The Challenge of Cross-Functional Collaboration
Every day, we collaborate with coworkers, partners, and other third-party organizations; and doing so almost always also means sharing data with them. While that may sound relatively harmless, in reality, collaboration can present risks to organizations' data security, be it through over-sharing, inadequate access controls, a lack of data hygiene or security policy enforcement, etc.
This is where the challenge lies: cross-functional collaboration (and the associated data sharing usually involved) is entirely necessary in an increasingly digital workplace, but it also puts organizations' sensitive data at greater risk of a breach. Traditional Information Rights Management (IRM) solutions such as Microsoft Rights Management Services (RMS) can be effective in combating these risks to a certain extent, but their effectiveness often depends on employees willingly incorporating the technology into their daily workflows, let alone applying the proper protections to the data.
In contrast, more modern secure solutions are (in theory) capable of automating necessary security measures, managing access controls as sensitive data moves between parties, and mitigating breaches before the damage can worsen. In short, this means employees can focus on their normal daily tasks and feel safe in the knowledge that their data will remain protected even when it's in the hands of a third party.
What Is Secure Collaboration?
Enter Fortra Secure Collaboration—a modern solution that encrypts sensitive data, applies access controls, and then follows the data as it's shared both internally and externally. Our tool takes a safer, more secure Zero Trust approach to file sharing, meaning nobody is inherently trusted to share, alter, use, or even view your sensitive data until they verify their identity and permissions.
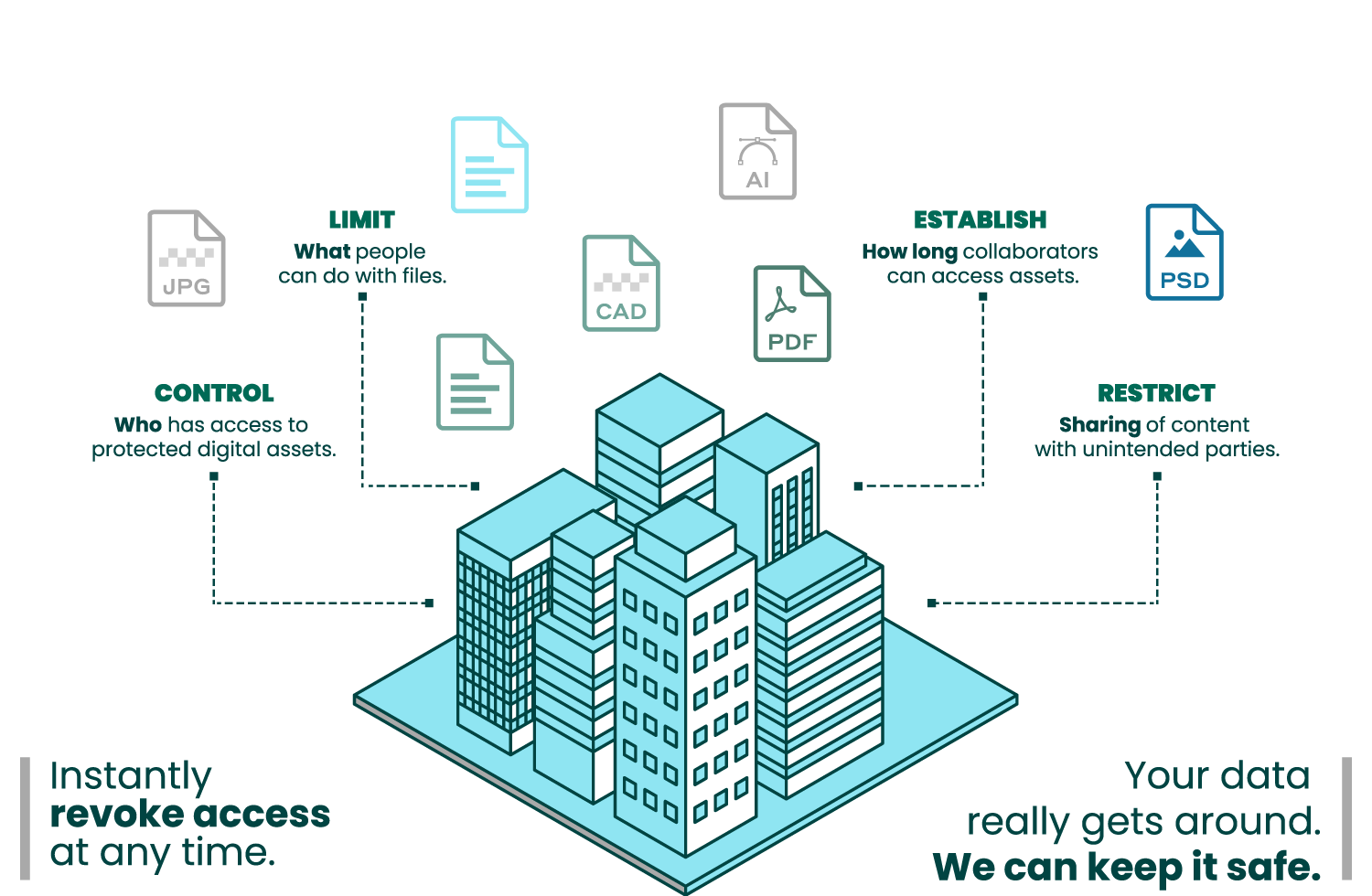
More specifically, Secure Collaboration allows users to maintain granular control over their data, such as:
- When and how a document or content can be accessed or viewed
- How long the document or content can be viewed or accessed
- Who can edit, save, or otherwise modify the content
- Whether a file can be shared or forwarded to a third party
- Which actions can be performed or allowed on the content, like copying, printing, or taking screenshots
- How many times said operations, like printing, are allowed
What Makes Your Organization Unique?
We help protect your advantage.
When organizations are concerned about the data they're sharing, even with trusted parties, it often comes down to concern over the integrity of their intellectual property (IP). Even more than a security tool, secure collaboration is a strategy to protect IP from being stolen, shared, and sold illegally. The strategy can include software, watermarks, and other technologies to limit its unauthorized spread. While the secure collaboration tool itself is undeniably the cornerstone of a greater secure collaboration strategy, an organization's strategy may also include other software, watermarks, and other methods and technologies to limit its unauthorized spread.
With this in mind, however, these security tools and measures cannot come at the expense of business operations. Secure Collaboration also helps to secure the flow of data in and out of document management systems (e.g., SharePoint) and other data repositories, meaning organizations can effectively restrict access to their most sensitive data while still allowing employees to access the data they need from a single, centralized access point.
Limit
Establish
Control
Restrict
Revoke
How Secure Collaboration Can Help
Data classification tools label information so that users within and outside of your organization understand its value and handle it accordingly. Secure Collaboration, when paired with data classification, enables users to collaborate with external partners confidently on their sensitive data, offering their organizations peace of mind in the process.
Data classification benefits Secure Collaboration by:
Enabling policy-based automated encryption based on classification labels
Informing which devices, users, and applications have the permissions to interact with what data
Controlling files in real time according to classification labels
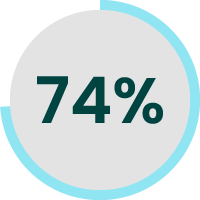
74% of breaches involve the human element.
We give you an "undo" button
Source: Verizon 2022 Data Breach Investigation Report
Secure Collaboration vs. Digital Rights Management
Digital rights management (DRM) grew out of the need to address the explosive growth in piracy after the advent of the internet, especially in the film and music industries. Digitization leads to reduced costs of reproducing copyrighted materials, along with an increase in large-scale distribution of pirated digital assets.
As the world has become more decentralized, the variety of intellectual property and sensitive content needing to be shared online as exploded.
With this increase in collaborative needs, nearly everyone within an organization has a need to collaborate externally. With this, DRM has evolved into secure collaboration, which invokes a more modern and user-friendly approach. Secure collaboration tools put data and content controls into everyone’s hands, typically without the reliance on an organization’s IT team.

Fortra’s Secure Collaboration protects your sensitive files, everywhere they travel.
In today’s highly collaborative, cloud-based and mobile-centric work environment, Fortra's Secure Collaboration provides simple, flexible, transparent data security, enabling businesses of all sizes to protect any file, on any device, anywhere it travels.