaps. Retesting can help determine if remediation efforts have worked or if there are additional efforts needed.
Red Teaming
Cyberattacks are rarely immediate or instantaneous. Once an attack path is found, it's exploited, but it can take a malicious actor weeks or months to find what they're looking for. During that time, they silently navigate your inner security system to access sensitive data or business critical systems. These are the same methods red teamers use, only they're on your side. They're employed to simulate how attackers will behave in your network using a variety of methods, including ransomware, phishing, social engineering, or even on-site techniques to test the detection and response capabilities of a security team. The detailed reporting from these engagements helps your blue team strengthen security measures and be better prepared for a real-world attack.
Social Engineering Testing
An organization’s employees are another potential attack vector, as all the technological defenses in the world cannot stop a human from carelessly clicking a malicious link. That’s why testing your employees’ awareness through social engineering is a worthwhile investment. Professional cybersecurity services can put your employees to the test using convincing phishing attempts and other tactics to measure their vulnerability to social engineering attacks and report on the results to inform next steps.
Becoming an Offensive Security Certified Professional (OSCP)
The Offensive Security Certified Professional (OSCP) is an elite penetration testing certificate that is well-respected throughout the cybersecurity community due to the rigor of training required and level of skill needed to attain this credential. Fortra has multiple OSCP professionals on our security team providing their specialized expertise. Additionally, other advanced certifications, such as Certified Information Systems Security Professional (CISSP), Offensive Security Wireless Professional (OSWP), and GIAC Web Application Penetration Tester (GWAPT) are held by other team members, demonstrating the diversity of talent available.
Fortra’s Offensive Security Tools
Fortra’s pen testing and red teaming tools are the gold standard for offensive security tools, including well-known and respected names such as Cobalt Strike, Core Impact, and Outflank Security Tooling.
These tools can be bundled together to create a multi-layered portfolio that advances security maturity and provides full coverage.
Penetration Testing Software
Run advanced pen tests with a centralized solution that offers guided automations, certified exploits, and multi-vector testing capabilities.
Red Teaming Software
Equip your red teamers to run advanced engagements and adversary simulations with the best tools available.
Security Testing Services
Our certified professionals offering penetration testing, red teaming, software security assessments, social engineering assessments, physical security testing, and employee training.
Pricing and Bundles
Contact us to learn more about our offensive security solutions and services.